
When you’ve worked so hard to build your company and your brand, you can’t afford to let digital security take a back seat. And nor can you afford to let threats prevent you from innovating in a time when businesses of all sizes face constant pressure to adapt to rapid change. Gaining control over information security means more control over the future success of your business.
According to recent research by Kaspersky, the average cost of a security compromise for a small- to medium-size business (SMB) weighs in at US$108,000. Approximately half of this stems from damage to information and infrastructure, the rest resulting from disruption to normal operations.
If you’re a business owner, that’s a statistic you can’t afford to ignore. Not only can the costs of a cybersecurity incident be catastrophic – they’re often notoriously difficult to quantify. On top of the more obvious and direct costs, you also have to factor in brand damage which could have deeper consequences. For example, 60 percent of businesses close within six months following a major attack.
Why should business owners care about cybersecurity?
According to Kaspersky’s Andrey Dankevich:
Smaller companies may not have cybersecurity among their top priorities. However, the cost for overlooking the problem will only grow. Why? Because malware doesn’t distinguish between its victims, and because even very small organizations have something to lose.
Andrey Dankevich
Solution Business Lead, Kaspersky
Many business owners may think they aren’t attractive targets, and that it’s not worth investing significant financial, human and technical resources into bolstering defenses. The belief is that cybercriminals would rather go after big targets, which is little surprise as its data breaches from brands like Yahoo! and Marriott that tend to make the headlines.
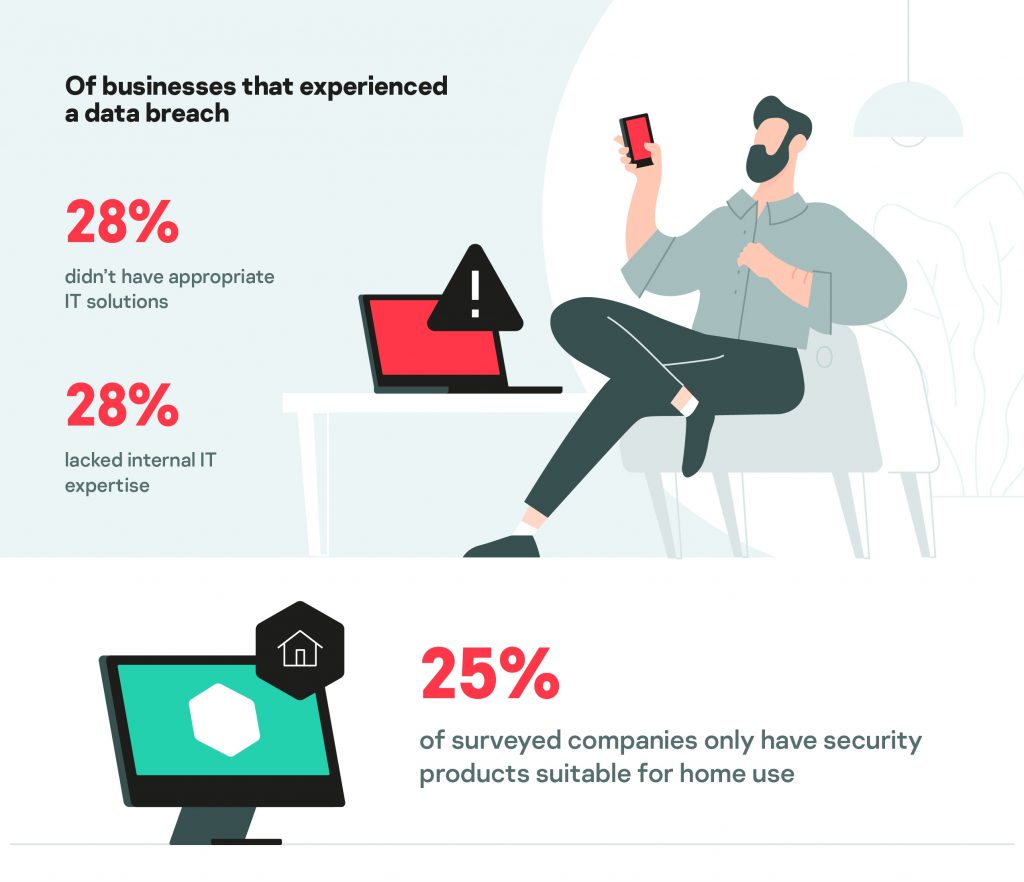
But big businesses are more likely to have cutting-edge security measures in place, or at least that’s the common thinking among cybercriminals. They’re perceived as being lucrative but extremely challenging targets. Most cybercriminals are opportunists. Instead of targeting big enterprises, they go after easy money – some 36 percent of small businesses have suffered a data breach. What’s more, around a quarter of companies only use consumer-grade products to protect themselves, and of those who have had breaches, more than one in four don’t have appropriate IT solutions or internal expertise.
Every organization, no matter its size or industry, has something that cybercriminals want. That might include payment data, personally identifiable information or intellectual property, to name a few. Small businesses are collecting more valuable data than ever before, so they’re becoming even more attractive targets. At the same time, their cybersecurity infrastructure is often lacking – smaller business may have no IT specialists on site and rely on managed service providers (MSPs), or even just basic consumer tech know-how to get by. With the lack of infrastructure and expertise necessary to protect the so-called crown jewels (your most valuable data), attackers have many avenues to exploit.
On a brighter note, it’s possible to build a robust small business cybersecurity infrastructure without having to choose between breaking the bank and jeopardizing your efforts to innovate.
Strong cybersecurity begins and ends with people
Information security is commonly perceived as a technical challenge. Ask almost any office employee, “Who in the business is responsible for cybersecurity?” and they’ll probably point at the folks in IT. Or, if there isn’t a dedicated IT team, they’ll likely point to management. The truth is, regardless of company culture, cybersecurity is everyone’s responsibility. That’s because it’s largely a human problem rather than a technological one – around 90 percent of cyberattacks involve a human element.
Cybercriminals prey on human error, simply because it’s far easier than exploiting technology. For example, it’s much easier for an attacker to manipulate someone into giving away login credentials than to break encryption or use a brute-force attack which could theoretically take longer than the projected lifespan of the universe. In fact, most cybercriminals don’t know any more about the inner workings of technology than the average layperson. Instead, they rely on social engineering tactics and malware-as-a-service (often purchased on the dark web) where cybercriminals recruit others as affiliates, in many ways mirroring the processes used by legitimate businesses.
The only real way to mitigate human error is to ensure your employees are at least as aware of the cybersecurity landscape as those who would exploit it. While you can’t expect people in accounts or HR to understand the complexities of things like encryption and security protocols, you can train them to better recognize social engineering threats like phishing emails and common security risks like weak passwords. Everyone must be included in an ongoing and interactive security awareness training program that prepares people for the risks. You won’t just be doing your business a favor – you’ll be helping everyone who works for you to stay safe in their personal lives too.
Protect your perimeter
Perimeter defense is the basic, foundational level of protection. Analogous to the walls of a medieval castle, its sole purpose is to keep the bad stuff out and the valuable stuff in. One of the biggest challenges is establishing where the perimeter exists in the first place. It’s not just about protecting internal networks with firewalls and antivirus software like it used to be. Far from data systems being restricted to in-house servers and workstations, business leaders now need to think about mobile devices being used for work (including those owned by employees) and cloud-hosted resources.
But conventional perimeter defense is no longer enough. The amount of data in your care typically extends far beyond the physical boundaries of your premises. That’s why protecting your online accounts must be a top priority. Hardware is becoming increasingly meaningless in small business environments, which are transitioning to cloud computing and managed services. All of these devices, known as endpoints, need to be protected.
Getting protected is not as daunting as it may at first seem. To complement in-house IT managers or replace them, small businesses often partner with managed service providers (MSPs) who can offer a suite of security services to meet your needs including managing antivirus software, installing firewalls and protecting email from malicious content.
How layered security helps protect the crown jewels
Back to the castle analogy, there’s more than mere walls protecting what’s inside. Many castles are built on hills to provide a defensive advantage. Others have moats or ditches to offer an additional layer of defense. And, even if an attacking army does get through the walls, there’s usually a garrison to provide a last line of defense. The same methodology applies to information security, where perimeter defense is simply the first barrier serving to stop attackers from getting into the system. But if that’s all there is, it’s a single point of failure which leaves your business extremely vulnerable.
Multilayered security is based on the concept of using multiple security solutions together to guard the crown jewels – your highly valuable and sensitive data. For example, a firewall helps prevent malicious code from reaching your network, antivirus software protects each individual device connected to the network, and encryption protects data both in storage and when it’s being sent across the internet.
These are all technical and administrative controls, both of which are relatively easy and cheap to implement given that they’re now standard with many business-grade IT systems.
But, while they do help protect your business, they’re not a substitute for training and expertise.
Adding value with better information security
It’s time for business owners to take information security seriously, but that doesn’t mean it should become a burden on resources or a blocker of innovation. Rather, it can add value to your business in a time when customers consider data privacy and security to be top priorities when choosing which organizations to do business with. With a combination of the right policies and cutting-edge technology, you can bring your business closer to achieving immunity from cyber-threats.




