Cloud threat intel: Kaspersky Security Network (KSN)
The Kaspersky Security Network (KSN) is a complex distributed infrastructure developed by Kaspersky Lab and dedicated to intelligently processing cybersecurity-related data streams from millions of voluntary participants around the world. By analyzing these data streams automatically in the cloud, the system ensures the fastest reaction times to new and yet unknown cyberthreats and the maintenance of the highest levels of protection for every partner or customer. It is one of the most important components of Kaspersky Lab’s multi-layered, next generation approach to protection which combines expert analysis, machine learning algorithms and big data, allowing us to spot patterns, changes and new threats in the cyber landscape – with skill and accuracy.
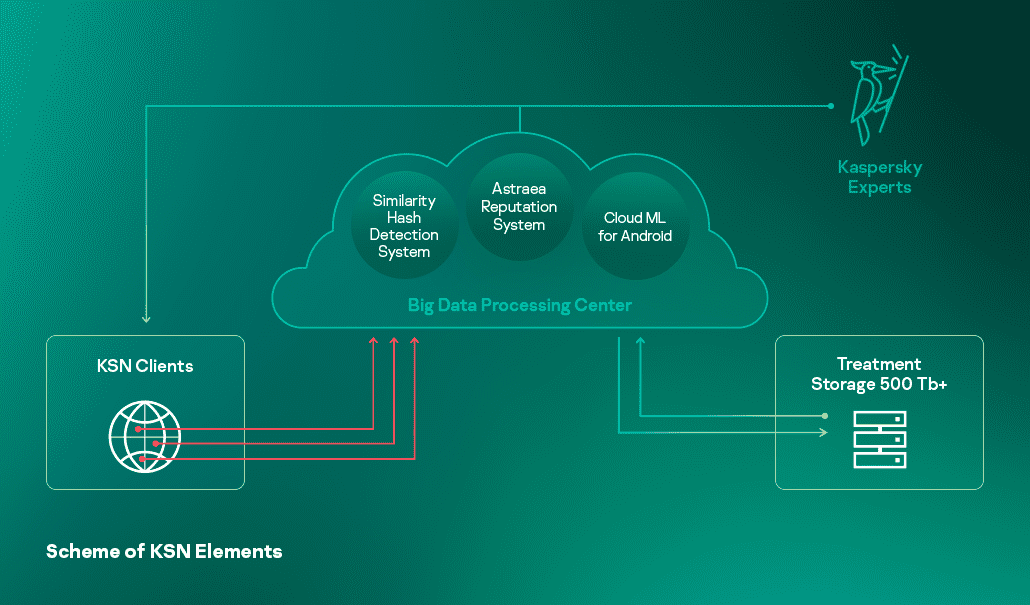
The scheme above illustrates the basic elements of KSN including:
- Astraea Reputation System. The system aggregates all the statistics with meta-information about suspicious objects worldwide in real-time. Following the analysis, the object’s reputation is calculated. Detection decisions towards malicious objects become immediately available to all users through KSN. If Astraea has no sufficient information about the object to make a verdict by the moment, the rating will be recalculated later after extra information is collected.
- Similarity Hash Detection System, a ML-based technology to detect malware variations. The cloud component of the system collects multiple file features from different sources including in-lab automatic systems of malware processing. Then a machine learning approach is used to find the features common to the whole group of similar malicious files. Based on these features, Similarity Hashes (SH) are calculated and published through KSN. The endpoint product extracts a file’s features at the endpoint, calculates its SH and checks it through both local and cloud SH databases. This approach allows Kaspersky Lab products to detect whole families of quickly changing polymorphic malware.
- Cloud ML for Android for mobile threats detection. In this system, the predictive model takes the form of a Decision Tree Ensemble. This type of powerful ML model trained on millions of samples can detect malware with high accuracy but it requires lots of resources to run which would be hard to get on mobile device. This is where we benefit from the cloud approach. First, the agent on a user’s device collects multiple features of an Android application - its entry points, permissions, etc. - to get the most accurate description of the app (no sensitive user data is collected). This data vector is sent to the KSN cloud where it is passed through the Cloud ML for Android model, and its classification decision is immediately sent back to the mobile device.
The KSN approach provides the following benefits for final security level of customers’ systems and their data:
- Detection of advanced and previously unknown malware
- Reduction of detection errors (False Positives)
- Significant reduction of response time to new threats - in contrast to traditional signature-based responses from hours to seconds or minutes.
The basic principles of KSN data protection
- Information processed is limited to that needed in order to improve detection algorithms, refine the products’ operation and offer better solutions to our customers;
- The information processed is received from customers who have accepted an EndUser License Agreement (EULA) and KSN agreement where the kind of information obtained is described in full;
- Participation in the KSN agreement can be opted in or out of, at any time, in the solution settings;
- The data received by KSN is not attributed to a specific individual. The information is used in the form of aggregated statistics, on separated servers with strict policies regarding access rights;
- The information shared is protected, even during transit in accordance with legal requirements and stringent industry standards, including through encryption, digital certificates, firewalls and more.


