Endpoint Detection and Response
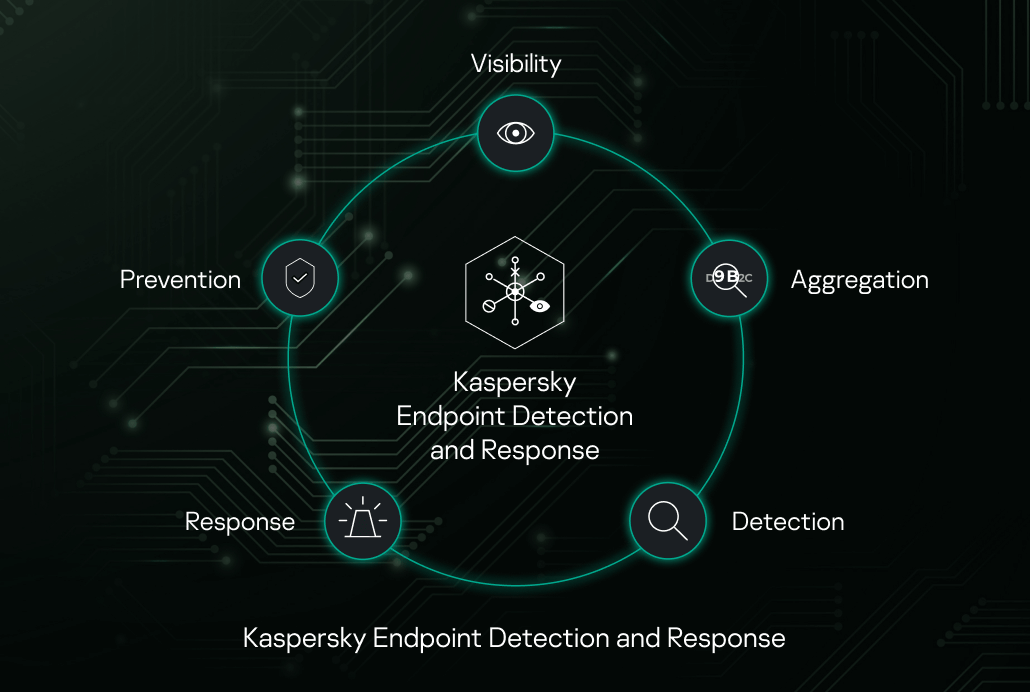
Kaspersky EDR is a cybersecurity solution for the protection of corporate IT systems. It adds endpoint detection and response (EDR) capacities to IT security:
- Extract patterns of elaborate attacks, automatically and manually, from events on many hosts.
- Respond to attacks by blocking their progress.
- Prevent future attacks.
The need for EDR
Not long ago, a typical cyberattack would use mass malware. It would target separate endpoints and detonate within single computers. Mass malware attacks are automatic, they pick out random victims via mass emails, phishing websites, rogue Wi-Fi hotspots etc. The remedy was endpoint protection solutions (EPP), which would protect hosts from mass malware.
Facing the effective EPP-based detection, attackers switched to the more costly, but more effective, tactic of launching targeted attacks against particular victims. Due to high cost, targeted attacks are usually used against companies, with the aim of getting profit. Targeted attacks involve reconnaissance and are designed for penetrating the victim’s IT system and evading its protection. The attack kill chain involves many hosts of the IT system.
Due to the high variety of methods and their human-led, interactive nature, targeted attacks can evade EPP-based security:
- EPPs rely on what they see on a single endpoint. But advanced attacks act on many hosts, making relatively unsuspicious actions on yet another endpoint. Even if host EPPs detect some of these actions, the attackers eventually build a multi-host kill chain. Traces of such attacks are scattered about many hosts.
- As EPP verdict is automatic, the attackers can verify that their attack is not detected by victim’s EPP or other automatic security solutions. Attackers keep whole farms of antimalware just for this case.
- Vendors cannot increase protection by just making EPP solutions more “paranoid” due to risk of false positives. So even when something ambiguous is happening on a host that could be a part of a kill chain as well as a legit action, EPP is designed not to interfere.
To address targeted attacks, cybersecurity vendors extend EPP solutions with endpoint detection and response (EDR) features:
- Providing centralized visibility of events on many hosts for their manual and automatic correlation
- Providing security staff with sufficient data about events
- Creating tools for response and remediation, thus countering human-led attacks with human-led cyberdefense
In essence, EDR adds new layers of endpoint protection against advanced attacks.
Kaspersky EDR’s input into security
Kaspersky EDR adds protection power to an existing EPP solution. EPP specializes on simpler mass attacks (viruses, Trojans etc), while the EDR concentrates on advanced attacks. With this solution, analytics view malware activity as well as events with legit software in the context of an attack, uncovering the whole kill chain.
Kaspersky EDR is fully integrated with Kaspersky Enterprise Security EPP, and it can work with EPP solutions of other vendors. The EDR adds the following:
- Multi-host event visibility: aggregation of attack traces scattered around the IT system
- Detection with “heavy” methods, which require much computation power unavailable for regular user endpoints due to possible effect on regular user workflow: advanced pre-processing, sandbox, heavy machine learning models, including deep learning, and others. Heavy methods provide better-quality detection
- Expert tools for incident investigation, proactive threat hunting and attack response
Kaspersky EDR design
Elements
- Endpoint sensor: integrated with Kaspersky Endpoint Security in one-agent or standalone (for deployment with other EPP solutions)
- On-premise servers (event storage; analytic engine; management module; optionally—a sandbox).On-premise location keeps the event data in full control of the customer
- The KSN cloud or KPSN private cloud for detection enrichment in real time and prompt reaction to new threats
EDR as part of Kaspersky Threat Management and Defense
Kaspersky EDR, Kaspersky Anti Targeted Attack platform and Kaspersky Cybersecurity Service (KCS) make up a suit for advanced protection and threat intelligence:
- Kaspersky Anti Targeted Attack Platform adds network-, web- and mail-based detection, extending the solution’s scope of targeted attack detection to “endpoint+network” level.
- KCS adds expert support for customer IT security team: training, providing threat intelligence data, security operation center (SOC) management by Kaspersky Lab and other options.
Integration with Security information and event management (SIEM) systems
You can integrate our EDR with 3rd party SIEM systems (detect data is exported in common event format, CEF).
Features
Continuous centralized event aggregation and visibility. The EDR aggregates events from hosts in real time:
- The EDR aggregates events continuously, regardless of their cause and suspiciousness. This makes EDR more effective against unknown malware. We could design it to aggregate only suspicious or malware events and thus save disk space on the central node (as some other EDR solutions do). But then legit actions of attackers with stolen credentials would not be logged, and new unrecognized threats won’t trigger logging as well.
- The EDR central node uploads events feed from hosts to its storage on the central node. Some other vendors’ EDRs store events right on hosts. When the central node needs data about events, it requests log info from hosts. This design saves disk space on the central node, but makes search slower and connection-dependent, with host visibility depending on host’s availability in the network.
Automatic detection. Threats visible in the scope of a single host are detected by Kaspersky Endpoint Security with heuristic, behavioral and cloud detection (or with another EPP host application). Above this, the EDR adds layers of detection with a multi-host scope, based on correlation of events feed from multiple hosts.
Apart from event-based detection, EDR host agents automatically send suspicious objects or parts of memory to the central node for a deeper analysis with algorithms unavailable for regular host computation power, including heavy pre-processing, heuristics and machine learning algorithms, sandbox, extended cloud detection, detection based on Kaspersky Lab’s threat data feed, custom detection rules (Yara).
Manual detection, or threat hunting, is the proactive search by an operator for traces of attacks and threats. The EDR lets you “hunt” through the whole history of events from many hosts, aggregated in the storage:
- You can search through the storage for traces of attacks and suspicious events and link them together to reconstruct the potential kill chain. Search queries in the database support compound filters (by hosts, detection technology, time, verdict, severity level etc).
- You can upload new IOCs to the EDR and detect earlier undetected persisting threats.
- You can manually send suspicious objects for deeper analysis by “heavy” detection methods.
- If the company has enabled the KL TIP service (Kaspersky Lab Threat intelligence platform), you can request information about objects in threat database.
Response is actions that an operator can take when they detect a threat. These actions include:
- Incident investigation, reconstructing events in the kill chain.
- Remote operations on the host, including process kill, deleting or quarantining files, running programs and other actions.
- Containment of the detected threat by hash-based deny of object execution.
- The rollback of changes on hosts caused by malware activity relies on the EPP solution. For example, Kaspersky Endpoint Security undoes such malware actions.
Prevention is the policies that restrict object activities on endpoints:
- Hash-based execution deny policies prevent running particular files (PE, scripts, office documents, PDF) throughout the whole IT system let you prevent attacks currently spreading around the world.
- Automatic detection of objects or URLs on hosts, which have been previously detected in a sandbox as malware.
- Application execution control (allowlisting, startup control, privilege control), policies of network access, USB drive access and others rely on the EPP solution. Kaspersky Endpoint Security EPP provides all these prevention features.
Management of Kaspersky EDR is role-based and provides workflow management: alert assignment, tracing alert status, logging alert processing. Email notifications are flexibly configured according to alert types and their combos (detect type, severity etc).
Use case: uncovering the kill chain
EDR host agents routinely send events to the in-house EDR server.
- One of events received on the server is associated with execution of a file with unique occurrence in the corporate IT system (judging by its hash). The file has other suspicious traits as well.
- The server triggers deeper investigation. It downloads the file itself for the automatized analysis by EDR analytical engines. The file is queued for automatic analytic procedures.
- The sandbox detects file behavior as malware and alerts the operator.
- The operator initiates manual investigation and checks the events possibly associated with the infection:
a. With standard administrator tools, finds that the infected machines had been accessed from a corporate web server, which is available from the Internet. Finds suspicious files and processes being executed on the server, creation of suspicious executables. Eventually, finds a web shell that attackers uploaded via a vulnerability on the server’s web site.
b. Identifies all command and control (C&C) servers for this attack. - The operator responds to the attack:
a. Blocks all detected C&Cs.
b. Kills malicious processes.
c. Blocks execution of malware files by their hashes.
d. Quarantines malware and suspicious files for later investigation.



