Application Control and HIPS
Traditional protection from cyberattacks is based on malware detection that checks any application against databases of known malware indicators before it's executed. In Kaspersky Lab products, this basic layer of threat protection in represented by KSN cloud detection, ML malware classification, Anti-Rootkit and other anti-malware technologies.
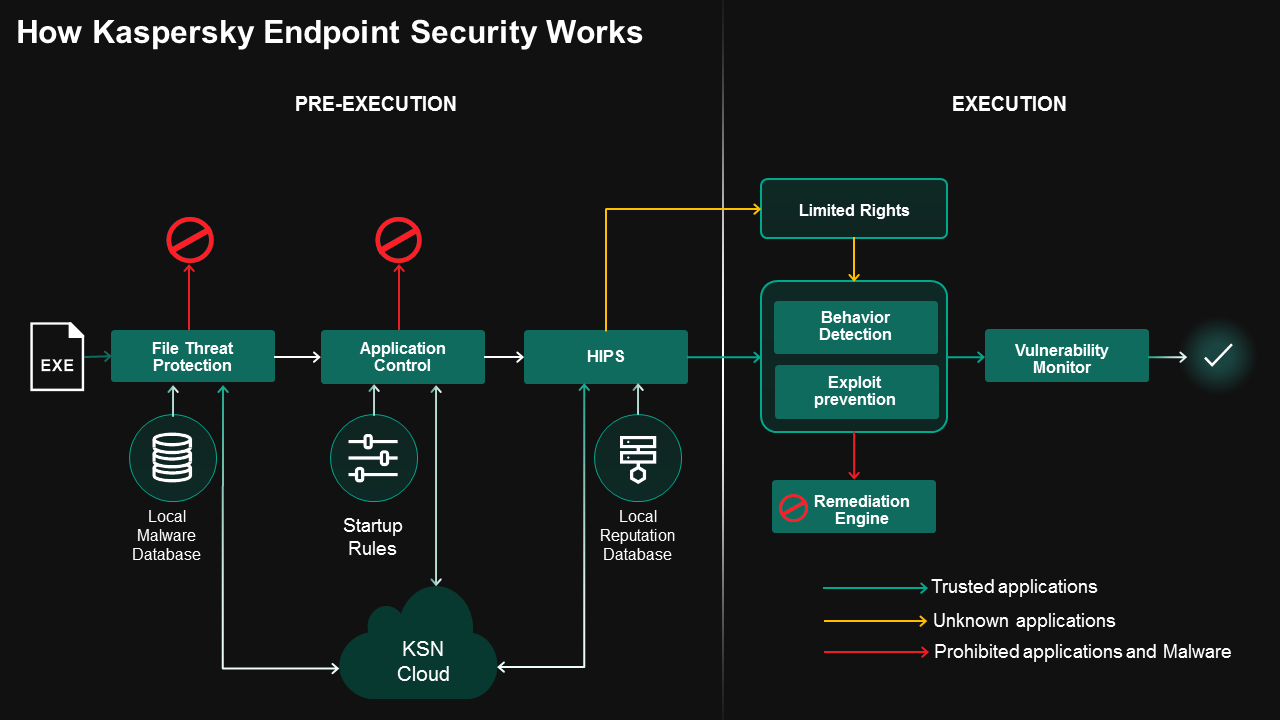
Another effective approach is to “enforce hygiene” of the attacked systems - even unknown threats could be blocked by hardening application access to critical system resources. Our main examples of resource-focused protection techniques are Application Control that either allows or blocks file execution according to local allowlisting / denylisting rules, and Host Intrusion Prevention System (HIPS) that limits application access to host resources (data, registry keys, process memory etc) based on application reputation.
To complete Kaspersky Lab's multi-layer endpoint security picture, we should also mention some next-layer execution control technologies: Behavior Detection, Exploit Prevention, Remediation Engine and Vulnerability Monitor, which are to be described in other TechnoWiki articles.
Trust categories
In Kaspersky Lab solutions, resource protection is based on assigning applications to trust categories and defining each category’s allowed operations, including:
- Attribution of applications to trust categories.
- Rule-based control of applications’ ability to start and to interact with other processes, data, network etc.
- Application monitoring , with privilege downgrading as soon as an application shows malicious activity: attempts to control other applications, change registry entries etc.
- Protected boot , which provides trust to application attribution, control and monitoring.
Application privileges are defined by the trust category it falls into. Applications are automatically inventoried on a host and assigned to trust categories. In Kaspersky Endpoint Security for Business (KESB), application lists are delivered to administrators from user computers – enabling them to develop their own application control policies.
Application attribution to a trust category is based on its behavior, as assessed by the antimalware engine, reputation in KSN, electronic signature and application integrity check. Applications are assessed on first launch or in a group, following the installation of the anti-malware solution on the host.
The trust categories are:
- Trusted applications: OS applications (svchost, smss and others), legitimate applications from known vendors, with verified signature and integrity.
- Untrusted applications : malware, which is blocked even from starting.
- Unknown applications : restricted, depending on their nature. For example, applications recognized as adware (which are still not malware) are allowed to run, but not to inject code into other processes. Applications that don’t show malicious activities but lack a signature will have broader privileges.
After initial categorization, applications continue to be monitored by the antimalware solution. If they display malware traits, they are downgraded to a lower trust category, and their privileges are restricted. Application reputation is periodically re-confirmed via KSN, just in case its reputation has been recently downgraded in the cloud.
Operations of applications that do not fall into the “Trusted” category are logged by the Remediation Engine. If an application turns out to be malware, the engine rolls back the changes it made.
Application Control
An application’s ability to start is defined by its trust category.
In Kaspersky Internet Security (for home users), users can fine-tune application blocking on their host and choose its mode:
- In automatic mode, untrusted applications are automatically blocked (Denylist).
- In Default Deny mode (Allowlists), only trusted applications are started (PE32-files, .Net-executables, installers and some other formats). Other applications are blocked permanently, including during reboot and OS update.
- In manual mode, users can, at first launch, decide whether or not to block a particular application.
In Kaspersky Endpoint Security for Business, administrators can configure startup blocking policies for applications, executable modules (PE-files, exe, scr, dll) and scripts executed via a variety of interpreters (com, bat, cmd, ps1, vbs, js, msi, msp, mst, ocx, appx, reg, jar, mmc, hta, sys). For this, the administrator inventories applications on user computers and receives their list with metadata (vendor, certificate, name, version, installation path etc.) If new applications appear on hosts later, these are also inventoried.
Applications are automatically grouped into hierarchical categories (for example, games, office applications, browsers). Categories help administrators to create groups of application startup policies. For user groups, administrators can block the startup of specific applications, application categories or applications that fall under certain conditions (e.g. with a low KSN cloud rating).
Application Control also provides several tools to simplify the initial configuration of allowlists rules, including a wizard to create rules based on inventory results, pre-defined rules recommended by Kaspersky Lab and dynamically updated allowlists rules based on Trusted Sources (file locations or reference computers).
Users can request administrator permission to start an application, via their KESB interface.
To avoid blocking a legitimate application, administrators can enable a blocking rule in test mode. Test rules don’t affect application startup, but administrators are notified of any triggers, enabling them to identify unwanted application startup blocks and to test proposed rules - or even the complete startup control feature - on their network.
HIPS
In addition to controlling its’ ability to start, the application’s trust category defines its privileges: i.e. what an application can do in the host system. Privilege control is rule-based, with a pre-defined set of “out of the box” rules that can be modified by home users or a business solution’s administrator.
For each trust category, rules define an application’s ability to:
- Modify files, registry keys (read, write, create, delete)
- Establish network connections
- Access web camera and microphone (stricter rules are applied here even for trusted applications)
- Execute system operations, e.g. open process, windows shutdown. It is important to control system operations, because malware can use them to interfere with other processes’ memory, inject code or interfere with OS operation.
Each rule defines the application categories it affects, the action that it controls and its verdict: “allow” or “deny”. In the home user solution, the verdict can also be “ask user” - the user is prompted to make the decision, and such decisions are cached.
Secured container
Using a special set of HIPS rules, any process could run in a secured container: access to this process is very limited, even for trusted applications. Additional restrictions provide screenshot blocking, clipboard protection and integrity control that protects the process from malicious injections. This way, all the application’s internal data (including user’s personal data) is kept safe. This HIPS technique is core to Safe Money (Safe Browser) mode.
OS boot protection
At OS boot, all untrusted applications are completely blocked, and the rest are restricted (for instance, their network access is blocked). This reduces the possibility of an attack during computer boot.

The protection technologies of...