Beware: hundreds of thousands of websites are fakes. They’re made to look like the sites of popular online stores, banks, and delivery services, but with just one purpose: to steal your passwords and financial data. Victims are lured to such sites by phishing emails, messenger chats, and even paid ads. But don’t despair: even if you click on a bogus link, it might still be possible to escape the scammers’ clutches without loss. As long as you spot the fake in time…
Where do phishing sites get hosted?
Sometimes scammers create a special new website and register a name for it that resembles the original (for example, netflik.com instead of netflix.com). Our separate post on fake names is worth checking out. But such sites are expensive to make and easy to block, so many cybercriminals take a different route. They hack legitimate sites of any kind, then create their own subsections where they publish phishing pages. It’s very often SMBs that fall victim to such hacks because they lack the resources to constantly update and monitor their websites. Sometimes a site hack can go unnoticed for years, which is a godsend for cybercriminals.
One of the most popular web content management systems is WordPress, and the number of hacked sites on the platform runs into the tens of thousands. However, once you know what to look for, it’s not hard to detect such sites yourself.
First sign of fakery: mismatch between site name and address
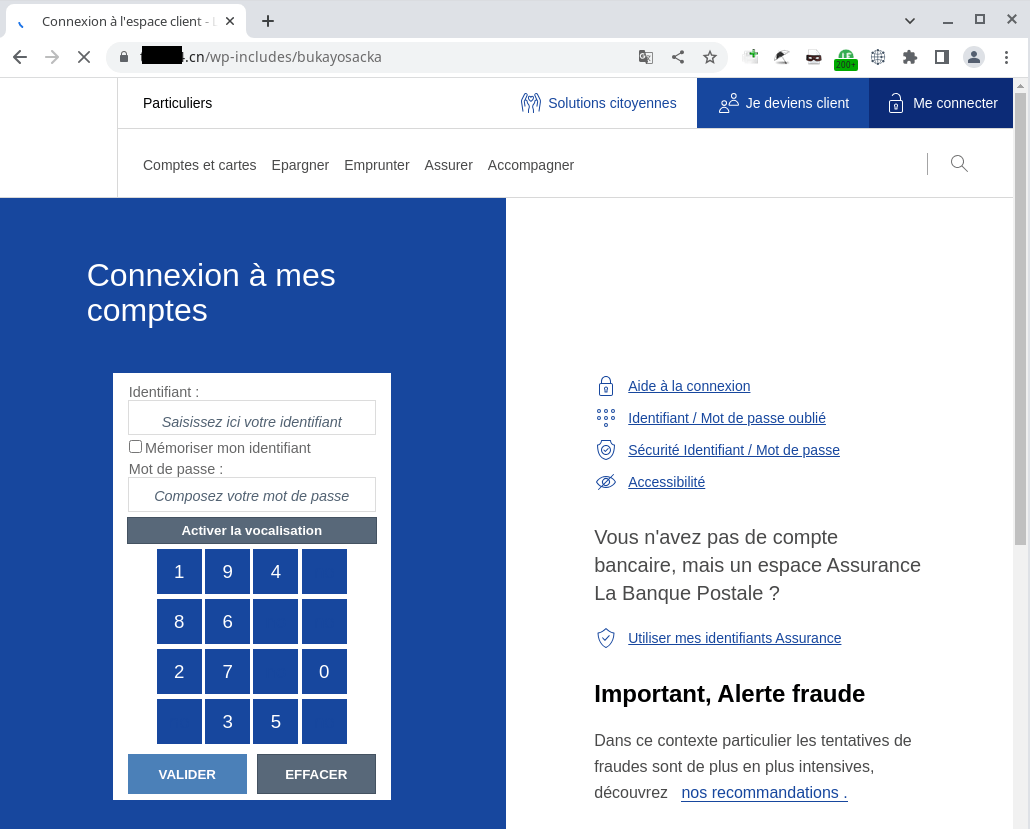
When following a link in an email, a social media post, or an ad, it pays to take a look at the URL of the site you land on. If it’s a hacked site, the discrepancy will be staring you in the face. The name of the service the fake site pretends to be might crop up somewhere in the directory path, but the domain name will be completely different; for example: www.medical-helpers24.dmn/wp-admin/js/js/Netflix/home/login.php. You know perfectly well that Netflix lives at netflix.com, so what’s it doing on medical-helpers24?
Checking the URL requires a little more effort on mobile devices because many apps open links in such a way that the site address isn’t visible or is only partially visible. In this case, click on the address bar in your browser to see the site’s full address.
Second sign of fakery: directory path elements
When looking at the full address of a web page, pay attention to the tail of the URL after the domain name. It might be rather long, but just focus on the first parts. Hacked subsections of a site are usually hidden deep within WordPress service directories, so the address will most likely contain elements like /wp-content/, /wp-admin/ or /wp-includes/.
In our example, www.medical-helpers24.dmn/wp-admin/js/js/Netflix/home/login.php, one such element comes right after the domain name, confirming our suspicions that the site has been compromised.
Chances are that the URL will end in .php. Pages with the .php extension are quite common, and this in itself is not a sign of hacking. But in combination with this directory path, the .php extension is compelling evidence of guilt.
Third sign of fakery: the site has a different subject
If the site name seems unfamiliar or suspicious, you can perform an additional check by going to the home page. To do that, delete the URL tail, leaving only the domain name. And this may open the page of the real owner of the site, which will be totally unlike the phishing page both in subject and design. It might even be in a different language, as in the example below:
Your personal data on a fake website
It might happen that some information fields (such as your email address or bank card number) are correctly pre-filled even on a phishing site. This means that the attackers have somehow gotten hold of a database of stolen personal data and are seeking to enrich it with additional information, such as passwords and CVV numbers. To this end, they post a table with known data on the victims, and this can often be freely downloaded from the site. So, if you see your real card number on a fake site, have the card reissued straight away, then think about additional security measures for other personal data. For example, if your email has been leaked, protect your email login with a stronger password and be sure to enable two-factor authentication.
How to guard against phishing
- Be vigilant. For the above tips to work, remember to check every link you click on.
- Check links before you click on them — some attacks don’t require the victim to do anything but land on an infected site. On your computer, you can hover over a link to show the URL it will take you to. On your phone, tap and hold the link with your finger to see the URL in the pop-up menu.
- Important addresses (your bank, email server, etc.) are best accessed through bookmarks or typing them manually, not through links in emails.
- Install security solutions on all computers, tablets, and phones. Phishing can get you on any device, so use Kaspersky Premium to keep all your digital companions secure.
 phishing
phishing


 Tips
Tips