Woburn, MA – September 15, 2022 – Kaspersky researchers have spotted an unusual malicious bundle targeting gamers on YouTube. Its main payload is the widespread RedLine stealer, one of the most common Trojans used to steal passwords and credentials from browsers. A bundle is a collection of malicious programs distributed in the form of a single installation file, self-extracting archive or other file with installer-type functionality.
Cybercriminals actively hunt for gaming accounts and gaming computer resources. As Kaspersky experts noted in the recent overview of gaming-related cyberthreats, stealer-type malware is often distributed under the guise of game hacks, cheats and cracks. This time, the researchers discovered another type of malicious activity linked to gaming: the attackers placed poisoned bundles on the victims’ YouTube channels under the guise of gaming-related content, alongside a link to a self-extracting RAR archive in the video description. The archive contains several malicious files – a notorious RedLine stealer among them.
The stealer can plunder usernames, passwords, cookies, bank card details and autofill data from Chromium- and Gecko-based browsers, data from cryptowallets, instant messengers and FTP/SSH/VPN clients, as well as files with particular extensions from devices. In addition, RedLine can download and run third-party programs, execute commands in cmd.exe and open links in the default browser. The stealer spreads in various ways, including through malicious spam e-mails and third-party loaders.
In addition to the RedLine payload itself, the discovered bundle is of note for its ability for self-propagation. Several files in the bundle in the description are responsible for this. They receive videos and post them to the infected users’ YouTube channels, along with the links to a password-protected archive. The videos advertise cheats and cracks and provide instructions on hacking popular games and software. Among the games mentioned are APB Reloaded, CrossFire, DayZ, Dying Light 2, F1® 22, Farming Simulator, Farthest Frontier, FIFA 22, Final Fantasy XIV, Forza, Lego Star Wars, Osu!, Point Blank, Project Zomboid, Rust, Sniper Elite, Spider-Man, Stray, Thymesia, VRChat and Walken.
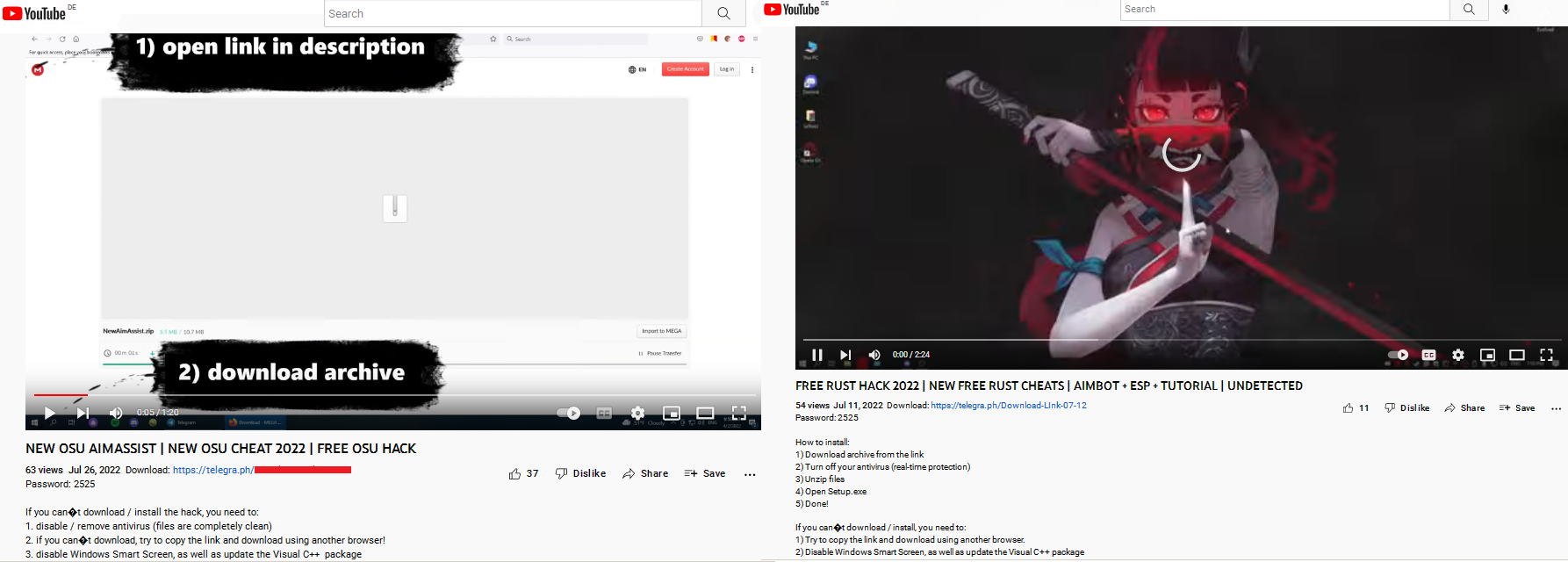
Examples of videos spreading the bundle
Once the victims themselves download the original bundle, the RAR archive is self-extracting. It contains a number of malicious files, clean utilities and a script to automatically run the unpacked contents. Some of the files’ names include explicit language.
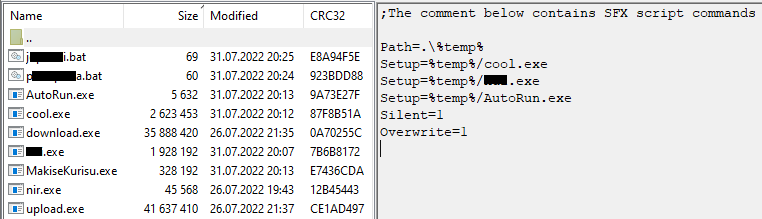 Contents of the self-extracting
archive
Contents of the self-extracting
archive
Another element that caught the researchers’ eye is a miner. It makes sense, since the main target audience, judging by the video, is gamers. They are likely to have video cards installed that can be used for mining.
“Gamers are one of the most popular groups targeted by cybercriminals,” said Oleg Kupreev, senior security researcher at Kaspersky. “This time attackers used gaming related content as bait for stealing victims’ credentials, as well as mining from their computers. Our advice would be to carefully pick the sources to quench your gaming thirst and do not download any suspicious archives from unreliable accounts”
Read about Redline gaming-related attacks on Securelist.
To protect yourself from malware hidden in open-source packages, Kaspersky recommends the following:
● Open-source repositories allow anyone to publish their own packages, and not all of them are completely secure. For example, attackers can impersonate popular open-source packages by changing one or two letters in the name to fool the user into thinking they are downloading the genuine package. Therefore, we recommend that you be on your guard and not to treat these packages as trusted.
● In general, development or build environments are convenient targets for attackers trying to organize supply chain attacks. That means such environments urgently require strong antimalware protection such as Kaspersky Hybrid Cloud Security.
● If you want to be among the first to know about new malicious campaigns spreading via open-source code, subscribe to threat intelligence feeds and reports, such as the ones provided via Threat Intelligence Portal.
About Kaspersky
Kaspersky is a global cybersecurity and digital privacy company founded in 1997. Kaspersky’s deep threat intelligence and security expertise is constantly transforming into innovative security solutions and services to protect businesses, critical infrastructure, governments and consumers around the globe. The company’s comprehensive security portfolio includes leading endpoint protection and a number of specialized security solutions and services to fight sophisticated and evolving digital threats. Over 400 million users are protected by Kaspersky technologies and we help 240,000 corporate clients protect what matters most to them. Learn more atusa.kaspersky.com.
Media Contact
Sawyer Van Horn
sawyer.vanhorn@Kaspersky.com
(781) 503-1866




