Malware linked to ScarCruft APT actor
Woburn, MA – November 29, 2021 – Today Kaspersky researchers announced their discovery of a previously unknown malware, dubbed Chinotto, targeting North Korean defectors and human rights activists. The malware, operated by the Advanced Persistent Threat (APT) actor, ScarCruft, is implemented in PowerShell, Windows executables, and Android apps. It is capable of controlling and exfiltrating sensitive information from its targets. The attackers attempted to gather information and attack victims' connections using compromised social network and email accounts.
The ScarCruft group is a nation-state sponsored APT actor known to mostly surveil government organizations related to the Korean Peninsula, North Korean defectors and local journalists. Recently, Kaspersky was approached by a local news service with a request for technical assistance during their cybersecurity investigations. As a result, Kaspersky researchers had an opportunity to perform a deeper investigation on a computer compromised by ScarCruft. The researchers worked closely with the local CERT to investigate the attacker's command-and-control infrastructure. During the analysis, Kaspersky uncovered an elaborate targeted campaign by this threat actor focused on users connected to North Korea.
As a result of the investigation, Kaspersky experts discovered a malicious Windows executable dubbed Chinotto. This malware is available in three versions: PowerShell, Windows executable and an Android app. All three versions shared a similar command and control scheme based on HTTP communication. This means that the malware operators can control the whole malware family through one set of command and control scripts.
When simultaneously infecting the computer and the victim's phone, the malware operator can overcome two-factor authentication in messengers or email by stealing SMS messages from the phone. After that, the operator can steal any information they are interested in and continue attacks on the victim's acquaintances or business partners.
The malware contains masses of garbage code meant to impede analysis. This includes filling the buffer with meaningless data and never using it.
Furthermore, the investigated computer was infected with PowerShell malware, and Kaspersky researchers found evidence that the attacker had already stolen the victim's data and tracked their actions for months. Although Kaspersky experts cannot estimate exactly how much and what data was stolen, they know that the malware operator collected screenshots and exfiltrated them between July and August 2021.
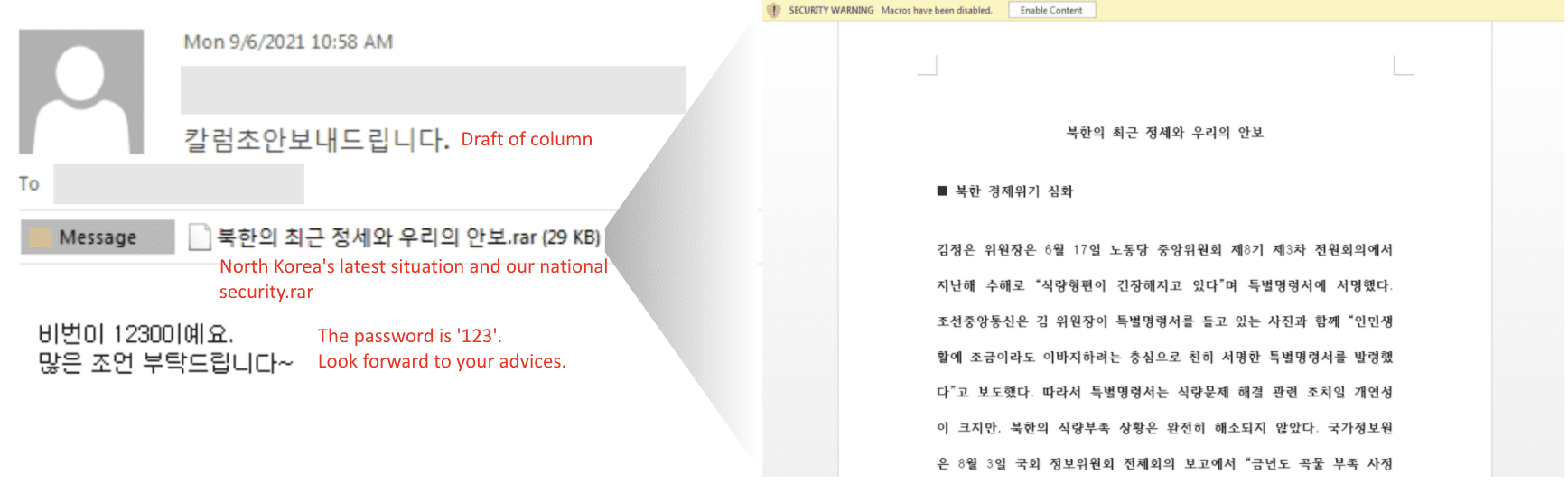
The actor sends a phishing email with a decoy to spread the malicious file
Initially, the attacker used the victim's stolen Facebook account to contact an acquaintance of the victim, who also runs a business related to North Korea. Following this, they used the connection to gather information about his activities and later attacked the target with a spear-phishing email containing a malicious Word document dubbed "North Korea's latest situation and our national security."
This document included a malicious macro and a payload for a multi-stage infection process. The first stage macro checks for the existence of a Kaspersky security solution on the victim's machine. If installed on the system, the macro enables trust access for Visual Basic Application (VBA). By doing so, Microsoft Office will trust all macros and run any code without showing a security warning or requiring the user's permission. In the case that no Kaspersky security software is installed, the macro directly proceeds to decrypt the next stage's payload. Later, after this initial infection, the attackers delivered the Chinotto malware and then could control and exfiltrate sensitive information from the victims.
During the analysis, Kaspersky experts also identified four other victims, all located in South Korea, and compromised web servers that had been in use since early 2021. According to the research, the target of the threat is individuals rather than specific companies or organizations.
"Many journalists, defectors, and human rights activists are targets of sophisticated cyberattacks,” said Seongsu Park, principal security researcher at Kaspersky's Global Research and Analysis Team (GReAT). “However, they generally lack the tools to defend against and respond to such surveillance attacks. This research demonstrates the importance of security experts sharing knowledge and investing in new types of security solutions that can combat such threats. Furthermore, our collaboration with the local CERT has given us a unique perspective on ScarCruft's infrastructure and its technical characteristics, which I hope will improve our security against their attacks."
Read the full report on ScarCruft on Securelist.
To protect yourself from such threats, Kaspersky recommends:
● Downloading your apps and programs from trusted websites.
● Don't forget to update your operating system and all software regularly. Many safety issues can be solved by installing updated versions of software.
● Being suspicious of email attachments by default. Before clicking to open an attachment or follow a link, consider carefully: Is it from someone you know and trust; is it expected; is it clean? Hover over links and attachments to see what they’re named or where they really go.
● Avoiding installing software from unknown sources. It may and often does contain malicious files.
● Using a strong security solution on all computers and mobile devices, such as Kaspersky Internet Security for Android or Kaspersky Total Security.
To protect organizations, Kaspersky suggests the following:
● Set up a policy for non-corporate software use. Educate your employees about the risks of downloading unauthorized applications from untrusted sources.
● Provide your staff with basic cybersecurity hygiene training, as many targeted attacks start with phishing or other social engineering techniques.
● Install anti-APT and EDR solutions, enabling threat discovery and detection, investigation and timely remediation of incidents capabilities. Provide your SOC team with access to the latest threat intelligence and regularly upskill them with professional training. All of the above is available within the Kaspersky Expert Security framework.
● Along with proper endpoint protection, dedicated services can help against high-profile attacks. Kaspersky Managed Detection and Response service can help identify and stop attacks in their early stages before the attackers achieve their goals.
About Kaspersky
Kaspersky is a global cybersecurity and digital privacy company founded in 1997. Kaspersky's deep threat intelligence and security expertise is constantly transforming into innovative security solutions and services to protect businesses, critical infrastructure, governments and consumers around the globe. The company's comprehensive security portfolio includes leading endpoint protection and a number of specialized security solutions and services to fight sophisticated and evolving digital threats. Over 400 million users are protected by Kaspersky technologies, and we help 240,000 corporate clients protect what matters most to them. Learn more at usa.kaspersky.com.
Media Contact
Sawyer Van Horn
sawyer.vanhorn@Kaspersky.com
(781) 503-1866




