Woburn, MA – April 24, 2023 – Kaspersky has released results from a new investigation into the Tomiris APT group, focusing on an intelligence gathering campaign in Central Asia. This Russian-speaking actor has used a wide variety of malware implants developed at a rapid pace and in all programming languages imaginable, presumably in order to obstruct attribution. The researchers sought to better understand the group’s use of malware that was previously linked to Turla, another notorious APT group.
Kaspersky first publicly described Tomiris in September 2021, following the investigation of a DNS-hijack against a government organization in the Commonwealth of Independent States (CIS). Back then, the researchers had noted inconclusive similarities with the SolarWinds incident. They continued to track Tomiris as a separate threat actor over several new attack campaigns between 2021 and 2023, and Kaspersky’s telemetry allowed them to shed light on the group’s toolset and its possible connection to Turla.
The threat actor targets government and diplomatic entities in the CIS with the final aim of stealing internal documents. The occasional victims discovered in other regions (such as the Middle East and Southeast Asia) turn out to be foreign representations of CIS countries, illustrating Tomiris’s narrow focus.
Tomiris goes after its victims using a wide variety of attack vectors: spear-phishing emails with malicious content attached (password-protected archives, malicious documents, weaponized LNKs), DNS hijacking, exploitation of vulnerabilities (specifically ProxyLogon), suspected drive-by downloads and other “creative” methods.
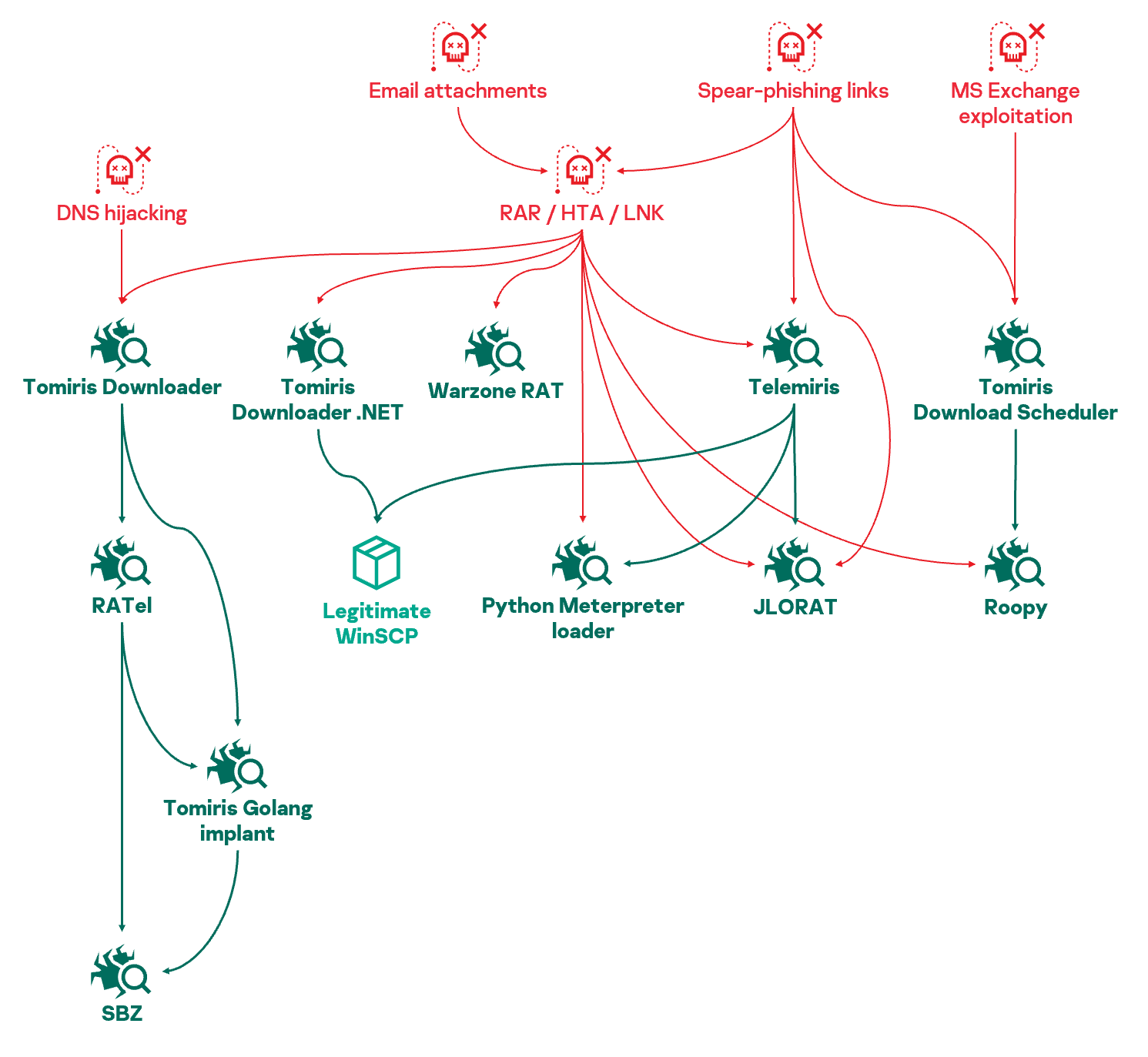 Relationships between
Tomiris tools. Arrows indicate a distribution link (parent distributed,
downloaded or contained child)
Relationships between
Tomiris tools. Arrows indicate a distribution link (parent distributed,
downloaded or contained child)
What makes the most recent Tomiris operations notable is that they appeared to leverage KopiLuwak and TunnusSched malware, which were previously connected to Turla. However, despite sharing this toolkit, Kaspersky’s latest research explains that Turla and Tomiris are very likely separate actors that could be exchanging tradecraft.
Tomiris is undoubtedly Russian-speaking, but its targeting and tradecrafts are significantly at odds with what has been observed for Turla. In addition, Tomiris’s general approach to intrusion and limited interest in stealth do not match documented Turla tradecraft. However, Kaspersky’s researchers believe that tool sharing is potential proof of some cooperation between Tomiris and Turla, the extent of which is difficult to assess. In any case, depending on when Tomiris started using KopiLuwak, a number of campaigns and tools believed to be linked to Turla may in fact need to be reevaluated.
“Our research shows that the use of KopiLuwak or TunnusSched is now insufficient to link cyberattacks to Turla,” said Pierre Delcher, senior security researcher at Kaspersky’s Global Research and Analysis Team (GReAT). “To the best of our knowledge, this toolset is currently leveraged by Tomiris, which we strongly believe is distinct from Turla – although both actors likely cooperated at some point. Looking at tactics and malware samples only gets us so far, and we are often reminded that threat actors are subject to organizational and political constraints. This investigation illustrates the limits of technical attribution, that we can only overcome through intelligence sharing.”
Read the full report about the Tomiris APT group on Securelist.
In order to avoid falling victim to a targeted attack by a known or unknown threat actor, Kaspersky researchers recommend implementing the following measures:
· Provide your SOC team with access to the latest threat intelligence (TI). The Kaspersky Threat Intelligence Portal is a single point of access for the company’s TI, providing cyberattack data and insights gathered by Kaspersky spanning over 20 years.
· Upskill your cybersecurity team to tackle the latest targeted threats with Kaspersky online training developed by GReAT experts.
· For endpoint level detection, investigation, and timely remediation of incidents, implement EDR solutions such as Kaspersky Endpoint Detection and Response.
· In addition to adopting essential endpoint protection, implement a corporate-grade security solution that detects advanced threats on the network level at an early stage, such as Kaspersky Anti Targeted Attack Platform.
· As many targeted attacks start with phishing or other social engineering techniques, introduce security awareness training and teach practical skills to your team – for example, through the Kaspersky Automated Security Awareness Platform.
About Kaspersky
Kaspersky is a global cybersecurity and digital privacy company founded in 1997. Kaspersky’s deep threat intelligence and security expertise is constantly transforming into innovative security solutions and services to protect businesses, critical infrastructure, governments, and consumers around the globe. The company’s comprehensive security portfolio includes leading endpoint protection and a number of specialized security solutions and services to fight sophisticated and evolving digital threats. Over 400 million users are protected by Kaspersky technologies, and we help 240,000 corporate clients protect what matters most to them. Learn more at usa.kaspersky.com.
Media Contact
Sawyer Van Horn
sawyer.vanhorn@Kaspersky.com
(781) 503-1866




