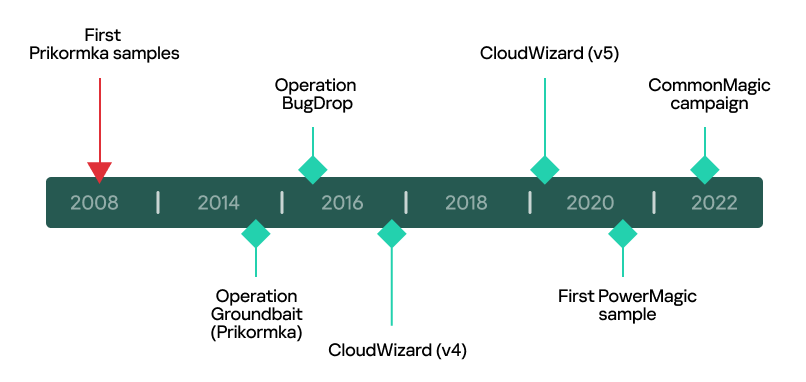
Woburn, MA – May 19, 2023 – Kaspersky researchers have provided further details on the CommonMagic campaign, which was first observed in March targeting companies in the Russo-Ukrainian conflict area. The new research reveals more sophisticated malicious activities from the same threat actor. The investigation identified that the newly-discovered framework has expanded its victimology to include organizations in Central and Western Ukraine. Kaspersky experts have also linked the unknown actor to previous APT campaigns, such as Operation BugDrop and Operation Groundbai (Prikormka).
In March 2023, Kaspersky reported a new APT campaign in the Russo-Ukrainian conflict area. This campaign, named CommonMagic, utilizes PowerMagic and CommonMagic implants to conduct espionage activities. Active since September 2021, it employs a previously unidentified malware to collect data from targeted entities. Although the threat actor responsible for this attack remained unknown at the time, Kaspersky experts have persisted with their investigation, tracing the unknown activity back to forgotten campaigns in order to gather further insights.
The recently uncovered campaign utilized a modular framework called CloudWizard. Kaspersky’s research identified a total of 9 modules within this framework, each responsible for distinct malicious activities such as gathering files, keylogging, capturing screenshots, recording microphone input, and stealing passwords. Notably, one of the modules focuses on exfiltrating data from Gmail accounts. By extracting Gmail cookies from browser databases, this module can access and smuggle activity logs, contact lists, and all email messages associated with the targeted accounts.
Furthermore, the researchers have uncovered an expanded victim distribution in the campaign. While the previous targets were primarily located in the Donetsk, Luhansk, and Crimea regions, the scope has now widened to include individuals, diplomatic entities, and research organizations in Western and Central Ukraine.
After extensive research into CloudWizard, Kaspersky experts have made significant progress in attributing it to a known threat actor. They have observed notable similarities between CloudWizard and two previously documented campaigns: Operation Groundbait and Operation BugDrop. These similarities include code similarities, file naming and listing patterns, hosting by Ukrainian hosting services, and shared victim profiles in Western and Central Ukraine, as well as the conflict area in Eastern Europe.
CloudWizard also exhibits resemblances to the recently reported campaign CommonMagic. Some sections of the code are identical, they employ the same encryption library, follow a similar file naming format, and share victim locations within the Eastern European conflict area.Based on these findings, Kaspersky experts have concluded that the malicious campaigns of Prikormka, Operation Groundbait, Operation BugDrop, CommonMagic, and CloudWizard may all be attributed to the same active threat actor.
“The threat actor responsible for these operations has demonstrated a persistent and ongoing commitment to cyberespionage, continuously enhancing their toolset and targeting organizations of interest for over fifteen years,” said Georgy Kucherin, security researcher at Kaspersky’s Global Research and Analysis Team. “Geopolitical factors continue to be a significant motivator for APT attacks and, given the prevailing tension in the Russo-Ukrainian conflict area, we anticipate that this actor will persist with its operations for the foreseeable future.”
Read the full report about the CloudWizard campaign on Securelist.
In order to avoid falling victim to a targeted attack by a known or unknown threat actor, Kaspersky researchers recommend implementing the following measures:
· Provide your SOC team with access to the latest threat intelligence (TI). The Kaspersky Threat Intelligence Portal is a single point of access for the company’s TI, providing it with cyberattack data and insights gathered by Kaspersky spanning over 20 years.
· Upskill your cybersecurity team to tackle the latest targeted threats with Kaspersky online training developed by GReAT experts
· For endpoint level detection, investigation, and timely remediation of incidents, implement EDR solutions such as Kaspersky Endpoint Detection and Response
· In addition to adopting essential endpoint protection, implement a corporate-grade security solution that detects advanced threats on the network level at an early stage, such as Kaspersky Anti Targeted Attack Platform
· As many targeted attacks start with phishing or other social engineering techniques, introduce security awareness training and teach practical skills to your team – for example, through the Kaspersky Automated Security Awareness Platform
About Kaspersky
Kaspersky is a global cybersecurity and digital privacy company founded in 1997. Kaspersky’s deep threat intelligence and security expertise is constantly transforming into innovative solutions and services to protect businesses, critical infrastructure, governments and consumers around the globe. The company’s comprehensive security portfolio includes leading endpoint protection, specialized security products and services, as well as Cyber Immune solutions to fight sophisticated and evolving digital threats. Over 400 million users are protected by Kaspersky technologies and we help over 220,000 corporate clients protect what matters most to them. Learn more at www.kaspersky.com.
Media Contact
Sawyer Van Horn
sawyer.vanhorn@Kaspersky.com
(781) 503-1866




