Woburn, MA – December 5, 2022 – During the first ten months of 2022, the proportion of users attacked by targeted ransomware almost doubled, compared to the same period of 2021. The striking growth indicates that ransomware gangs, new and old, have continued mastering their techniques. The final crimeware report of 2022 by Kaspersky covers the major developments in the ransomware world this year, including new features introduced by the notorious “LockBit” group, and a newcomer, “Play,” that employs self-propagation techniques.
According to Kaspersky security solutions, the share of users affected by targeted ransomware attacks accounted for 0.026% of all users attacked by malware in 2022 – versus 0.016% in 2021. These figures show that cybercriminals are steadily shifting from opportunistic assaults to precisely tailored ransomware attacks to accomplish their goals.
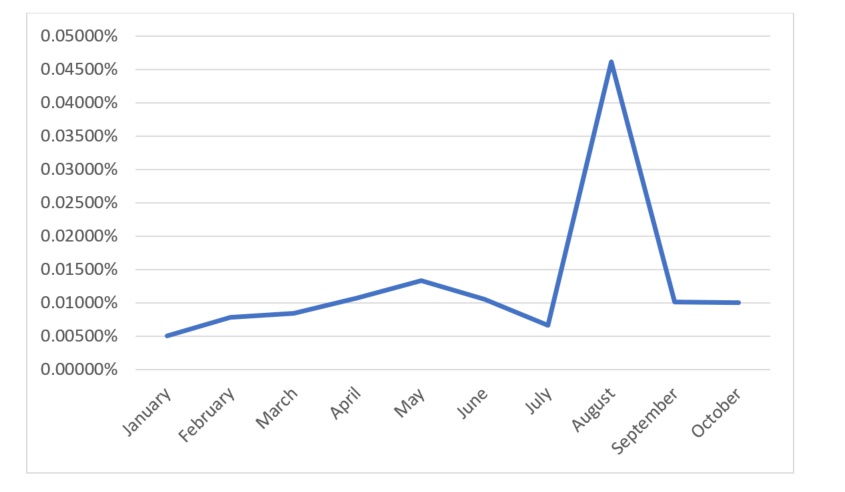 Proportion of users affected by targeted ransomware,
by month, January – October 2022
Proportion of users affected by targeted ransomware,
by month, January – October 2022
As recent investigations by Kaspersky show, ransomware groups continue to improve their techniques. One of them, Lockbit, remains one of the most popular, innovative and rapidly developing ransomware variants that are currently used. And this group can still ambush cybersecurity specialists by adding new options such as credential dumping. This technique means that the actor can take over the infected machine’s domain and create a named pipe to reset the operating system’s credentials.
New ransomware variants continue to emerge. In 2022, Kaspersky has detected over 21,400 ransomware strains.
 Number of new ransomware modifications, by
month, January – October 2022
Number of new ransomware modifications, by
month, January – October 2022
Kaspersky’s most recent discovery is “Play,” a new, highly obfuscated ransomware variant that makes analysis more difficult. Its code bears no resemblance to other ransomware samples but luckily Play is in early stages of development. When the investigation was conducted, the location of the leak could not be detected and victims were required to contact the criminals via an email address left in the ransom note. What captivated researchers’ attention was that Play contains a functionality that was recently found in other advanced ransomware variants: self-propagation. First, the attackers find a server message block (SMB) and establish a connection. Next, Play tries to mount the SMB mentioned above and distribute and execute ransomware in the remote system.
“Ransomware developers keep a close eye on the work of competitors,” said Jornt van der Wiel, security expert at Kaspersky. “If one successfully implements a certain functionality, there is a big chance that others will as well. This makes their ransomware more interesting to their affiliates. The self-propagation of ransomware is a clear example of this. More and more ransomware groups take on inventive techniques that make ransomware attacks even more targeted and destructive – and this year’s statistics do prove it. Another thing we'll never stop reminding the public of is the need to make regular backups and store them offline.”
Read the full crimeware report on Securelist.
To protect yourself and your business from ransomware attacks, consider following the rules recommended by Kaspersky:
- Do not expose remote desktop services (such as RDP) to public networks unless absolutely necessary and always use strong passwords for them.
- Promptly install available patches for commercial VPN solutions providing access for remote employees and acting as gateways in your network.
- Focus your defense strategy on detecting lateral movements and data exfiltration to the Internet. Pay special attention to the outgoing traffic to detect cybercriminals' connections.
- Back up data regularly. Make sure you can quickly access it in an emergency when needed.
- Use solutions like Kaspersky Endpoint Detection and Response Expert and Kaspersky Managed Detection and Response service, which help to identify and stop the attack on early stages, before attackers reach their final goals.
- Use the latest Threat Intelligence information to stay aware of actual TTPs used by threat actors. The Kaspersky Threat Intelligence Portal is a single point of access for Kaspersky’s TI, providing cyberattack data and insights gathered by our team for 25 years. To help businesses enable effective defenses in these turbulent times, Kaspersky has announced access to independent, continuously updated and globally sourced information on ongoing cyberattacks and threats, at no charge. Request access to this offer here.
About Kaspersky
Kaspersky is a global cybersecurity company founded in 1997. Kaspersky’s deep threat intelligence and security expertise is constantly transforming into innovative security solutions and services to protect businesses, critical infrastructure, governments and consumers around the globe. The company’s comprehensive security portfolio includes leading endpoint protection and a number of specialized security solutions and services to fight sophisticated and evolving digital threats. Over 400 million users are protected by Kaspersky technologies and we help 250,000 corporate clients protect what matters most to them. Learn more at usa.kaspersky.com.
Media Contact
Sawyer Van Horn
(781) 503-1866




