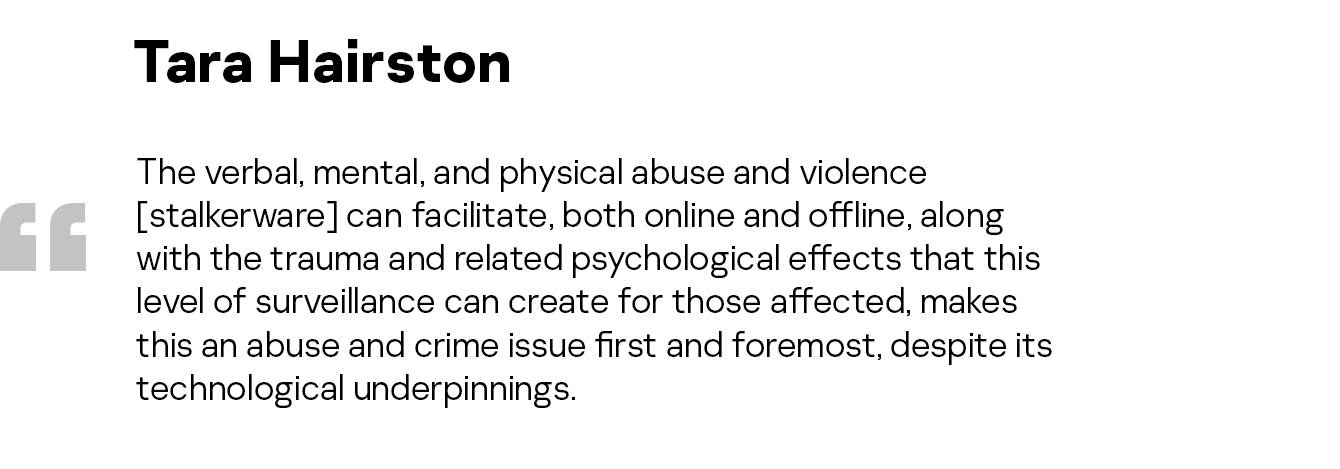
Using technology to perpetrate domestic abuse and intimate partner violence is not new. Stalkerware, commercially available software that enables online surveillance without a device user’s consent and knowledge, is just a recent example of how technology can enable offline and online harassment, stalking, abuse, and violence.
In order to raise awareness about the dangers of stalkerware and other forms of tech-enabled abuse, and to discuss how individuals can protect themselves, Tara Hairston, Head of Government Relations, North America for Kaspersky moderated an online panel event with Jennifer Landhuis, Director of the Stalking Prevention, Awareness, and Resource Center (SPARC), Adam Dodge, founder of EndTAB.org, and Lindsey Metselaar, Creator and Host of the popular millennial dating podcast, We Met At Acme.
The hour-long event, was attended by nearly 100 people which made for a fruitful conversation about stalking prevention and the need for collective action to support and assist individuals targeted by stalkerware. As a matter of fact, we decided to go off script to allow our panelists to answer the many questions left by audience members during the event, and those submitted to @wemetatacme prior to the event.
https://www.instagram.com/tv/CHgczjnDfGH/?utm_source=ig_web_copy_link
- 0:40 Opening remarks
- 02:48 What is stalkerware?
- 08:15 Overview of the issue of tech-enabled abuse and offline harm associated with it
- 12:30 How are organizations like SPARC working with other groups to hold perpetrators accountable for their crimes?
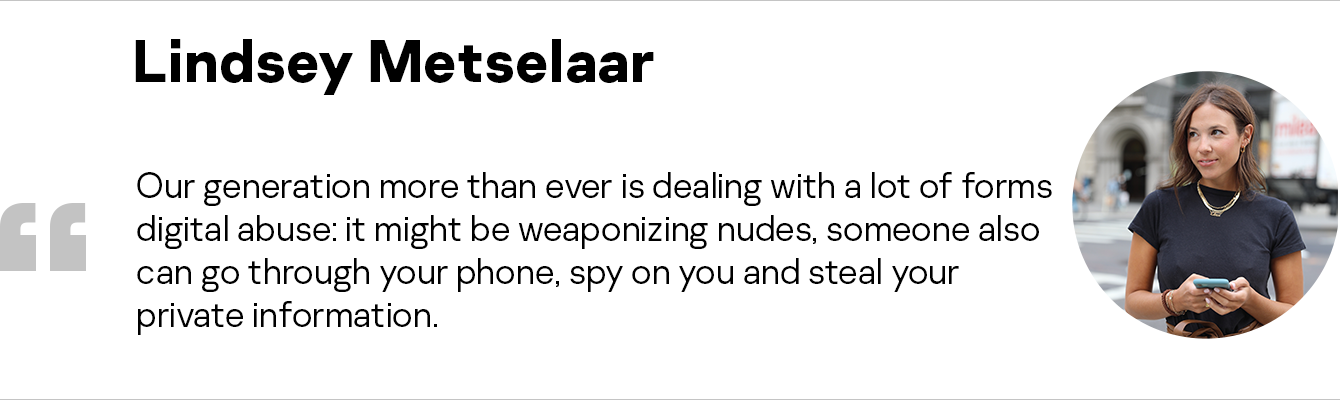
- 15:15 Has Lindsey’s community shared stories/concerns related to stalking?
- 19:15 How do you report stalking behavior?
- 25:00 How does intimate partner violence and stalking differ from traditional cybersecurity threats?
- 30:11 Q&A — When and how should you get a restraining order?
- 38:25 Q&A – How can we feel safe when dating online?
- 43:15 Q&A – What are the most used stalking apps? How can we check our devices for for hidden malware?
- 52:30 Q&A – How can tech platforms help to combat online abuse?
- 55:40 Concluding remarks
We all have a role to play in recognizing the insidious nature of these technologies, the psychological and traumatic effects they can have, and the need for collective action to support and assist individuals targeted by stalkerware and other forms of tech-facilitated and tech-enabled abuse. Unfortunately, we were unable to address all the questions received during the event. These are critical questions and we’d like to provide as much information to those who attended. So, we’re taking the time to answer those questions here.
What are the symptoms of stalkerware?
It is important to understand that symptoms are not proof. If you suspect stalkerware, trust your gut feeling and make a safety plan. Part of this safety plan could be to reach out to organizations working with victims of domestic violence.
Some of the common symptoms indicating the possibility of stalkerware on a device are:
- A fast-draining battery.
- Constant overheating.
- Unprompted resets.
- Large increase in mobile data use
- The possibility of other people having had recent physical access to your phone.
- Applications with suspicious access to GPS tracking, text messages, call recordings and other personal activities.
One of the most common methods of installation is physical access. Continue to stay proactive in preventative measures by using the following information how to minimize risks.
How to minimize risk?
There are a few pieces of advice that can help to increase your digital safety:
- Use a complex lock screen password and update it regularly.
- Do not disclose your password to anyone – not even yout family members.
- Do regular checks of your phone— delete apps you don’t use and review the permissions granted to each app.
- Disable the option of third-party application installation on Android devices.
- Protect your Android devices with anti-virus products, such as Kaspersky Internet Security for Android, which detects stalkerware and issues warnings.
- If you are an iPhone user, do not leave your phone unsupervised and unlocked (of course, the same, goes for Android device owners).
What professionals should one reach out to in this case?
It really depends on the situation and your comfort level. Law enforcement, local gender based violence organizations, digital forensics firms and victim resource sites such as www.NNEDV.org or www.safeescape.org.
Also check out the Get Help section of the Coalition Against Stalkerware.
Speaking of laws, do you think there will ever be a law such as a national stalking offenders registry?
No, registries are not an effective means of monitoring offenders. I do know there is a startup (Garbo.io) that is attempting to give people on online dating platforms the ability to see if the person they matched with has a domestic violence background.
What are some cybersecurity resources that are available to collaborate with advocates/victims?
The SafetyNet program of the National Network to End Domestic Violence has an app that can be helpful. You can access it at https://www.techsafetyapp.org/ or on any app store for free.
What do I do if I’m being called on no caller ID often? I answered the first time it started to happen back in April of this year and it has been constant since at weird hours during the day or at night.
You could try installing an app that unblocks blocked calls. There are several options on each store, so just search for “unblock caller ID”.
If you have an iPhone, you can block unknown numbers and spam calls. You can find detailed instructions on the Apple website. Similarly, Android users can find detailed instructions on Google Support.
When a client shares that their phone is working differently, what is the most TIC method of taking action? i.e. a client clicked a link on their phone, then they noticed that the only income texts and calls were from abuser – all other texts and calls were blocked. We helped call phone carrier and they were unable to assist or provide more information. Client eventually had to purchase new phone.
If the client wishes to have law enforcement involved they can take the phone to LE (law enforcement) to begin an investigation. If they choose to take the phone as part of the investigation, they can do a cell phone forensic exam to determine if the phone has been compromised. If the victim does not wish to pursue criminal charges, they could consider factory resetting the phone. However, if someone is monitoring the phone that will alert that person that the victim is aware of what is going on. Also factory resetting may or may not get rid of Stalkerware. If a factory reset is done, it is advisable to not restore their purchases as it could compromise the phone. To be safer, they would need to create a new Google/iTunes account with new logins and passwords and purchase the apps again (likely not cost effective).
My boyfriend’s ex suddenly began me stalking around 10 years after they broke up. We have seen them around our neighborhood a lot but most of the harassment has come via DM. They are now threatening to reach out to me. I have blocked all accounts. Is it better to restrict the accounts to see if they continue to reach out?
This is a personal choice. If you have blocked accounts and the activity has ceased, then I would not turn them back on or allow access. Even if you did allow this access, there is a possibility that the communication would not be enough to move forward with the criminal justice system and then you have been subjected to additional harmful and unsettling communication. I would stick with your original plan for now and if there is additional contact, I suggest you work with a victim service provider to determine a safety plan and additional ways to gather evidence.
I found, what I have now found out, is “auto forward spy” that my ex-husband installed on my phone. I deleted it immediately because I was terrified. The police now have my phone and are running forensics. I am so worried they won’t be able to find a trace of it. He had to pay for the program. He had access to everything on my phone and could even turn my mic on. Do I have any chance of actually linking this to him?
There would be two steps to this. The first is finding the evidence on the phone through the cell phone forensic exam. The second is linking the stalkerware to your ex-husband. That part of the investigation is determined by law enforcement’s steps to be able to prove that the offender is the person that placed it on your phone. This is a long and complicated process and I would suggest you see if the law enforcement agency has a victim advocate who can work with you and keep you apprised of the investigation.
For friends and family of someone who is being stalked, what are ways to make sure we are protecting ourselves? How can we safely contact a friend/family member who is regularly having their phone/accounts hacked, for example, while protecting our information from being intercepted by the stalker?
Using a safer phone for communication (an affordable phone that you can purchase from a chain store) that you give to the family member and s/he uses that phone only for communications with safe people. Otherwise, in-person communications, using landlines or work phones or other options can be safer or creating new emails and only accessing those on computers the victim does not believe the offender has accessed. Creating new emails and passwords that the offender cannot guess are important.
To learn more about stalking, domestic and intimate partner violence, stalkerware, and tech-enabled abuse, here are a few links that you might find useful:
 stalkerware
stalkerware



 Tips
Tips