Errors and vulnerabilities become almost inevitable when developing any complex IT system, software or hardware. These errors are often found not by employees and technical experts of the company that produces the software or hardware, but by external researchers. Eliminating these errors and potential vulnerabilities is key to strong cybersecurity, where our researchers and experts work too. Thus, the main source of errors and failures — humans — is also a key factor for their timely detection and correction. At the same time, it is important to realize that this process of error correction can potentially create new risks and failures instead of solving the problem.
At Kaspersky, we adhere to clear and transparent ethical principles in responsible vulnerability disclosure (RVD) — the process we follow when we find vulnerabilities in the systems of other organizations. We base our five principles on our more than 23 years of global work and continue to be inspired by some best practices and, in particular, the Forum of Incident Response and Security Teams’ (FIRST’s) Code of Ethics. In every case, we place top priority on the safety and security of our users (the people and organizations using Kaspersky products and solutions).
At the same time, we respect the interests of all involved parties: the individuals or organizations whose product is vulnerable, their clients (as possible victims), and the cybersecurity industry as a whole.
Following the principles ensures we act in a transparent, responsible, and consistent manner to build a safer information and communications technology (ICT) ecosystem. For such an approach to work across the entire IT industry, however, other vendors — and their users, independent researchers, regulators, and other interested parties — must also use similar motives as their guides. Therefore, we decided to publish our principles for responsible disclosure of vulnerabilities found in other companies’ software. We are in the vanguard.
Principle #1: Build trust
A certain degree of distrust is the foundation of information security. But vulnerability disclosures without trust simply will not work, so we presume benevolence as a motive for all parties, although of course we take the time and effort to coordinate actions and reduce any harm of vulnerability — trust, but verify. We don’t publish information about vulnerabilities for fun or ambition, but only in the interests and safety of users and society.
Principle #2: Inform the affected party first
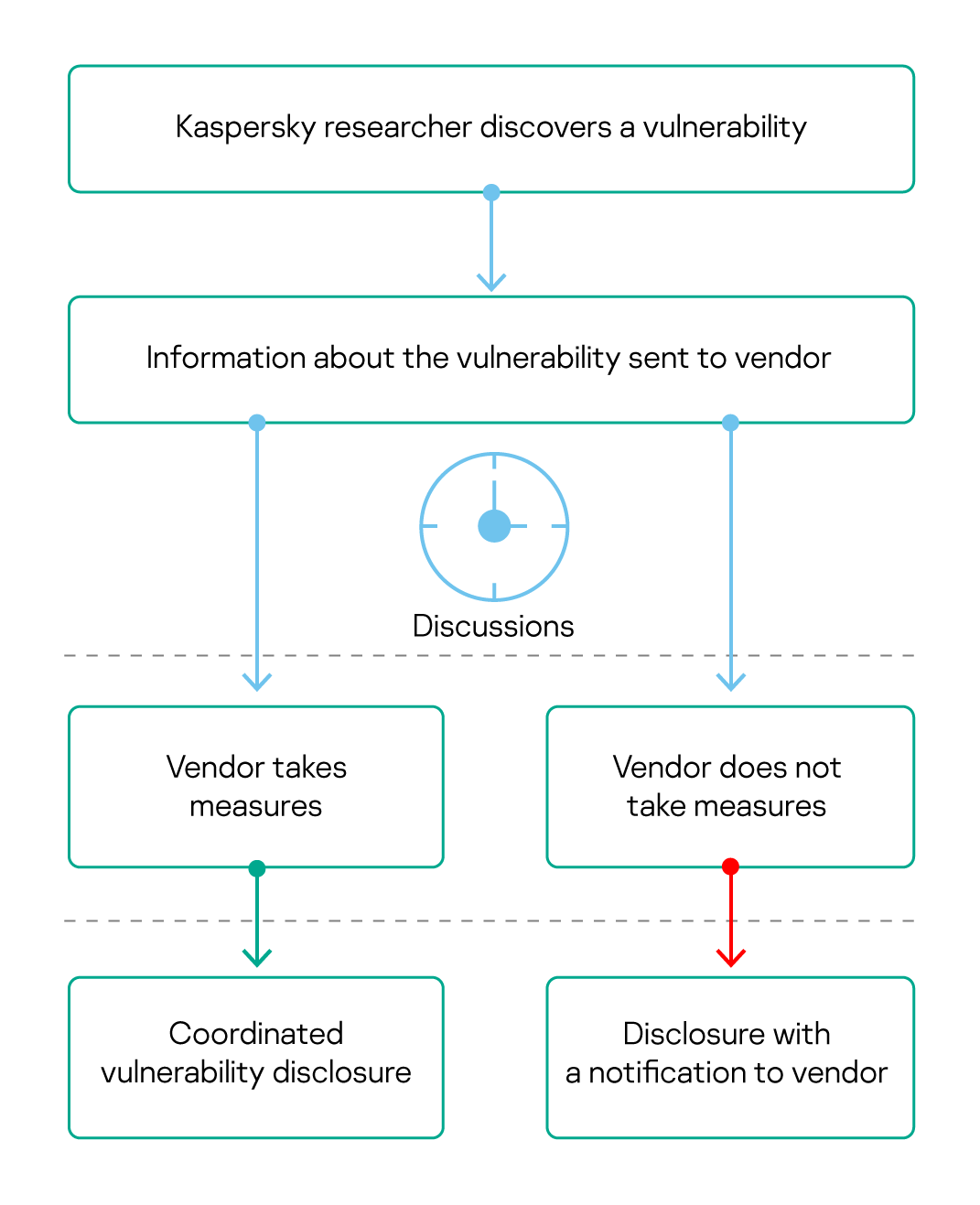
Vulnerability disclosure is a complex process that can face numerous obstacles such as unresponsive or even unreachable participants. Despite such issues, providing timely and precise information to affected vendors is critical. First, we jointly coordinate efforts to eliminate the vulnerability and minimize user risk. For that, in turn, the vendor needs to provide a clear and transparent way to report and process information about vulnerabilities (more about how that works at Kaspersky here and here).
Principle #3: Coordinate efforts
To state the obvious, every vulnerability is unique. Some threaten users of a single product, and others may affect multiple parties (e.g., in cases involving international companies with complex supply chains). Vulnerabilities may also affect critical infrastructure and public sector networks and thus threaten national security. At the same time, researchers and vendors are not the only relevant parties; regulators, customers, independent researchers, and white-hat hackers may also be involved. For effective coordination between all stakeholders, we are guided by international best practices (for example, the ISO/IEC 29147:2018 standard for vulnerability disclosure). In particular, we try to provide all participants with sufficient time for a thorough vulnerability analysis and remediation development.
Principle #4: Maintain confidentiality where appropriate
If technical information about a vulnerability is revealed too early in the process, attackers can take advantage of it. That’s why we share information in a confidential manner with parties that need to develop mitigation measures and then work through the most trusted and secure communication channels for reporting. For the same reason, we negotiate disclosure terms and conditions with the vendor. However, if a vendor doesn’t reply, depending on the severity and scale of the vulnerability and immediacy of the risk, we make the disclosure through our own communication channels and disclose this according to our internal policies, local regulations, and industry best practices, all while keeping the vendor informed.
Principle #5: Incentivize desired behavior
Despite industry efforts, cybercriminals continue to seek out — and find — vulnerabilities. Therefore, we consider it important to openly support everyone who responsibly reports on vulnerabilities and follows industry best practices for responsible disclosure.
Saving vulnerability disclosure
I am convinced that if all parties adhere to similar ethical principles, we will be able to work together to make the ICT ecosystem not only safer, but also healthier and more predictable for our users — the people for whom we work.
You can learn more about our Ethical Principles for RVD on the Global Information Transparency Initiative page.
 vulnerabilities
vulnerabilities

 Tips
Tips