Any movie, be it horror, action or thriller, has a moment that any IT specialist would call comedic, when a demonstration of a mainframe hacking, a virus in action or any other computer-related action occurs. Smart directors will show this part very briefly, avoiding any view of the computer screen, which could distract the audience from the plot. The reality is though, hacks are typically ugly and may take days or even weeks to complete, so this makes us even more respectful of those movie producers who manage to make movies based entirely on computer and network related subjects, and make them look good, while avoiding too much criticism from professionals.
Hackers [1995]

The creators of this movie avoid showing the hacking process most of the time. They show a lot of rapid-fire keyboard clicking and some abstract visuals, but nothing more. Many of the portrayed hacks are quite possible and the hacker lingo in the movie is quite realistic: Unix books, weak passwords and similar subjects clearly indicate that the director and writer spent a lot of time learning about how hacking is done. It seems they decided that realistically depicted hacking just looks boring.
Live Free or Die Hard [2007]

The popular action movie, starring Bruce Willis, features a lot of funny dialogue about cyber security and heavily overuses hacking themes in the plot. Although many tricks depicted, i.e. remote CCTV access and traffic light control, are sometimes possible, it’s very complicated to perform all of them, especially in a timely manner and in such a tight sequence. In addition, it is tricky to blow something up remotely using the Internet. Though examples of malware disrupting real factories already exist, it’s not the most practical approach to blowing things up, especially when exact timing is involved.
Nevertheless, critical infrastructure requires hacking protection and we should thank Bruce Willis for drawing public attention to this fact.
007: Skyfall [2012]

From the computer geek point of view, this movie is memorable thanks to another tricky-to-implement Internet-controlled explosion, and the generally correct idea that top-secret information theft happens on the Internet, not on service stairs where spies are hiding from security personnel. Other amusing scenes include a funny-decorated hacking HQ on a desolated island. Actually, there is no advantage in building a data center on a secluded island in Asia, as it’s easily traceable and providing enough bandwidth for it would be tricky. Real hackers often rent required computing power in huge cities, especially in Asia. Physical isolation is not required as the necessary protection is provided by encryption.
Wargames [1983]

This is a very old movie that is still adored by geeks. The plot involves young hackers penetrating a powerful military computer just to discover that it has some simulation games installed. While playing these games, people don’t realize that it’s actually not a simulation and they are engage real missiles, possibly starting World War III. This movie depicts some real hacker tricks of those times, e.g. wardialing. However, the main point in “Wargames” is not accurate.
The Internet was born as a military network, that’s why original Internet protocol had minimal protection implemented. It was assumed that any person accessing a computer terminal was triple-checked by security staf. Nowadays, that obviously does not happen. Quite luckily though, military personnel watched the evolution of the Internet quite closely, so all important military systems today are “airlocked” – or totally isolated from the Internet.
Sneakers [1992]
The plot of this movie was created by the aforementioned “Wargames” authors. This plot revolves around a “black box”, which allows its owner to break any kind of encryption. In the film, secret service from multiple countries pursue this treasure, and NSA plays a major role as well. In reality, this type of device is impossible to build (otherwise NSA wouldn’t pursue crypto-mail providers with such passion). On the other hand, the social engineering tricks that were depicted work flawlessly – both in 1992 and 2013.
Bourne Ultimatum [2007]

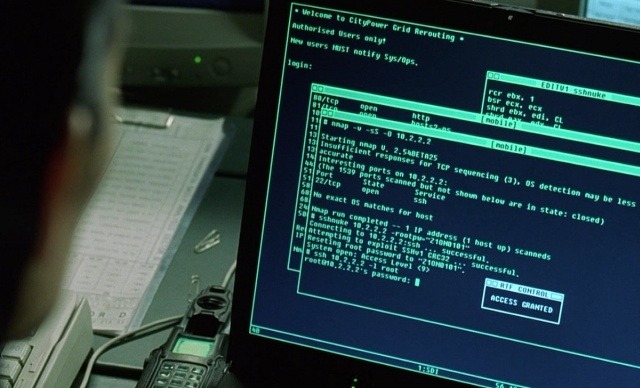
This is a rare gem. The spy movie writers for this film really listened to computer security advisors when creating it! Of course, you have to hack some computers to steal secret documents in the XXI century. And computer screens in this movie feature real-life applications being used both by hackers and system administrators: SSH, bash and Hollywood’s favorite port scanner NMAP.
The Matrix Reloaded [2003]
The Matrix trilogy greatly increased the popularity of the simulated reality philosophy, but geeks like this movie because of its aesthetics. Of course the plot involves a lot of hacking, but it usually happens like magic, making hacking no different from Harry Potter spells. Generally speaking, the “escape from a sandbox” problem, which Matrix heroes are trying to solve, really exists and modern malware often solves it in the form of exploits, i.e. for Adobe Reader. But movie creators hardly thought about that – besides showing real NMAP utility once in a while.
Paranoia 1.0 [2004]

This is a very fancy plot that involves artificial intelligence, nanorobots, corporate conspiracy and, of course, computer hacking. This is not a Hollywood movie, so authors ignored Hollywood tradition to show NMAP as an ultimate hacking tool and depicted real source code of the online virus scanner called Viralator.
Tron [1982]
Almost twenty years before “The Matrix” and “Thirteenth floor,” living people and computer programs met as equals in the cult movie “Tron.” Movie creators perceived the computer as an arcade gaming machine, so despite the possibility of the realistic hacking mentioned in the plot, it’s depiction was more like Pong and Space Invaders. It was extremely naïve, but despite this (or maybe thanks to this), the movie became a sci-fi classic.
The Girl with the Dragon Tattoo [2009]

Many people prefer the Swedish screen version of Stieg Larsson’s novel because its atmosphere and characters are more realistic to them. And this is true when it comes to the computer hacking scenes, where movie protagonist use good old NMAP to scan the computers of people she is interested in. This part of the plot is quite viable, because computer hacking has become one of the most efficient ways to dive deeper into people’s secrets. In addition, it’s often easier, cheaper and safer to do this rather than establish secret surveillance or break into someone’s apartment. There is an even more effective way though – to steal someone’s smartphone, which is typically full of secrets and private data.
Of course, it’s possible to protect yourself from all of these types of threats by using a reliable security solution for all your devices, e.g. Kaspersky Internet Security. But movie characters are seldom aware of this!
 hackers
hackers


 Tips
Tips