On August 15, the Signal team reported that unknown hackers attacked users of the messenger. We explain why this incident demonstrates Signal’s advantages over some other messengers.
What happened?
According to the statement issued by Signal, the attack affected around 1900 users of the app. Given that Signal’s audience runs to more than 40 million active users a month, the incident impacted only a tiny share of them. That said, Signal is used predominantly by those who genuinely care about the privacy of their correspondence. So even though the attack affected a minuscule fraction of the audience, it still reverberated around the information security world.
As a result of the attack, hackers were able to log in to the victim’s account from another device, or simply find out that the owner of such and such phone number uses Signal. Among these 1900 numbers, the attackers were interested in three specifically, whereupon Signal was notified by one of these three users that their account had been activated on another device without their knowledge.
How did it happen?
On the pages of Kaspersky Daily, we have often talked about the fact that Signal is a secure messenger, and yet it was successfully attacked. Does that mean that its renowned security and privacy are just a myth? Let’s see exactly what the attack looked like and what role Signal actually played in it.
Let’s start with the fact that Signal accounts, as in, say, WhatsApp and Telegram, are linked to a phone number. This is common, but not universal practice. For example, the secure messenger Threema proudly states as one of its selling points that it does not tie accounts to phone numbers. In Signal, a phone number is needed for authentication: the user enters their phone number, to which a code is sent in a text message. The code must be entered: if it is correct, that means the user does indeed own the number.
The sending of such text messages with one-time codes is handled by specialized companies that provide the same authentication method for multiple services. In the case of Signal, this provider is Twilio — and it is this company that the hackers targeted.
The next step was phishing. Some Twilio employees received messages saying that their passwords were supposedly old and needed updating. To do so, they were invited to click a (that’s right) phishing link. One employee swallowed the bait, went to the fake site and entered their credentials, which fell straight into the hackers’ hands.
These credentials gave them access to Twilio’s internal systems, enabling them to send text messages to users, and to read them. The hackers then used the service to install Signal on a new device: they entered the victim’s phone number, intercepted the text with the activation code and, voilà, got inside their Signal account.
How this incident proves Signal’s robustness
So, it turns out that even Signal isn’t immune to such incidents. Why, then, do we keep talking about its security and privacy?
First of all, the cybercriminals did not gain access to correspondence. Signal uses end-to-end encryption with the secure Signal Protocol. By using end-to-end encryption, user messages are stored only on their devices, not on Signal’s servers or anywhere else. Therefore, there is simply no way to read them just by hacking Signal’s infrastructure.
What is stored on Signal’s servers is users’ phone numbers as well as their contacts’ phone numbers. This allows the messenger to notify you when a contact of yours signs up for Signal. However the data is stored, first, in special storages called secure enclaves, which even Signal developers can’t access. And second, the numbers themselves aren’t stored there in plain text, but rather in the form of a hash code. This mechanism allows the Signal app on your phone to send encrypted information about contacts and receive a likewise encrypted reply as to which of your contacts uses Signal. In other words, the attackers could not gain access to the user’s contact list either.
Lastly, we should stress that Signal was attacked in the supply chain — through a less protected service provider used by the company. This, therefore, is its weak link. However, Signal has safeguards against this, too.
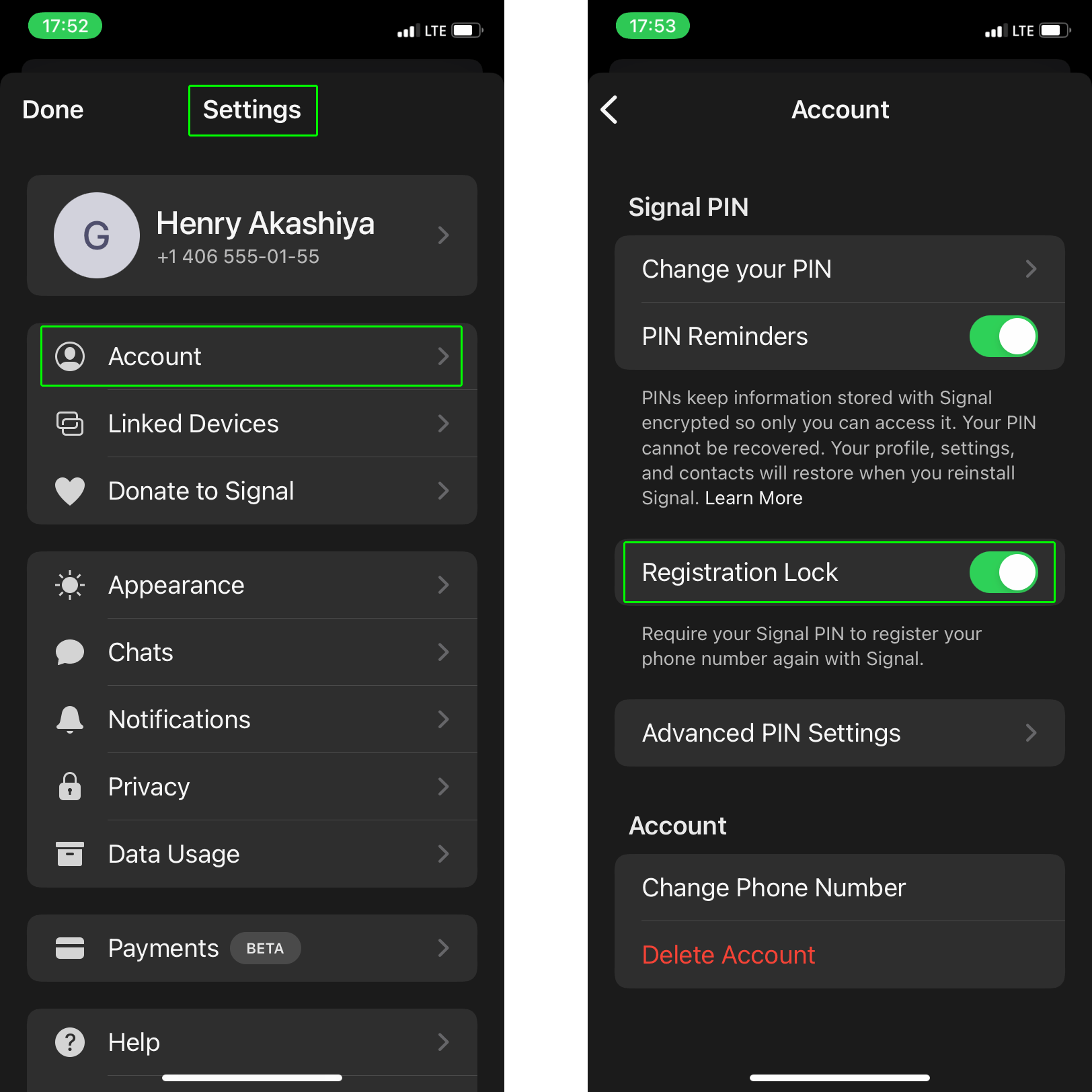
The app contains a feature called Registration Lock (to activate go to Settings → Account → Registration Lock), which requires a user-defined PIN to be entered when activating Signal on a new device. Just in case, let’s clarify that the PIN in Signal has nothing to do with unlocking the app — this is done through the same means you use to unlock your smartphone.
By default, Registration Lock is disabled, as was the case for at least one of the hacked accounts. As such, the cybercriminals managed to pull off the attack by impersonating the victim of the attack for roughly 13 hours. If Registration Lock had been enabled, they could not have logged in to the app knowing only the phone number and verification code.
What can be done to better protect messages?
To sum up: the attackers did not hack Signal itself, but its partner Twilio, giving them access to 1900 accounts, which they used to log in to three of them. What’s more, they gained access to neither correspondence nor contact list, and could only try to impersonate the users of those accounts they penetrated. If these users had turned on Registration Lock, the hackers could not even have done that.
And although the attack was formally a success, there is no reason to get scared and stop using Signal. It remains a pretty secure app that provides good privacy for your messages, as demonstrated by this hacking incident. But you can make it even safer:
- Enable Registration Lock in the Signal settings, so that cybercriminals can’t log in to your account without knowing your private PIN, even if they have the one-time code for activating Signal on a new device.
- Read our blog post about setting up privacy and security in Signal, and configure your app. Signal has basic settings as well as options for the truly paranoid, that provide extra security at the cost of some usability.
- And, of course, install a security app on your smartphone. If malware gets on your device, no safeguards on Signal’s side will protect your messages and contact list. But if malware is not allowed in, or is at least caught in time, there is no threat to your data.
 messengers
messengers

 Tips
Tips