“Three billion human lives ended on August 29, 1997. The survivors of the nuclear fire called the war Judgment Day. They lived only to face a new nightmare: the war against the Machines”.
Well, not really. Back then, in 1997, the first Wi-Fi specification (802.11b) was standardized, Steve Jobs returned to Apple, .PNG was invented, and a computer defeated a human in a chess match. But the Judgment Day never happened. Machines have not evolved enough to start the apocalypse. True artificial intelligence capable of destroying the humanity is still nowhere to be seen, but that does not mean that change did not come over the past 18 years.
Change is here – once the definition of ‘robot’ is extended beyond the image imposed on us by Hollywood, we see that robots are indeed around us in abundance, and local “Armageddons” are happening constantly here and there. This is not because of the robots’ free will but rather that someone did a poor job in creating them.
Today’s weekly news digest covers three stories about the mistakes coders made when programming robots, the way other people exploit those design flaws, and then the reckoning. I would not go as far as calling it the end of the world, but in terms of hazard, it’s code coral, I repeat, code coral, with a sprinkle of the color pumpkin. The rules of the road, as always: every week the team of our Threatpost news blog handpicks three top news, which I ruthlessly comment. All of the previous editions can be found here.
I ran a small survey in my last post to find out how people use password managers, and the results are the following: A little over half of respondents (62%) agree that password managers are instrumental for keeping all unique passwords in order. A half of those who answered the second question (in total 123) use such managers – I should note this number is quite higher for the people of the IT community, whereas for ordinary folks this number constitutes only 7%.
A permanent backdoor in Cisco routers via modified firmware
I have previously stated that today’s router is a secret black box standing quietly in a dusty corner most of the time, and no one ever gives a hoot about it. That assumption applies both to home and industrial routers. Researchers discovered a possibility to install backdoors into at least three models of industrial routers by Cisco. Taking into consideration the usual treatment routers receive, this could remain unnoticed for quite a long time.
The concept of the attack, easy at the first site yet complex in reality, is the following: upon obtaining access to a vulnerable router, one could upload modified firmware, and once the attacked gets remote access to the appliance, they could install plugins to enable further compromising.
It’s not all that bad, really. FireEye’s researchers identified only three vulnerable models: Cisco 1841, 2811 and 3825. As far as I know, those models are at the end of life and would stop being supported by the vendor in no time. The initial attack vector does not exploit a vulnerability in routers: apparently, the firmware could be modified only upon obtaining direct access to the device via default login credentials or, otherwise, on laying hands on the unique password an attacker happened to know.
Attackers Replacing Firmware on @Cisco Routers: https://t.co/BPbw4C3926 via @Threatpost pic.twitter.com/kOZ1JkN11T
— Kaspersky (@kaspersky) September 15, 2015
The situation itself, should it be feasible, is a complete fiasco which creates a huge hole in the corporate security. Stealing login credentials per se would never be of interest to anyone, but in our situation it’s firmware modification which matters: it would give permanent access to the appliance and, subsequently, to a corporate network. The bottom line in this respect is obvious: if you live in the information security world, trust no one. By the way, the total number of infected routers (at least in its IPv4 part) hardly surpasses several dozens.
A serious bug in AirDrop data exchange system
News.
Where was I… Right, the rise of machines. In Terminator II’s fictional universe (I despise Terminator III and beyond) the humanity first created machines and then the latter rose against their masters. The initial purpose of building the machines was to make humans’ (well, the military’s) life easier. The robots were created to strike at targets pointed on the map of the world, or fight cyber attacks, etc.
This fictional model, although quite simplified, is happening now, in real life. It’s been ages since the only thing humans do to manage gadgets, connect to networks, or exchange information is pressing a button. Just as a user asks the question (or even before), the answer is programmed and ready.
Well, that is, in fact, what we call ‘progress’, but there is one fundamental flaw in it: we do not exercise any control over the interaction between our devices and the network. Take the wonderful AirDrop feature, for example. It was able to solve countless problems on its own: the user does not have to think of “pairing” or “connection to the access point” or “authorization”, the only thing he should do is to choose the addressee in the proximity and send the data. A vulnerability was bound to be discovered in this overly perfect connection model.
Bug in #iOS and #OSX Allows Writing of Arbitrary Files Via AirDrop via @threatpost https://t.co/J0U8WlyYQs #apple pic.twitter.com/2jMTsQTaqN
— Kaspersky (@kaspersky) September 16, 2015
Mike Dowd, an Australian researcher, demonstrated an attack, which allowed one to remotely overwrite data on the victim’s device with help of AirDrop. The only thing you need to do is send a specially crafted link to a mobile device (or even a Mac OS X computer). As soon as it lands on the targeted device, the user is prompted to either accept data or decline, but it does not matter anymore: the exploit has already done its job (quite similarly to StageFright in Android).
There is a certain limitation: the user should opt in for accepting data from all devices in proximity in AirDrop. But for the sake of convenience (!) this can be done even on a locked device. So, once the attacker gets physical access to the phone for a couple of seconds, it’s done. As a result, a culprit would be able to remotely install any apps on an iPhone. Of course, those rogue apps would enjoy basic privileges and would not be able to steal anything right away, but this is the story about other exploits, which are usually used to jailbreak devices.
The bug was patched in iOS 9.
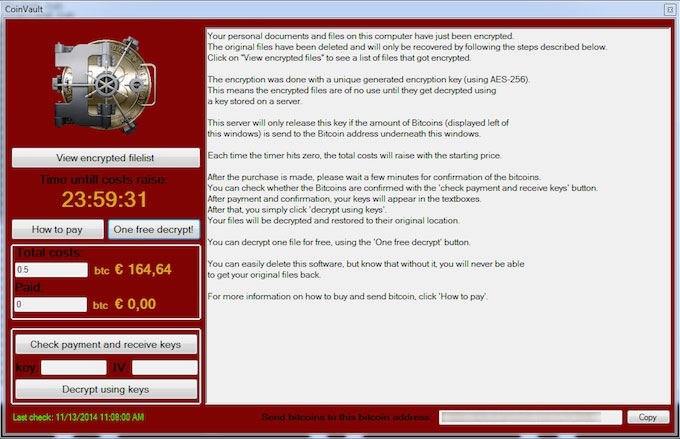
CoinVault ransomware creators arrested
News. The research by Kaspersky Lab. More research on CoinVault, including the concept of decryption without ransom.
While the machines don’t have enough intelligence for evil deeds, people are quite fine doing that in their stead. Real arrests following cases of ‘someone hacking someone’ are rarely heard of, to our dismay. Take the story we discussed above: researchers discovered modified router firmware with backdoors. But who did modified it and why? No idea.
Sometime there is a notion that anonymizing technologies in the Internet really make law enforcement a tedious, fruitless mission. Ransomware is one great example of such situation. Tor is used to anonymize C&C servers, and ransoms are paid in Bitcoins – seems as there’s nothing to do here.
Considering the above, we are very glad that good guys finally won. Two men were arrested in the Netherlands for allegedly creating the CoinVault cryptoloker. Kaspersky Lab’s experts also contributed to the operation, by researching the technology behind the attack.
CoinVault is not the most widespread locker, but it serves a perfect example of a very complex attack to research. Last year’s report demonstrated how actively the ransomware’s samples evade analysis: if you run the Trojan in a virtual machine or on a computer with WireShark or any similar software, the payload is blocked.
Security Week 38: #Cisco routers under attack, a #bug in #AirDrop, and the arrest of #CoinVault cryptohawkers
Tweet
Once the November report was published, it seemed that the cybercriminals behind the attack decided to lay low for a while, until the Panda Security researchers shared a couple of new samples. On gathering enough of indirect ‘evidence,’ Kaspersky’s specialists managed to decrypt the CoinVault’s victims’ data without them paying ransom.
A thorough analysis of the malicious code also helped to get the culprits. At first, experts discovered lines in ‘ideal Dutch’ whereas the common standard for coding malware is bad English, which makes it harder to localize the creator. Then, with help of the National Hi-Tech Crime Unit of the Dutch police, the C&C server was seized and those managing it identified.
Criminals behind #CoinVault ransomware are busted by Kaspersky Lab & Dutch police https://t.co/r0mP3LDIgr #infosec pic.twitter.com/X6ssm0c2UH
— Kaspersky (@kaspersky) September 17, 2015
The outcome of this story, I’d say, is that no anonymizing method used for crime activities is impenetrable. First, any new technology would ultimately get a counter method. Second, the main reason why cybercriminals are finally arrested is not a flaw in the technology, but a human factor, which would always be there.
What else happened:
A handful of bugs were discovered in PayPal and other services; they allow for authentication (even 2FA) bypass. As for PayPal, the blame is on a mobile API, which happened to be a bit less secure than expected.
The ‘Let’s encrypt’ initiative is now live, so website owners have another way to get a HTTPS certificate with a relatively less effort.
Google patched a bug in Android, which enabled lock screen bypass by entering a veeeeeeeeeeeeeeery_looooooooooooooooooong_paaaaaaaaaaaaaasword.
#Google Patches Latest #Android Lockscreen Bypass via @threatpost https://t.co/XqLsWIWRXd #mobile pic.twitter.com/7ioP8J3Rdz
— Kaspersky (@kaspersky) September 16, 2015
Oldies:
“Invader” and “Plastique” families
Resident viruses, extremely dangerous. They infect .COM and .EXE files (except COMMAND.COM) according to “Jerusalem” algorithm, as well as boot sectors of floppy drives and HDDs. They format an additional track on the floppy drive, and write themselves in sectors next to MBR on HDDs. Depending on their counters, they are able to run a null cycle when aborting in accordance with timer (int 8), erase data on drives, play music, decrypt and display the following texts:
“Invader” — “by Invader, Feng Chia U., Warning: Don’t run ACAD.EXE!”
“Plastique” — “PLASTIQUE 5.21 (plastic bomb) Copyright 1988-1990 by ABT Group (in association with Hammer LAB.) WARNING: DON’T RUN ACAD.EXE!”
They also include the text: “ACAD.EXECOMMAND.COM.COM.EXE”. They hijack Int 8, 9, 13h, 21h.
Quoted from “Computer viruses in MS-DOS” by Eugene Kaspersky, 1992. Page 104.
Disclaimer: this column reflects only the personal opinion of the author. It may coincide with Kaspersky Lab position, or it may not. Depends on luck.
 analysis
analysis





 Tips
Tips