The industry of infosec news (if there is one, after all), while not that similar to cry-wolf Vanity Fair type of media, is constantly agitated and always looking for the scoop. For instance, one of the most popular pieces of news on Threatpost last year was quite a mediocre one, covering the PNG vulnerability. It wasn’t even a vulnerability as such, just a method of obscuring a malicious code in the image’s metadata. Why did that happen? Someone (not us, obviously!) decided to announce the flaw as ‘You can infect your PC by looking at cat pics!!111’.
Of course, once some supermassive hole allowing culprits to infect millions of machines is discovered, I’d be happy to write about it, but those are nowhere to be seen. Many years have passed since Slammer: that sneaky little malware was able to infect a Windows XP PC in just 30 minutes and needed only connection to the Internet.
As for current software, it is not such an easy target (yet). But what if something dreadful happened? Something that would leave everyone awed, heartbroken and thinking about next-level PC/phone/fridge security, or, otherwise, every device or appliance would turn into a useless piece of plastic/metal/whatever to some evil maniac’s will. The world is on fire! Mamma mia! Porca Madonna! Ributtati all’età della pietra con solo carta e penna per archiviare e condividere informazioni!
Er. Epic fails in information security are plausible — take all those IoT things, for example — but are unlikely to happen. While we are waiting for some big kaboom, we might overlook some serious but down-to-Earth flaws, with which someone effectively wins and someone effectively loses. They are nothing but outstanding vulnerabilities — business as usual.
#Security Week 35: vulns in @Wordpress, @GitHub #DDoS, @Wyndham responsible for #breach, while @Target is not
Tweet
In today’s digest of information security news, we will cover three cases of routine vulnerabilities, which are massively and effectively exploited. Once again, the rules of the road: every week Threatpost’s team handpicks three important news stories, which I would restlessly comment. All previously aired episodes can be found here.
Hacked WordPress websites are used to deliver the Neutrino exploit pack
This news should be divided in two parts. The first parts would be about thousands blogs and websites based on the WordPress engine which is highly vulnerable. The second part would cover the methods used by hackers exploiting these vulnerabilities, the malware they use to infect users’ PCs and, ultimately, the way they extract money from their hacking scheme.
Now, WordPress. It’s like a web-based Windows. It’s a very popular web engine with an extensive plug-in system, which, by design, enjoys high level of attention from cybercriminals. Just look at this year’s news coverage (and that’s not all!):
- A Zero-day vulnerability, in a plug-in.
- A flaw in random (not really) number generator, which theoretically allows to figure out the token used during the password change procedure.
- An SQL inject, in a plug-in.
- Again, a SQL inject, in a plug-in.
- A XSS vuln, in a plug-in.
- A Zero-day in WordPress itself, JavaScript injection via commentaries. The patch is available in v 4.2.1.
- Vulnerabilities in two plug-ins.
- A XSS vuln in WordPress itself, patched in v 4.2.3.
- Vulns in three plug-ins.

That’s the picture. Zscaler researchers spotted a massive breach of exposed WordPress websites (v 4.2 and lower). V 4.2, by the way, was launched as a short time ago as in April this year, which makes one wonder how bad it is for those who have not updated their sites for at least over a year. After hacking the websites, culprits would inject an iframe, then set up the Neutrino exploit pack, and then infect PCs with malware. By now, there are over 2,500 affected websites, which is not much compared to the entire Internet, yet is enough to make the lives of tens of thousands users miserable.
What are exploits and why they are so scary? https://t.co/tulx05JN0q pic.twitter.com/Z5A4itfh7E
— Kaspersky (@kaspersky) July 31, 2015
Going further, the exploit pack uses a bug in Adobe Flash, which leaked as a part of the notorious breach of Hacking Team. Thus obtaining a capability to execute a code on the victim’s machine, attackers deploy the Cryptowall locker – a piece of the ransomware which has been in the wild for over a year and demands ransoms of over $500 for a decryption key.
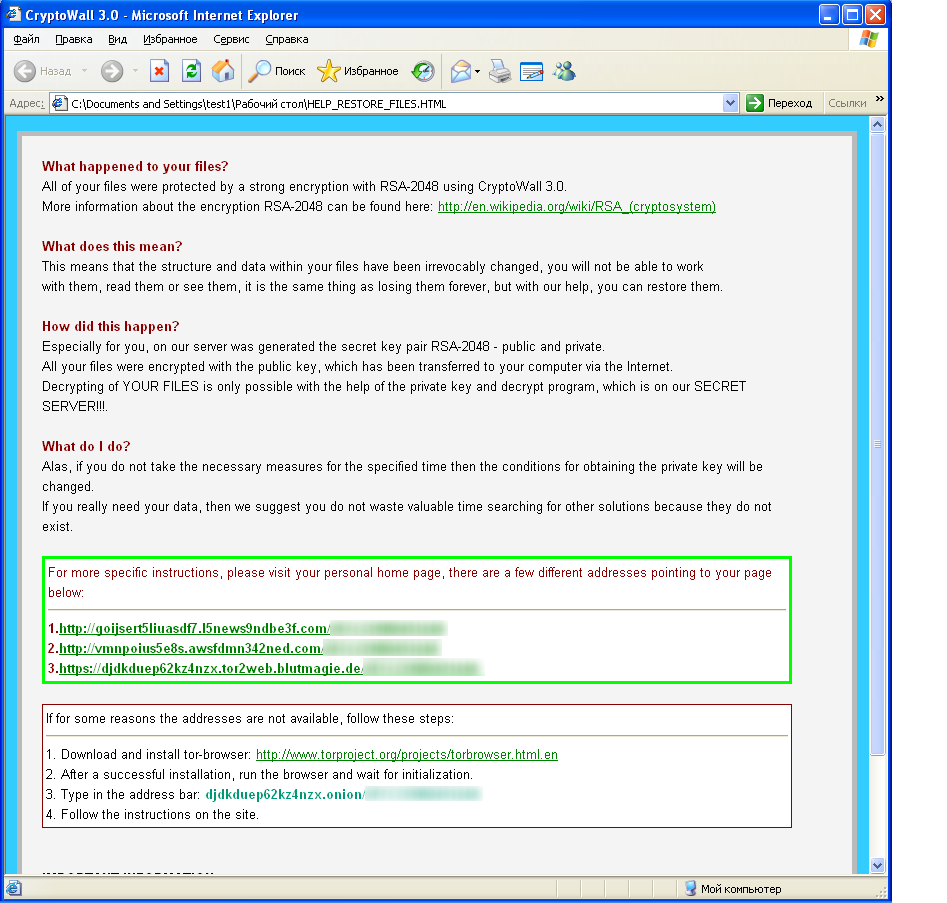
[Caption: All your files belong to us. To learn more about ransomware, check here]
Imagine you own a small business and a couple of years ago you purchased a turnkey website from a third party supplier, so you have no idea about the type of engine your website runs on. Compared to some massive stuff like sneaking a malicious code through banners of, say Yahoo, it’s peanuts, but hundreds of infected sites like that can generate multi-million dollars in revenue (or losses, depending on the point of view).
From the security standpoint, this attack is not extraordinary. It looks as a collection of small incidents: there are a number of vulnerabilities in just one website engine (or its plug-ins); someone will constantly hack those sites and deploy an exploit pack; someone will develop those exploit-packs, using the data obtained from the company running a questionable business of trading vulns and ultimately unable to guard its own secrets.
Someone will use outdated Flash, and someone will collect money from desperate people who are not able to access their own files. Taken separately, each of the precedents is not a big deal, but collectively they form quite a dreadful picture.
Curiously, researchers have previously noted the spike in Neutrino’s traffic, by expense of its rival — Angler, with no particular idea why at the moment. It seems that besides making money, people standing behind those cybercriminal operations had something of a fray finding out who’s the boss.
GitHub is DDoS-ed. Again
In reality, it’s quite easy to bring down the number of software vulnerabilities. What you need to do is just prohibit coders from coding. Well, that’s a disputable way, but someone, it appears, wanted to do that, disrupting GitHub’s operations by executing a DDoS attack on one of the software industry’s most renowned repository.
The news is not breaking, anyway: The attack started early in the morning, was discovered and taken down three hours later, the culprit behind the attack remains unknown. *Yawn* Bo-ring. So, why did that news attract everyone’s attention? The reason is that GitHub was heavily DDoSed for over a week back in March, so no wonder everyone overreacted.

The March attack was curious. Experts were under a strong impression of malware traffic being somehow connected to China’s Baidu search engine. It’s like an iframe appeared on Google’s main page and redirected the traffic to the victim’s website.
This helps to bring any website down, but it does not sound anything like possible. Or does it? Quite unlikely, and it seems in that March attack Baidu was not responsible for anything, and the ‘bonus’ was attached to Chinese users somewhere else and not on Baidu.
Where exactly it did, remains an open question. Maybe it was a usual way of infecting users and then luring them into downloading a rogue script when they access popular website. Or, maybe, the swap happened somewhere else.
Google have provided detailed analysis of the recent Github attack – http://t.co/F75hTyzp2s pic.twitter.com/HJPMMg0InZ
— Kaspersky (@kaspersky) April 27, 2015
For instance, it could happen somewhere between outside world’s Internet and Chinese Internet, where the Great Chinese Firewall resides. In this case, those who access Chinese websites outside China might unintendedly do attackers’ bidding: the response from the server would bear a malicious script, which would be used against GitHub projects from the victim’s PC.
By the way, the affected GitHub projects seemed to be hand-picked: the targets were two projects which would allow bypass of the Great Firewall and access to the content banned in China. That type of attack even got its own name – ‘Man-on-the-Side.’ The aftermath of the story: HTTPS rules.
American hotel chain responsible for a data breach
News.
The news is totally about law and order, but it’s quite important. Seven years ago, the Wyndham hotel chain’s IT infrastructure was hacked, with over 600,000 customer records stolen. Leaked credit card data allowed culprits to strip the card members of over $10 million. The breach was as simple as this: find one exposed computer in one of the hotels, get the admin password, get access to… well, to everything.
From the technical point of view, the hack was an epic fail of the hotel’s security team: let alone client data, why on Earth would one store credit cards numbers unencrypted? The US Federal Trade Commission was pretty upset with Wyndham, claiming the company did not comply with its own privacy policies.
There was a promise to provide ‘standard-based protection’ (like deploying a firewall or encrypting data) which the hotels did not live up to. As it turned to be, there was no firewall and no encryption. There were default passwords on PCs, no security audit ever, and no plan B. The FTC tried to punish the company, with the very first legal case revolving, awkwardly, around whether the FTC has a right to do that or not. After a series of iterations, the parties came to a conclusion that the FTC is empowered to do that.
Court Rules FTC Has Authority to Punish Wyndham Over Breaches – http://t.co/pmgYUjbGEe
— Threatpost (@threatpost) August 24, 2015
That sounds interesting. Say, a company faced an APT attack, the one that presupposes the use of advanced hacking techniques and helps preserve unsolicited access for a long time. It’s all clear: the company took all measures necessary, but they got bypassed, and nothing can help here.
But it’s another story when the attack was not advanced at all, but very persistent, just because the infrastructure was completely insecure to any threat. The ruling of the court adds a bit of headache to American companies in terms of compliance. Usually rules of compliance are applied to credit card processing systems, but it appears that now it would be applied to all aspects of protecting personal data.
Maybe, it’s for the best. However, technologies and methods of protection should be created anywhere but in courtrooms. Courts serve to fine-tune the definitions. And yet one more thing – Data should be encrypted. It sounds completely down-to-Earth like “one should do backups.” Still, data SHOULD be encrypted.
By the way, Target, which clients suffered a more impactful breach, was not fined, as per the FTC’s ruling.
Target Says SEC Won’t Pursue Enforcement Action as a Result of Data Breach – http://t.co/OwsXc1ZBHK
— Threatpost (@threatpost) August 27, 2015
What else happened:
American researchers scanned over 400,000 apps on Google Play, finding 7.6% of them potentially dangerous. It does not correspond to Google’s own assessment: according to Google, the chances of infection when downloading apps exclusively from Google Play are just 0.15%. At the same time, the approach used by the researchers is vague itself: they analyze the code, find non-standard deployment and automatically list the code as potentially dangerous.
Scanner Finds Malicious Android Apps at Scale: https://t.co/53MoLU2nRz via @Threatpost pic.twitter.com/7HrpJdSoz9
— Kaspersky (@kaspersky) August 27, 2015
In Russia, ransomware is distributed via email. That’s not news. The news is that now the attackers use fake “Payment overdue” notifications from banks. These guys know how to use any situation in their advantage, including financial crisis.
According to research, >40% of CryptoLocker victims paid #ransomware #infosec http://t.co/Lnb4Rq7foJ #whitepaper pic.twitter.com/wrxC9Rq1ZH
— Kaspersky (@kaspersky) August 24, 2015
Apple closed the vulnerability which helped any app to track users even with time limits set up in the system. It’s funny that bootlegging such kind of bug through App Store moderation is a lot easier than in case of a purely malicious app.
Patched Ins0mnia Vulnerability Keeps Malicious #iOS Apps Hidden: https://t.co/LVLKMC8NcX #apple via @threatpost pic.twitter.com/jtZM9WXZYl
— Kaspersky (@kaspersky) August 26, 2015
Oldies:
Den-Zuk

A very dangerous virus, length of 9 sectors. It infects disk’ s Boot sector when called (int 13h, ah = 2,3,4,5). If the second part of the virus is saved on the disk, no security checks are done, letting the virus destroy a part of the information on the disk (40th track).
Hijacks int 9 and 13h. After the ‘warm’ reboot, it inputs its name (Den Zuk) on the screen. Changes the tag of the infected disk to “YC1ERP”. Does not possess destructive functions yet is very dangerous, since it can destroy data on the 40th track of the disk. Includes texts: “Welcome to the C l u b — The HackerS — Hackin’ All The Time”, “The HackerS”.
Quoted from “Computer viruses in MS-DOS” by Eugene Kaspersky, 1992. Page 99.
Disclaimer: this column reflects only the personal opinion of the author. It may coincide with Kaspersky Lab position, or it may not. Depends on luck.
 breach
breach

 Tips
Tips