One of the biggest no-nos in the business world is talking about age. However, I found myself in a session about just that at RSA Conference 2020.
Before your HR radar goes off, this is not about ageism or other common prejudices. It was a talk from Ben Smith, RSA’s Field CTO (US), and it focused more on how today’s workplace really comprises four well-defined generations (traditionalists, baby boomers, Generation X, and millennials), not to mention “cuspers,” or people straddling two of the traditional buckets, who tend to share some traits of both.
The reason this is important for the business world, and the security world in particular, is that the conversation is data-driven, not hypothetical; generations really do consume technology in different ways.
So, when building a security program, you have to understand that one size doesn’t fit all. Smith provided a whole bunch more theory, which you can hear about in the full talk.
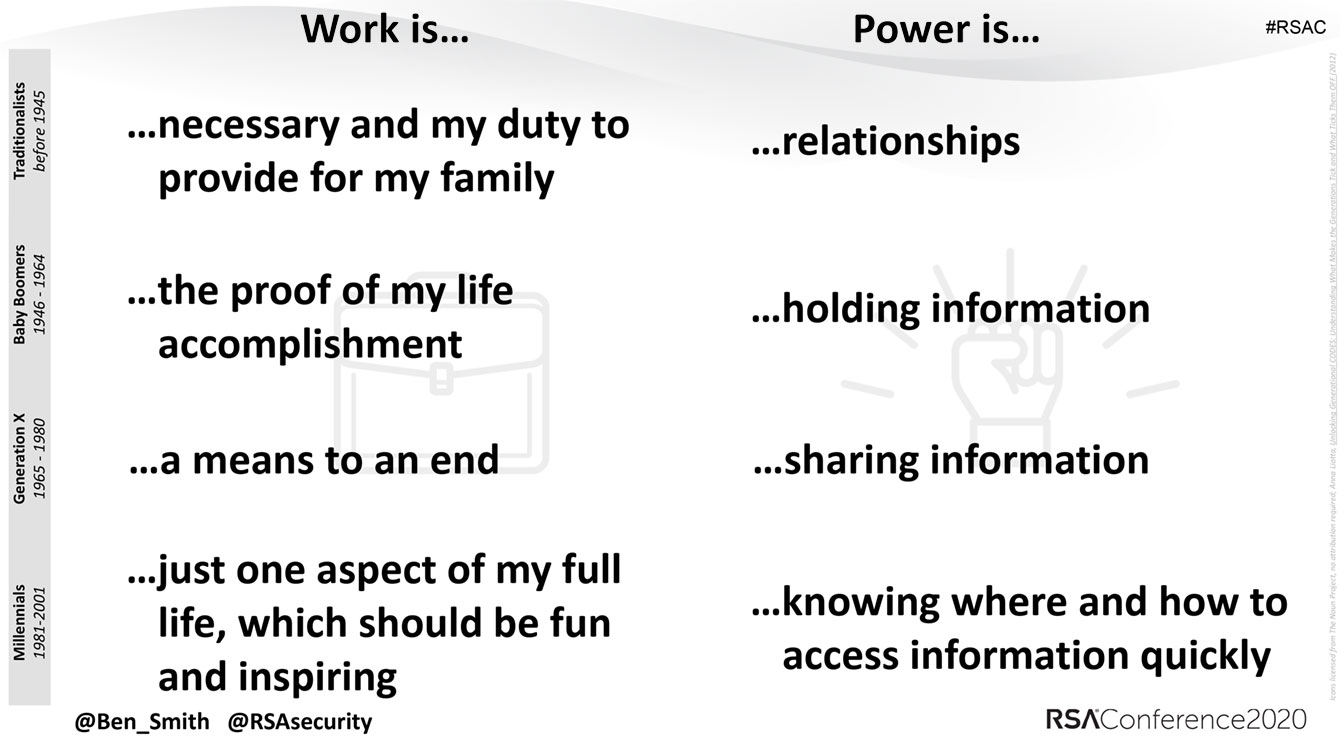
As you can see, the bottom three — the youngest — generations focus on information, and they are dynamically opposed. Smith pointed out other generational gaps as well, from having electronics in the bedroom to where work occurs, work/life boundaries, digital media consumption, time on social networks, and more.
With that said, there’s a common denominator, and it can help you build the core of your security program. In the slide below, what really stood out to me as it relates to work and security is the concept of having no on/off switch. How should your security training accommodate that?
Remote work. Understand that there is no more 9-to-5 and that people are always working away from the office. When building out a strategy, be sure to address the risks of working remotely, along with best practices on how to work within the company’s policies. For example, you may need to mandate the use of a VPN on public Wi-Fi networks, not storing sensitive documents on public file-sharing sites, define what apps and actions are allowed on work devices, and so on.
Social engineering. People are becoming more familiar with the threat of fake social network accounts pretending to belong to family or loved ones. That concept is important in the workplace as well, and it should be a part of workplace awareness campaigns. No one wants to be the one who transfers a few hundred thousand dollars to the wrong account because someone pretending to be the CEO asked for an urgent money transfer.
Data sharing. These days, you can avoid having to create website passwords by using your social networking credentials instead — and some folks may not be fully aware of the risks, or realize what types of data they are giving up. When looking at your educational program, consider this a key point. Also, add info on which types of sites are not OK to set up using work e-mail addresses — think dating, gambling, and other types of sites that have nothing to do with your business.
Multidevice usage. The bring your own device (BYOD) trend has been a pain for IT and security managers for quite a few years now. Like it or not, now you have to live with it: People are conducting business on their phones, laptops, or tablets and doing personal tasks on work devices. Policies can’t really stop that, but you can educate employees on best practices, what they may and may not do, and how to secure their devices.
Gamification. Anyone who uses the Web or plays games at all is familiar with gamification, even if they don’t necessarily know it by that name: People get points for doing X, and the top performers are rewarded with Y. When planning your security training, consider working gamification into the program, and how you can reward people for being your internal champions. Security doesn’t have to be only about sticks; you can use carrots as well.
Every workplace is different, and the way your team responds will not be the same as the company across the street, but taking into consideration concepts that speak to the different ways working generations interact with technology will help you with security planning that can benefit everyone.
 RSAC
RSAC


 Tips
Tips