It’s been about a year since kids returned to in-person school following a long stretch of virtual learning due to the pandemic. Parents, students and schools are now quite used to the integration of technology in learning; with many students bringing school-issued computers home with them to complete assignments.
Despite cybersecurity measures put in place by many schools, cybercriminals have continued to target these institutions. And even though 2023 has just started, we’ve already seen ransomware attacks hit schools across the U.S. from Tucson to Nantucket, as well as across the pond in the U.K. While any sort of cybersecurity incident is unfortunate, it’s encouraging to see that a growing number of schools are focusing on protecting student data.
But, you might be thinking, what kind of data are cybercriminals stealing and holding hostage? Class schedules and grades? Unfortunately, it’s more serious than that. If schools refuse to pay the ransom, cybercriminals are threatening to release Social Security numbers, banking information and even medical histories.
Surveying the Parents
In 2021, we surveyed parents of school-aged children, once in May and once in October, on their attitudes and experiences with regards to cyberattacks on American schools. This past October, we wanted to see how parents’ experiences have changed and what the ransomware landscape now looks like in schools. While the findings show an increase in ransomware activity, parents are still taking an active role (although slightly less active than in May 2021) in educating their child on practicing good cyber-hygiene, such as using strong passwords.
So, What’s Changed?
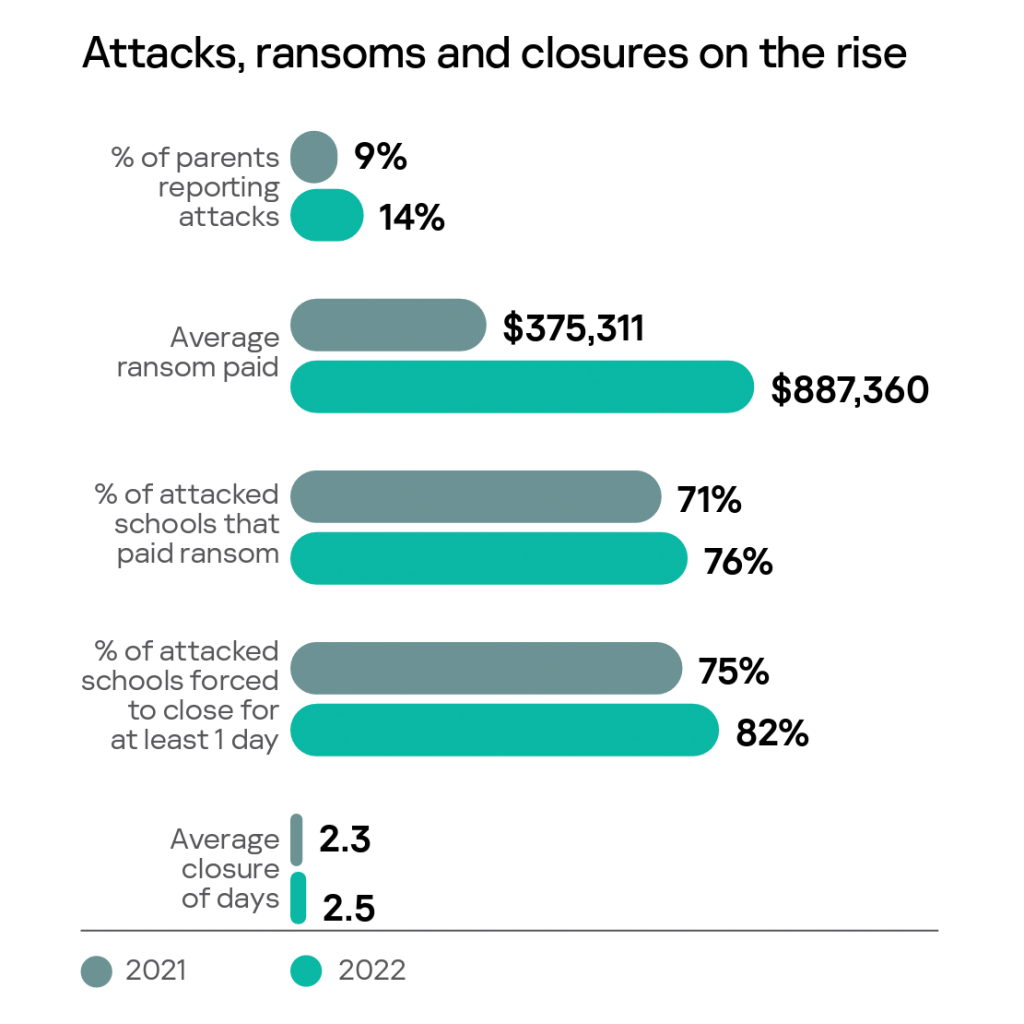
Why do ransomware attacks continue to occur? Part of it is due to victims continuing to pay ransoms. And whilst schools may want to prevent their vulnerable data from leaking, paying the ransom only encourages bad actors to continue their attack. So how has the impact of these attacks changed over the span of a year?
- More parents (14%) said their child’s school was hit with a ransomware attack while they were a student there. This was up from 9% in October 2021.
- Parents reporting an attack said their school district paid an average ransom of $887,360 to the attackers. In 2021, the figure was just $375,311.
- On the high end of ransoms, 10% of parents reporting an attack said the district paid more than $1M; up from 3.7% in 2021.
- School closures also increased with 82% of parents reporting attacks said their school was forced to close for at least 1 day, up from 75% in October 2021. The average closure was 2.5 days, up slightly from 2.3 days reported last year.
Despite many schools still paying out ransoms, parents are largely content with how schools are responding to ransomware attacks. Of parents reporting attacks, 82% were satisfied with their school’s response to the attack, up from 80% in October 2021. Confidence in a school’s ability to handle future cybersecurity incidents successfully rose significantly from 68% in May 2021 to 81%.
However, there’s still a lot more that schools could be doing in terms of preventing and responding to ransomware attacks. More than 68% of parents who’ve reported an attack said they weren’t immediately notified by the school, with notifications coming from social media, their child, local news or other sources. So what steps should schools be taking?
As ransomware attacks continue to hit schools, we strongly urge school administrators to employ some additional security mechanisms, such as:
- Multi-factor authentication
- Regular software updates
- Training staff and students to spot phishing attacks
It doesn’t look like ransomware attacks are slowing down anytime soon, but you can do your best to stay as safe and secure as possible.
 Ransomware
Ransomware

 Tips
Tips