Ransomware has hit the news in a big way lately. Is this malware just another hot-button topic that everybody will forget about as soon as a new big threat emerges? Unfortunately, that’s unlikely: Ransomware infections are reaching pandemic rates, and this type of malware is not going to vanish any time soon. We are not trying to scare you — well, we are, but not for kicks. Have a look at the statistics gathered by Kaspersky Security Network and you’ll see — we are facing a really dangerous threat.
The first wave: blockers
Ransomware’s history can be divided into two parts: before encryption and after it. Blockers were the ancestors of modern cryptors. This malware blocked access to a user’s operating system or browser until the victim paid a moderate ransom. Paying typically required sending an SMS to a short code (an alternative to a telephone number, often used for charity giving) or transferring money to an e-wallet.
This malware used to be rather profitable — and criminals used it widely. Naturally, security experts and law enforcement agencies tackled the problem quickly.
They found an elegant solution and struck at the cybercriminals’ business from the side of payment systems. When the regulatory rules of electronic payments changed, cybercrime became simultaneously less profitable and more risky’ and many culprits got busted.
#Tip of the week: Fighting screen lockers with @kaspersky products https://t.co/SAS4x4ve9o pic.twitter.com/11SGH4e8nR
— Kaspersky (@kaspersky) June 3, 2016
Second wave: cryptors
A couple of years ago, everything changed. Bitcoin became widespread and rather popular among cybercriminals. The cryptocurrency is simultaneously a digital asset and a payment system that is impossible to trace or regulate. Of course, criminals loved it. In addition, they switched to a new approach: Instead of blocking access to browsers and operating systems, they began encrypting files stored on victims’ hard drives.
Why is the encryption approach so efficient? Private files are unique, so users cannot replace them by reinstalling an operating system. If the cryptor uses strong encryption, people become unable to restore (in other words, to decrypt) their files. This has empowered criminals to demand huge ransoms: several hundred dollars from consumers and thousands from companies and corporations.
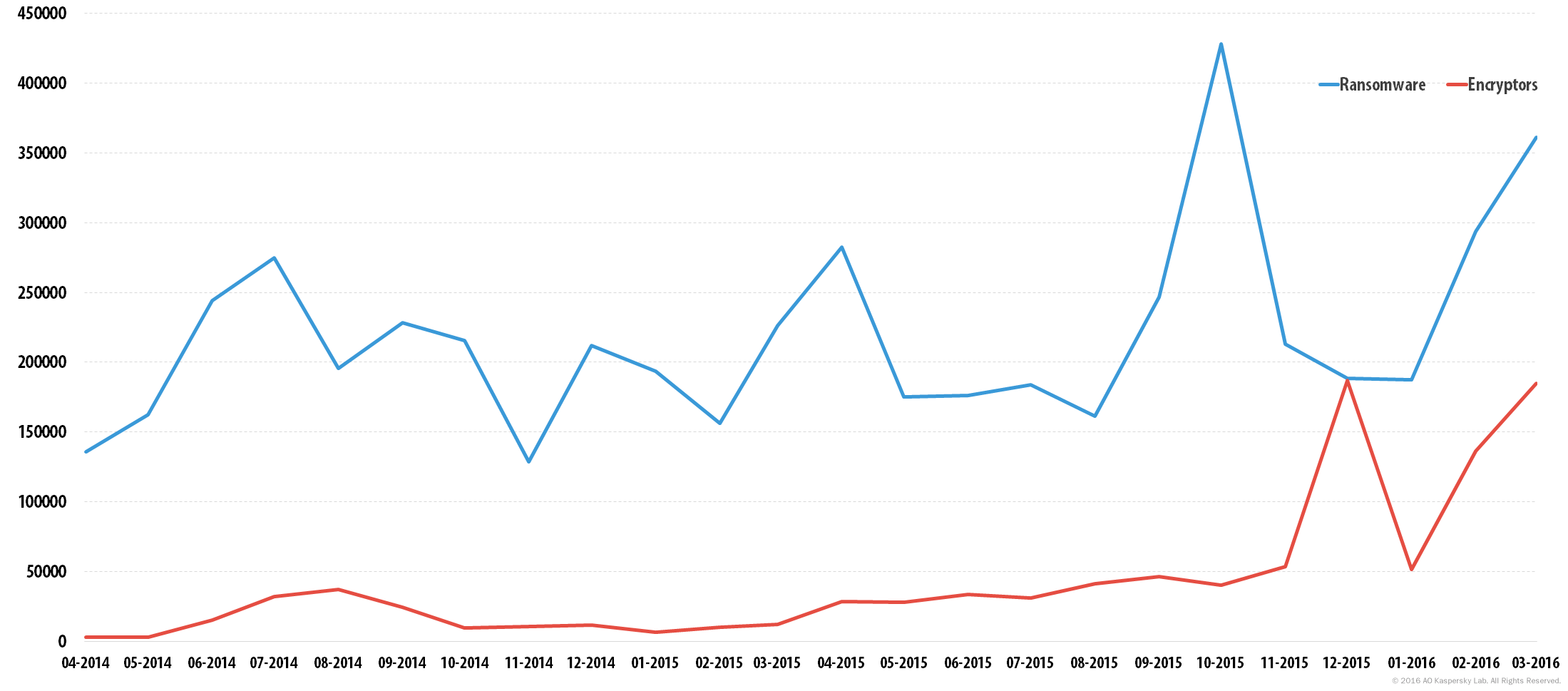
For a time, that young generation of encryptors was less widespread than the older blockers. But it didn’t take criminals long to switch to the new malware. By the end of 2015 the number of ransomware attacks was increasing like an avalanche.
According to our analysis, based on Kaspersky Security Network statistics, in one year the number of attacks increased more than fivefold: from 131,111 attempts to infect our users in 2014–2015 to 718,536 in 2015–2016.
Global distribution of attacks and the most active ransomware families
The top 10 countries for ransomware are India, Russia, Kazakhstan, Italy, Germany, Vietnam, Algeria, Brazil, Ukraine, and the United States. However, the ransomware that people face in India, Algeria, Russia, Vietnam, Kazakhstan, Ukraine, and Brazil is mostly old and relatively mild versions of blockers. In the US, however, 40% of ransomware victims are attacked by dangerous cryptors. In Italy and Germany, the situation is even worse: in these countries the word ‘ransomware’ became synonymous to the word ‘cryptor’.
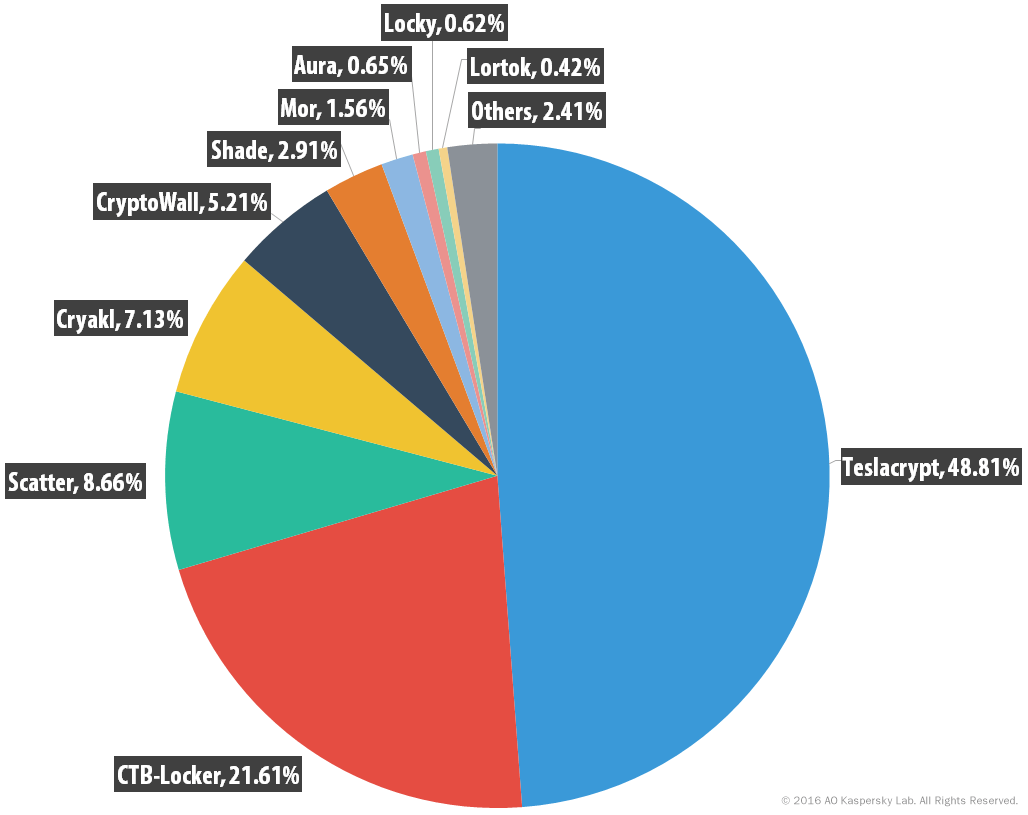
In 2015–2016, four racketeering Trojans were the most active: TeslaCrypt (almost half of all attacks, but fortunately, we have a decryptor for it), CTB-Locker, Scatter, and Cryakl (we also decrypt Cryakl). Those four families share almost 80% of the “market”.
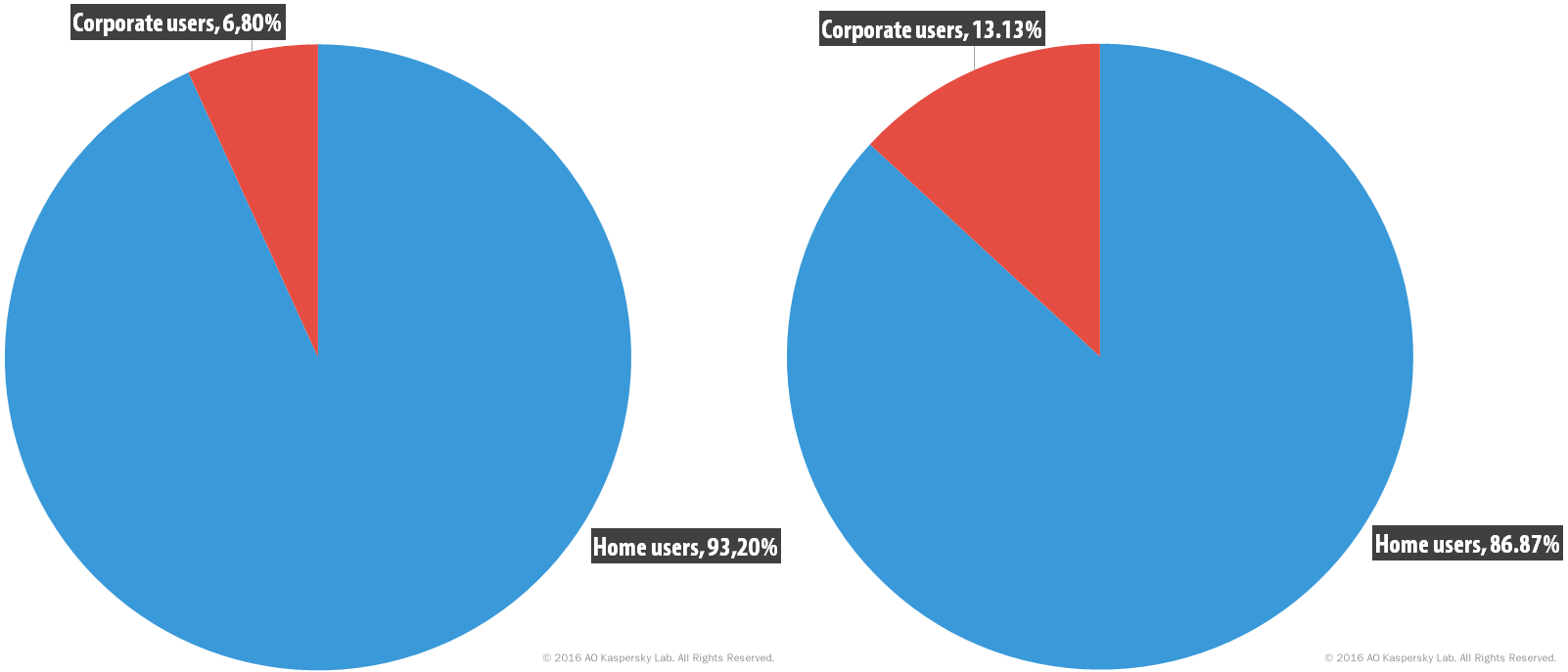
Another noteworthy fact: Initially, ransomware targeted mostly home users. After the “upgrade” to encryption, it started going after companies as well: The share of corporate users attacked with ransomware more than doubled from 2014–2015 to 2015–2016, from 6.8% to 13.13%.
You can read further about the evolution of ransomware from 2014 to 2016 on securelist.com.
How to stay protected
1. Make backups regularly.
2. Use reliable security solutions. For example, Kaspersky Internet Security, as well as all of our other flagship solutions, detects and blocks all known ransomware families. It also has a built-in module that can protect you from the latest and yet-unknown cryptors.
3. Update your software on a regular basis: Patches fix software vulnerabilities, and the fewer bugs you have, the harder it becomes to infect your system.
4. Keep up with cybersecurity news here on Kaspersky Daily and on threatpost.com — alert today is alive tomorrow. Be sure to tell your friends, relatives, and colleagues about the latest threats.
5. If you’ve already fallen victim to ransomware, don’t pay any ransom without giving other options a try. If you’ve come across a blocker, use our free WindowsUnlocker tool. If you are fighting against a cryptor, check NoRansom.kaspersky.com to see if there is a cure for that as well.
 blockers
blockers