Mobile World Congress is always about smartphones. But if you stop looking for them and take a look from a different angle — you’ll find a lot of other stuff. As we headed to MWC 2016 with that goal in mind – looking with a different lens— unfortunately what we saw at the conference was quite scary. Read along to see why.
Mobile payments: obsession with convenience
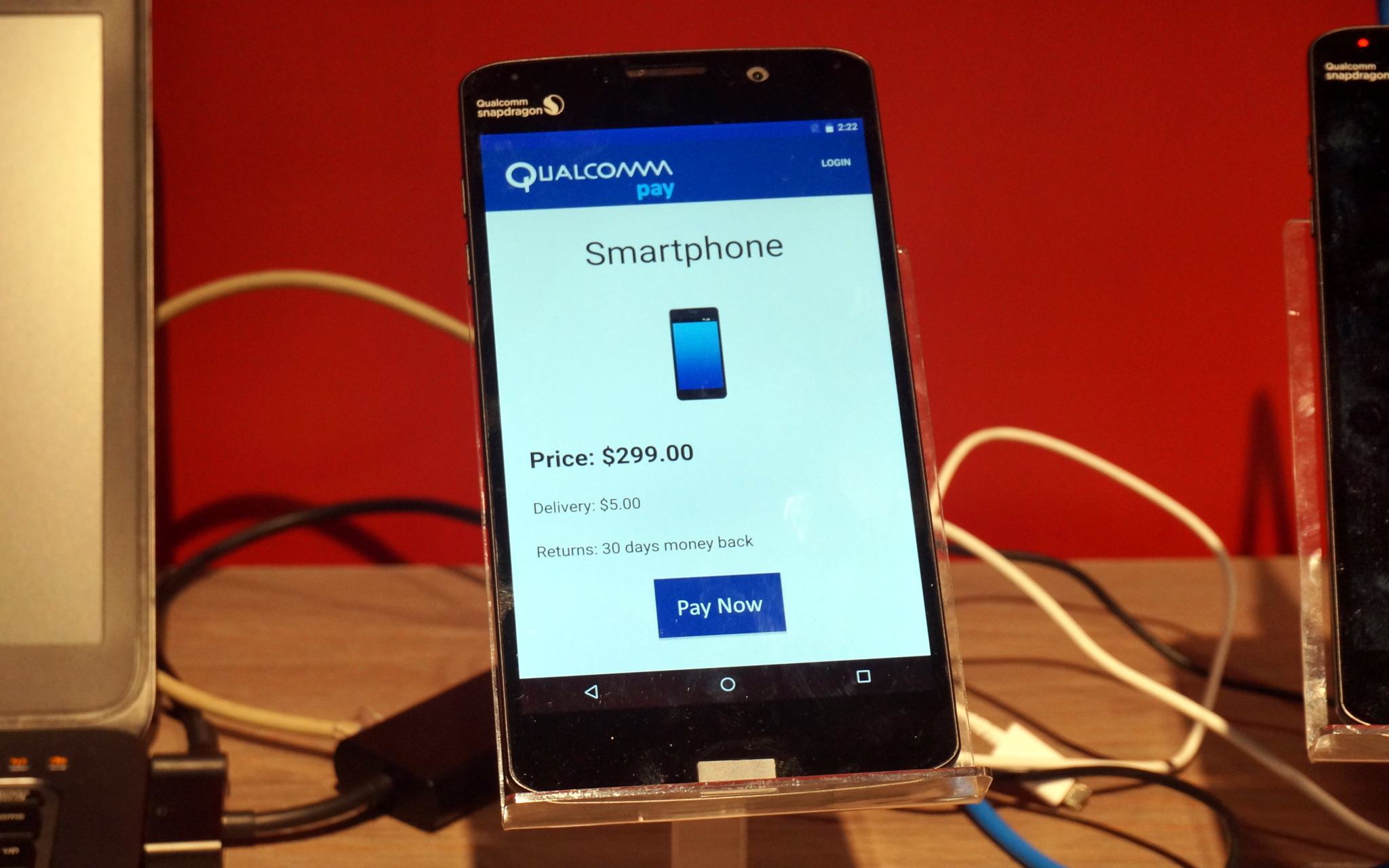
It seems that a lot of companies have become obsessed with mobile payments — and there were many announcements during MWC were dedicated to that theme. A recurring theme was that they were looking for mobile payments to become and more convenient. What was not emphasized in the spin cycle was that they were not trending on becoming more secure.
For example, Samsung revealed that Samsung Pay is coming to several new countries including Brazil, UK, Canada, China and Spain. While we have no reason to believe that Samsung Pay is not safe (while we do for Apple Pay). It is worth noting that a group of hackers broke into LoopPay recently. This is of note as this is the system behind Samsung Pay; acquired by the Korean company a year ago.
#SamsungPay: An Early Examination of Security: https://t.co/PTWVfwi7wl #Samsung #mobilepayments pic.twitter.com/Tx0J56ZsI8
— Kaspersky (@kaspersky) March 13, 2015
Samsung claims that those hackers wanted to steal the technology in order to create a similar system of their own, but there is no guarantee that they do not possess enough data to compromise Samsung Pay’s users’ accounts.
https://www.instagram.com/p/7LgOaiv0Gl/
A few days before MWC Qualcomm and Tencet announced that a Qualcomm-based phone now supports biometric fingerprint authentication for payments in WeChat, the biggest Chinese messenger. While Qualcomm accentuates that these payments are super secure because of the Qualcomm Heaven framework, we all know that there are certain problems with fingerprint scanner security. So we can only hope that Qualcomm and Tencent have created a really worthy payment system, but it’s quite possible that hackers will find a way to compromise it — as they usually do with new payment systems.
VISA is taking cautious steps towards the same direction. While one of the two biggest credit card companies is quite fond of contactless payments (e.g VISA PayWave), it’s engineers try to triple check everything to be sure their technology is absolutely secure — and that’s really music to our ears. Yet the concept of iris authentication is already approved within the company, and at MWC they showcased a fingerprint authentication system. Fortunately for everyone, it is in its early testing stage, and engineers are even thinking of making a two-factor authentication system using both a finger and an iris.
Great piece from our #MWC16 panel hosts @kaspersky on #cybersecurity and the #tokenisation approach: https://t.co/7cqd8gerhj
— VisaNewsEurope (@VisaNewsEurope) February 25, 2016
We asked the man working on VISA’s booth for his opinion on spoofing iris and fingerprint recognition. No, he’s not aware if it’s even possible. He did assure us that if it turns out that such things are actually possible, he’s quite certain that researchers would have to think of some additional security — for example, monitoring the blood flow in the veins which also has a unique pattern for every human.
VISA’s main rival Mastercard stole the show by introducing the selfie-payments. Yes, you read it right: the selfie-payments. It means using selfies instead of passwords — and Mastercard claims that would enhance security because people tend to treat their passwords the wrong way: write them down and lose them or re-use them.
The video above shows that the system requires you not only to be in front of the camera but also to blink, so it cannot be tricked by a simple printed photo. But we’re sure hackers all over the world had accepted this as a challenge. Probably a video would be enough to cheat the system.
How easy is it for hackers to steal your face? https://t.co/SGtYtE1y63 #digitalidentity pic.twitter.com/Cz85TxEkYt
— Kaspersky (@kaspersky) October 28, 2015
Fingerprint sensors: stagnation
Biometrics is becoming a common things, fingerprint readers can now be found not only in the flagship phones, but also in those in mid to lower tiered price buckets. Huawei has even integrated a fingerprint reader in its new 2-in-1 Windows-based laptop/tablet MateBook.
#Mobile fingerprint sensors: more or less secure? https://t.co/m3eqgNRcrI #security pic.twitter.com/Asx52xPiao
— Kaspersky (@kaspersky) January 21, 2016
At MWC, we talked with representatives from two fingerprint reader manufacturers. The new scanner that Synaptics had announced is as secure as possible: the data is encrypted, and Synaptics highly recommends that cellphone manufacturers use the special ARM Trustzone secure environment for processing this data.
At the same time the other fingerprint manufacturer, NEXT, has two types of sensors, and one of them does not encrypt the data. And NEXT does not stress the necessity of using secure sandboxes for biometric data, but is very aggressive in terms of pricing it’s products as low as possible. Since not many manufacturers consider security their top priority, we apprehend that these cheap and insecure NEXT fingerprint scanners may end up in a lot of devices, and that would make the aforementioned contactless payments with smartphones even less secure than they are now.
Connected cars
First connected, and then self-driving cars are certainly going to be our future. But for now car manufacturers are paying way more attention to on-the-road behavior and safety of these cars than to their cybersecurity. And researchers have already shown that cybersecurity is a must for every car that is exposed to Internet.
#BlackHat 2015: The full story of how that Jeep was hacked https://t.co/y0d6k8UE4n #bhUSA pic.twitter.com/SWulPz4Et7
— Kaspersky (@kaspersky) August 7, 2015
Samsung and Sony have both introduced their ‘make-a-connected-car-yourself’ kits that are compatible even with old cars. The one Sony has announced is connected via USB and Bluetooth and seems to be more like a controller for the navigation app in you phone. Compromising it probably won’t give the hacker much more that the destination you are heading, the music you are listening and the way to change those things. Nothing too scary.
But Samsung has introduced a more complex device. One of its functions is to analyze the car’s vital signs, while the other is to serve as an in-car Wi-Fi hotspot. That means that this device is connected to an OBD II port in the car and to the LTE network at the same time. We already know that a car can be hacked remotely using OBD II, and Samsung is making that even easier by connecting it directly to the Internet.
#Progressive #Snapshot Exposes Drivers to Car Hacking: https://t.co/c8I8lc1zu0
— Kaspersky (@kaspersky) January 27, 2015
A car can be super safe and have the highest grades in crash tests, but if it is prone to someone snagging the control and remotely gunning the engine — in certain circumstances all that safety is of almost no good.
Not everything was super-scary at MWC 2016 — there were really interesting devices and good news. But all in all this year’s Mobile World Congress was definitely about everything becoming connected, and the more things are exposed to the Internet, the more ways are opened to somehow hack and compromise them. We hope that the next MWC will place more emphasis on securing all these connections. Yet we realize that the next Black Hat definitely will be about hacking all this connected stuff.
 biometrics
biometrics






 Tips
Tips