When a conversation touches on credential theft, e-mail messages with phishing links tend to come up first. However, those messages represent just one means of obtaining user names and passwords for various online services. Scammers still mail links to spyware regularly, too. One trick they use to disguise those links is including an image that appears to be an attachment.
E-mail with a malicious link
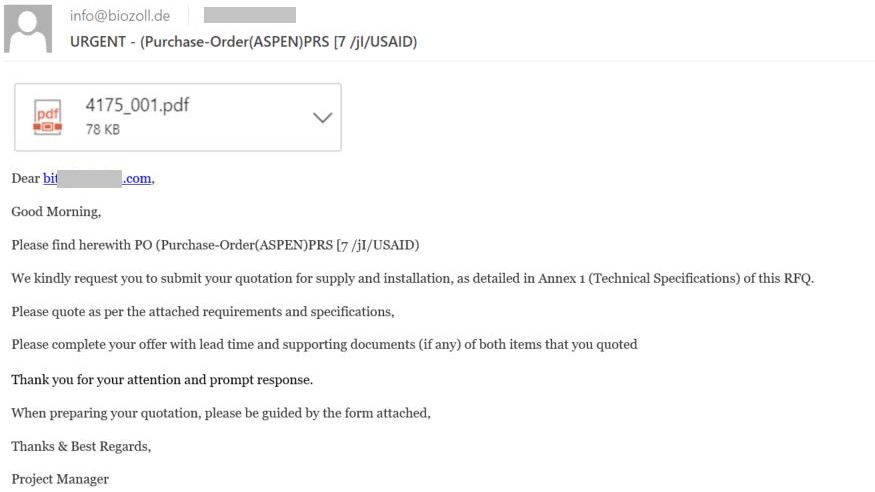
Today, we’re looking at a targeted e-mail attack. The cybercriminals in question made their e-mail look credible, sending an RFQ (request for quotation) to a provider of industrial services and equipment vendor, with guidelines attached.
Industrial companies receive such requests fairly often, and account managers will typically open the guideline document and prepare a proposal, glossing over any slight discrepancies such as differences between the domain name and the sender’s signature. What we are interested in, here, is how cybercriminals get recipients to run the malware. Here’s what the e-mail looks like.
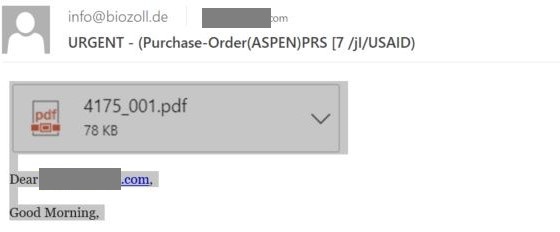
See the attached PDF? Well, what you’re looking at is not an attachment at all. Outlook does display e-mail attachments like this, but here you’ll find a number of differences:
- The attachment icon should match the application associated with PDF files in your system. If not, then either it’s not an attachment or whatever’s attached is not a PDF file;
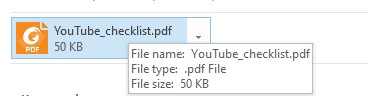
- Details about the file — name, type, size — should appear if you hover your mouse over a real attachment. You shouldn’t instead see a link to some shady website;
- The arrow next to the file name should be highlighted and function as a button that brings up a context menu;
- The attachment should appear in a separate block, not in the body of the e-mail, something like this:
In fact, this object disguised as a PDF attachment is just a regular image. If you try selecting parts of the message with your mouse or using Ctrl-A to select all, that much will be apparent.
The image obscures a hyperlink to a malicious program. Clicking the link downloads a spyware Trojan.
Attack payload
In this particular case, the malicious link pointed to an archive named Swift_Banco_Unicredit_Wire_sepa_export_000937499223.cab, which contained a loader for a Trojan Kaspersky identifies as Trojan-Spy.Win32.Noon, a fairly commonplace spyware Trojan. Known since 2017, it enables attackers to steal passwords and other information from input forms.
How to stay safe
To keep spyware Trojans from harming your company, install a reliable security solution on every device with Internet access to prevent malware from running.
Additionally, train your employees to detect cybercriminals’ tricks in e-mails.
 e-mail
e-mail

 Tips
Tips