As Google’s mobile platform continues to grow in popularity, so too does the tendency among cybercriminals toward developing malware that targets it. Interestingly, though, until very recently (as in the last day or so), our researcher friends at Kaspersky Lab had never seen an Android SMS Trojan targeting users in the United States. That – of course – has now changed with the emergence of an Android Trojan known as ‘Trojan-SMS.AndroidOS.FakeInst.ef’ (FakeInst).
Oddly enough, in an email interview, Kaspersky Lab Expert Roman Unuchek explained that he has never really understood why SMS Trojans failed to take off in the U.S.
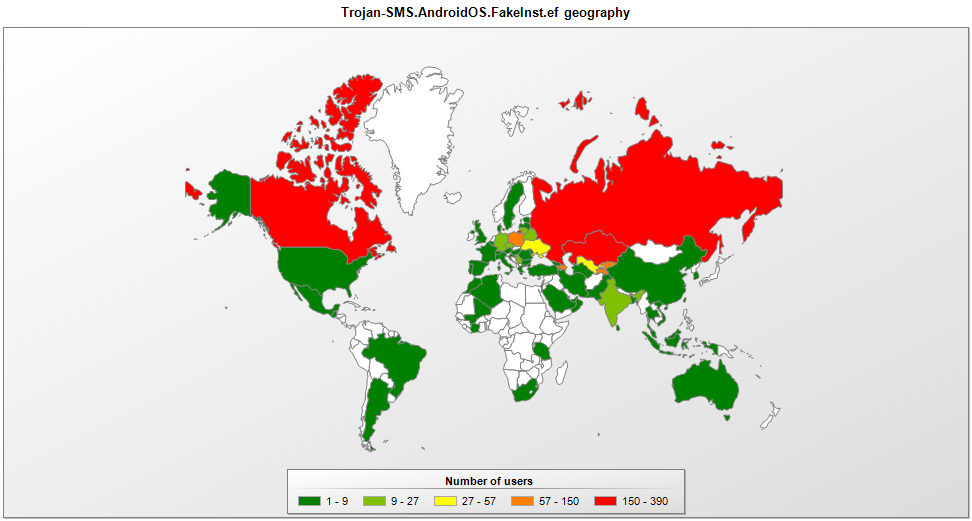
As if its status as the premiere SMS Trojan targeting Android users in the U.S. wasn’t enough, FakeInst is also targeting Android users in an additional 65 countries. As Unuchek notes, this is a mobile threat with global ambitions. In fact, FakeInst is known to have targeted users in Germany, France, Finland, Hong Kong, Ukraine, the U.K., Switzerland, Argentina, Spain, Poland, Canada, China, and many more nations.
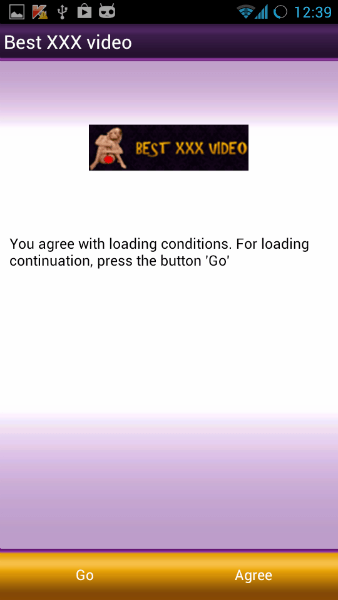
FakeInst is a malicious Android application whose purported use is to watch pornographic films. After a user downloads, installs, and opens the app, it then prompts that person to send a text message in order to purchase paid content from the app. Thanks to an extensive database, Fakeinst is able to send premium rate messages in 66 countries.
Inside Fakeinst, the first ever #Android Trojan which is able to steal from U.S. users by sending premium SMS. #Security
Tweet
When and if the user sends that text message, the Trojan will open an adult website – however, it’s a free site, which may be accessed directly and without any payments.
In the case of the United States, the Trojan will only send premium rate SMS messages to numbers that fall within the country’s mobile country code. FakeInst then sends three messages to the premium number – each message costing $1.99.
Perhaps even more seriously, the malicious application can also intercept, delete, and even respond to incoming text messages.
Unuchek believes the FakeInst was likely developed by cybercriminals in Russia.
As stated above, threats targeting the Android platform are increasingly commonplace, which comes as no surprise considering the open nature of the platform and its enormous popularity. Last year, Android malware designed to steal from bank accounts was somewhat novel. Now Android banking malware is increasing dramatically. If Android SMS Trojans targeting users in the U.S. follows the trend set by Android banking Trojans, then you should expect to see some more of these sorts of threats moving forward.
To avoid such threats and associated money loss, only install software from well-established marketplaces like Google Play and Amazon App Store, disable the (in)security option “Allow installation from unknown sources” and use dedicated mobile security solution.
 Android
Android


 Tips
Tips