With his family away at their country house, Eugene Kaspersky is enjoying solitary moments in his city apartment. He’s keeping busy spending (digital) face time with employees, customers, and partners. We caught up with him and other Kaspersky executives last week for a chat about how our industry is working through and even forging ahead during the pandemic.
How the COVID-19 pandemic has affected cybersecurity around the world
Eugene cut straight to the cybertalk. Unfortunately, he pointed out, the cyberthreat landscape hasn’t calmed down in the face of the pandemic; cybercriminals typically work from home anyway. With that in mind, we predicted early on that cybercrime would be more active while people are spending more time at home.
April turned out to be an unusually busy period for the threat landscape as many companies moved employees from working in the office to working from their homes — and cybercriminals found new ways to exploit the situation:
- Brute-force attacks on database servers in April 2020 were up 23% (Report: Cyberthreats on lockdown);
- Malicious files planted on websites increased by 8% in April (Report: Cyberthreats on lockdown);
- Network attacks and phishing e-mails rose (Report: spam and phishing in Q1 2020).
Eugene shared another interesting observation: Our data showed a decline in cybercriminal activity during the first two weeks of May. Were cybercriminals on holiday? A possibility that came up in discussion with our Global Research and Analysis Team was that cybercriminals were so successful in their campaigns that they were reaping what they sowed, turning stolen data into cash.
Of course, it’s always very important to stay safe and be aware. Even a relatively less-threatening landscape still holds danger, and you can bet cybercriminals will still jump on unpatched vulnerabilities and continue to hook folks with phishing, malicious e-mail attachments, and so forth.
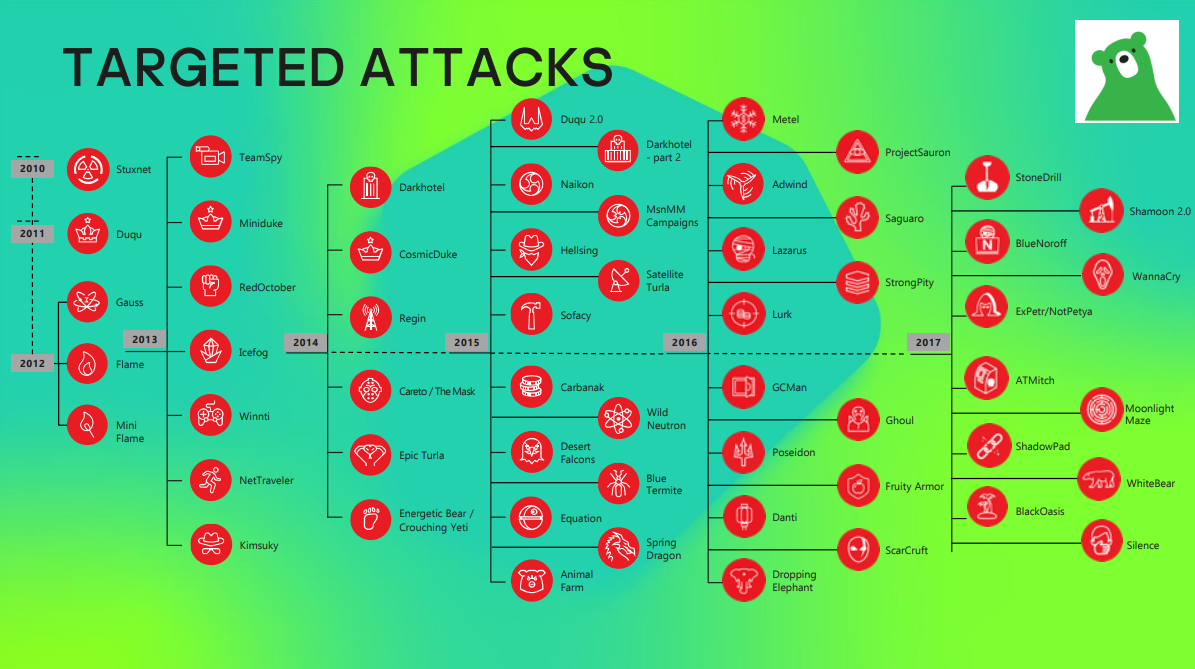
Lazarus under quarantine
Kurt Baumgartner, principal security researcher with Kaspersky’s Global Research and Analysis Team (GReAT), presented the next session, which focused on current Lazarus campaigns, an area GReAT monitors.
Lazarus’ destructive activities have been making headlines for quite some time now. In 2014, Kaspersky was one of the first public sources to share information on the malware used in the Sony Pictures Entertainment attack known as Destover.
The criminal activities don’t stop there. The threat group is also known for its financial attacks. Not only do Lazarus actors hack and steal from other cybercriminal groups, but they’ve also targeted casinos, cryptocurrency exchanges, and banks. In 2016, Lazarus made headlines again for attempting to wire itself almost a billion dollars from the Bangladesh Central Bank.
The group was also behind the WannaCry attack that delivered ransomware and caused unbelievable amounts of damage to networks and equipment around the world.
Recently, the United States Cyber Command (USCYBERCOM) tweeted about three malware families Lazarus is known for using. However, Baumgartner mentioned that those YARA rules were outdated — they were compiled between 2015 and 2018. Lazarus has updated its malware sets numerous times since 2018. Although this information is helpful to categorize, classify, and understand the advanced threat group, it isn’t particularly helpful to network defenders when it comes to defending against a future attack.
As a matter of fact, to stay ahead of cyberattacks, cybersecurity experts should subscribe to some sort of threat intelligence report. Through our Threat Intelligence Portal, you can find up-to-date monitoring and reporting — not only on Lazarus, but also on a number of other groups. You can find executive summaries, updated IOCs and YARA for malware in current use, and more in our threat intelligence reports.
Why employees stand between your business and the next cyberattack
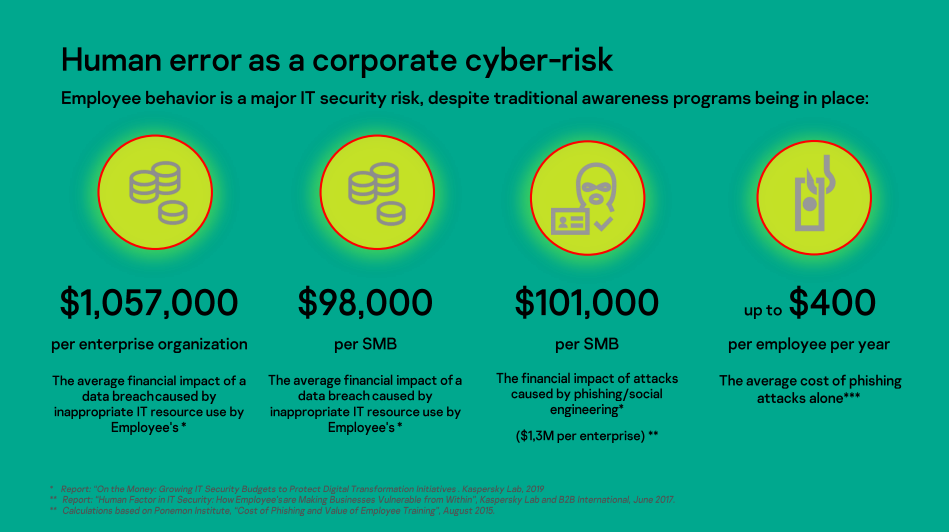
Moving on to the last session, Kaspersky North America Pre-Sales Manager Eric Payne discussed the cost of security incidents and data breaches related to human error.
The global workforce’s transition to remote work wasn’t easy. Companies had to make the decision abruptly in response to stay-at-home orders. Neither business leaders nor IT teams were given advance notice or much time to respond. And although some companies found the shift relatively easy, others had little to no experience with remote working and everything that comes along with it.
When employees work from home, companies have less control over IT security, especially when employees are not issued corporate devices. Although employees may be considered the weakest link, they are also the first line of defense, so when organizations try to bolster their defenses — i.e., make sure their employees are security-aware — they often look to traditional security awareness training programs. They will find several fundamental problems with such tools:
- Training takes too much time,
- Content is not engaging,
- Employees are not motivated to learn,
- Individual progress is not assured.
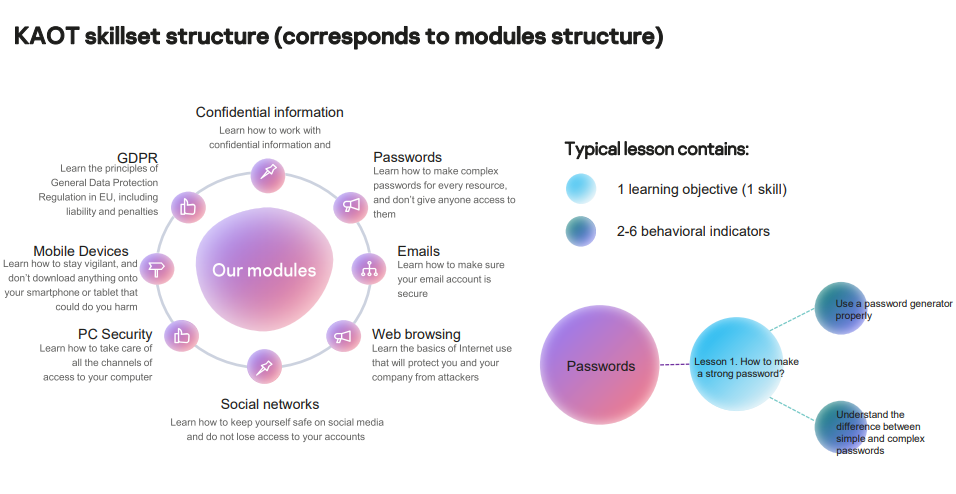 As a solution, Payne introduced adaptive online security training. Our new program, Kaspersky Adaptive Online Training meets a clear need, and you can read more about it here, but here are a few highlights:
As a solution, Payne introduced adaptive online security training. Our new program, Kaspersky Adaptive Online Training meets a clear need, and you can read more about it here, but here are a few highlights:
- Provides personalized learning for each participant,
- Reduces training time by up to 50%,
- Adapts to each participant’s level of knowledge,
- Ensures use of learned skills.
If you missed the webinar, or just want to see it again, watch the full replay here.
 webinar
webinar

 Tips
Tips