Advanced Persistent Threats, or APTs, are a pet subject for infosec experts to talk about, as such attacks usually employ the most sophisticated hacker tools. However, for common folks such threats are of no interest whatsoever.
To the general public, some of the most widely publicized attacks were like something from spy fiction. Until recently, APTs were not an issue to be concerned about, as the majority of APTs were targeting government organizations, with all details of investigations being highly confidential and real economic effect challenging to assess for obvious reasons.
#Stuxnet’s first 5 victims provided path to Natanz nuclear facility https://t.co/flHYwrU7Ws pic.twitter.com/pf5bSA2tBZ
— Eugene Kaspersky (@e_kaspersky) November 12, 2014
However, things are about to change: APTs inaugurated their presence in the commercial sector, or, to be more exact, in the banking sector. The results are pretty easy to assess: the loss due to an APT campaign targeting dozens of global financial institutions totaled $1 bln.
The vector of the attack
In order to infiltrate the bank’s intranet, the attackers used spear phishing emails, luring users to open them, infecting machines with malware. A backdoor was installed onto the victim’s PC based on the Carberp malicious code, which, in turn gave the name to the campaign — Carbanak.
After obtaining control over the compromised machine, cybecriminals used it as an entry point; they probed the bank’s intranet and infected other PCs to find out which of them could be used to access critical financial systems.
That done, the criminals studied the financial tools used by the banks, using keyloggers and stealth screenshot capabilities.
Then, to wrap up the scheme, the hackers withdrew funds, defining the most convenient methods on a case-by-case basis, whether using a SWIFT transfer or creating faux bank accounts with cash withdrawn by ‘mules’ or via a remote command to an ATM.
On average, it took from two to four months to drain each victim bank, starting from the Day 1 of infection to cash withdrawal.
Estimated loss
One way or another, the criminals stripped each victim bank of $2.5 mln to $10 mln – the amount looks striking even when assessed individually. Considering that dozens – up to one hundred – of organizations lost their funds due to the APT attack, the cumulative loss might well total to a stunning $1 bln.
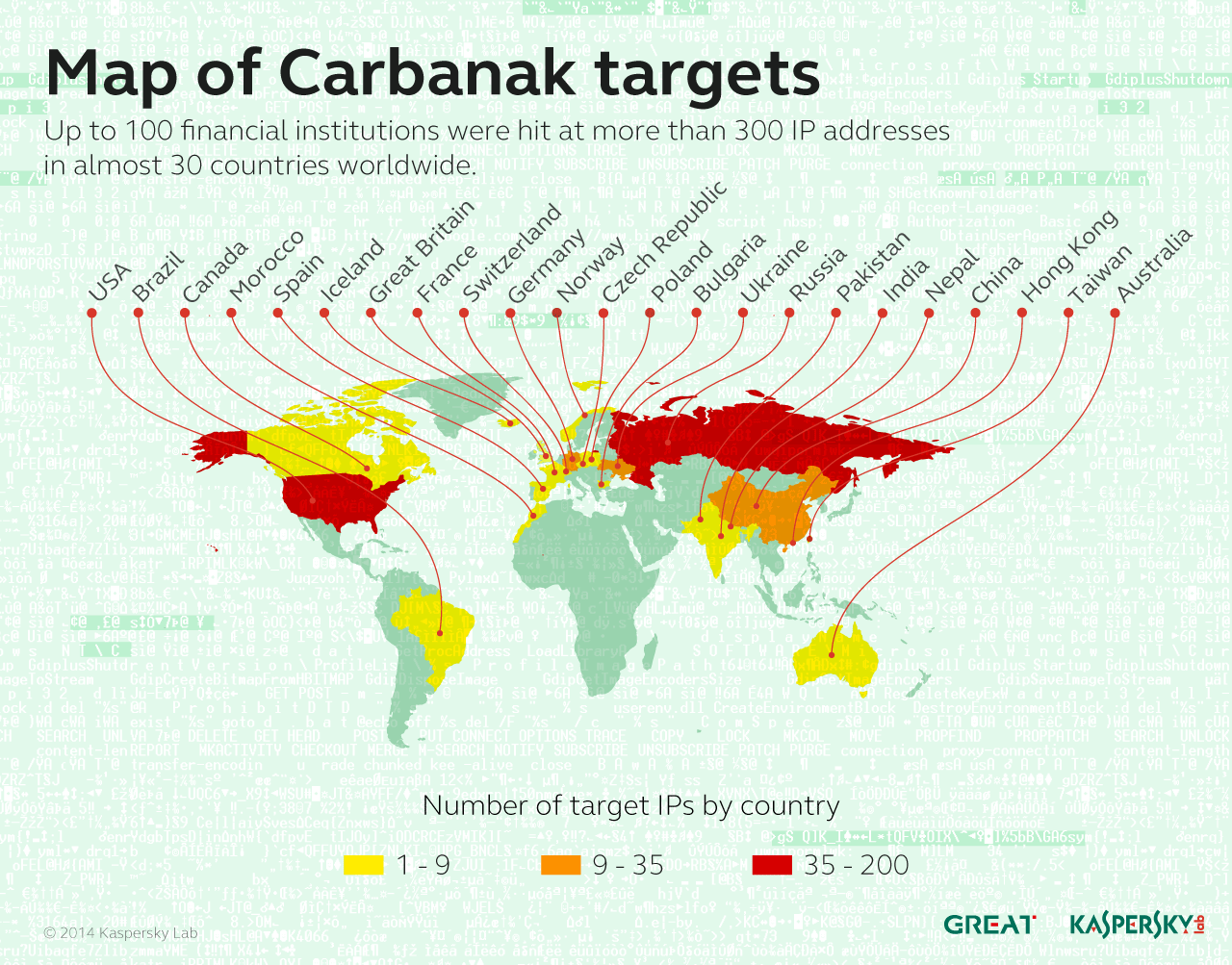
The countries which sustained severe losses due to the attack include Russia, USA, Germany, China, and Ukraine. Currently, Carbanak is expanding its operations to new locations, now present in Malaysia, Nepal, Kuwait and several African countries.
Based on the information from Kasperky Lab, the first samples of malware used by Carbanak were created back in August 2013. First cases of the infection date back to December 2013. First successful theft was registered in February to April 2014, with attacks peaking in June 2014.
Can ATMs get #malware infection & give away cash? Yes, here is a real case: https://t.co/xOzKZ0h3kz pic.twitter.com/4hb8NrbhYE
— Eugene Kaspersky (@e_kaspersky) October 7, 2014
Apparently, the attackers won’t stop until caught. Now, a number of both national cyber defense centers and international organizations, including Europol and Interpol, are involved into the investigation. Kaspersky’s Global Research and Analyst Team (GReAT) has also joined the effort.
How to protect against this threat?
Now, a piece of good news for our customers:
- All Kaspersky Lab enterprise products and solutions detect known samples of Carbanak malware as Backdoor.Win32.Carbanak and Backdoor.Win32.CarbanakCmd.
- In order to make sure your level of protection remains high, we recommend you to enable the proactive protection module which is included in all Kaspersky product versions.
In addition, we have a couple of tips to protect yourself from this and other security threats:
- Never open suspicious emails, especially those accompanied by an attachment.
- Regularly update the software you use. For instance, this very campaign did not employ zero-day vulnerabilities, but used known bugs, previously patched by vendors.
- Enable heuristic detection in your antivirus: this will increase the odds of the early detection of a malware sample.
You can find more information about the Carbanak campaign and our GReAT team investigation details in blog post at Securelist.
 APT
APT



 Tips
Tips