Updated October 9, 2018: Google has changed app permission settings in Android Oreo, adding a new group called “Special app access.” More details are available in “App permissions in Android 8: The complete guide.”
In the face of malware, Android has a very good defense mechanism — the app permissions system. This system defines a set of actions an app is allowed (or not allowed) to perform. By default, all Android apps work in a sandbox — an isolated environment. If they want to access, edit, or delete data outside the sandbox, they need the system’s permission to do so.
Permissions are divided into several categories, but we are going to discuss only two of them: normal and dangerous. Normal permissions cover such actions as accessing the Internet, icon creation, Bluetooth connection, and so forth. These permissions are granted by default and do not require a user’s approval.
If an app needs one of the “dangerous” permissions, user confirmation is required. So, why are some permissions deemed dangerous? Are they inherently, actually dangerous? And in which cases should you grant them?
Dangerous permissions
The “dangerous” category includes nine permission groups where apps are somehow connected with the user’s privacy or security. In turn, each group contains several permissions an app can request.
If a user approves one of the permissions, the app gets all of the permissions from the same group automatically, without additional confirmation. For example, if an app gets permission to read SMS messages, then it will be also able to send SMS messages, read MMS messages, and perform other operations from this group.
Calendar
What it permits:
- Read events stored in the calendar (READ_CALENDAR).
- Edit old events and create new ones (WRITE_CALENDAR).
Why it’s dangerous: If you actively use your digital day planner, the app will know everything about your daily routine and might share it with criminals. In addition, a buggy app could accidentally wipe important meetings from the calendar.
Camera
What it permits:
- Camera access (CAMERA) lets the app use your phone to take photos and record videos.
Why it’s dangerous: An app can secretly record video or take photos at any moment.
Contacts
What it permits:
- Read contacts (READ_CONTACTS).
- Edit contacts or add new ones (WRITE_CONTACTS).
- Access account list (GET_ACCOUNTS).
Why it’s dangerous: An app can snag your whole address book. This data is very attractive to spammers and fraudsters. This permission also grants access to the list of all of the accounts you use in the apps on this device — Google, Facebook, Instagram, and others like them.
Location
What it permits:
- Access to your approximate location (ACCESS_COARSE_LOCATION), provided based on data from cellular base stations and Wi-Fi hotspots.
- Access to your exact location (ACCESS_FINE_LOCATION), provided based on GPS data.
Why it’s dangerous: The app knows where you are at all times. It might, for example, let burglars know when you are far away from home.
Microphone
What it permits:
- Record audio from the microphone (RECORD_AUDIO).
Why it’s dangerous: The app can record everything that’s going on near your phone. All of your conversations. Not only when you’re speaking on the phone, but all day long.
Phone
What it permits:
- Reading phone state (READ_PHONE_STATE) lets the app know your phone number, current cellular network information, the status of any ongoing calls and so on.
- Make calls (CALL_PHONE).
- Read the list of calls (READ_CALL_LOG).
- Change the call list (WRITE_CALL_LOG).
- Add voicemail (ADD_VOICEMAIL).
- Use VoIP (USE_SIP).
- Process outgoing calls permission (PROCESS_OUTGOING_CALLS) lets the app see who’s calling, hang up the phone, or redirect it to another number.
Why it’s dangerous: When you grant phone permissions, you allow the app to take almost any action associated with voice communications. The app will know when and whom you call — and it can call anywhere, including paid numbers, at your charge.
Body Sensors
What it permits:
- (BODY_SENSORS) — this permission provides access to your health data from certain sensors, such as a heart-rate monitor.
Why it’s dangerous: If you use accessories with body sensors (not the phone’s built-in movement sensors), the app receives data about what is going on with your body.
SMS
What it permits:
- Send SMS messages (SEND_SMS).
- Read saved SMS messages (READ_SMS).
- Receive SMS messages (RECEIVE_SMS).
- Receive WAP push messages (RECEIVE_WAP_PUSH).
- Receive incoming MMS messages (RECEIVE_MMS).
Why it’s dangerous: It lets the app receive and read your incoming SMS messages as well as send them (charged to you, of course). For example, criminals can use this permission to subscribe victims to unwanted paid services.
Storage
What it permits:
- Read SD card or other storage (READ_EXTERNAL_STORAGE).
- Save records to storage or SD card (WRITE_EXTERNAL_STORAGE).
Why it’s dangerous: The app can read, change, or remove any files stored on your phone.
10 tips for maximum #Android #security – https://t.co/bIqSGMj05q pic.twitter.com/j0quFlYNnw
— Kaspersky (@kaspersky) November 7, 2014
How to set up app permissions
You should carefully consider each permission you grant. For example, if a game or photo-editing tool wants access to your current location, that’s strange. At the same time, maps and navigators really need GPS data — but not access to contact lists or SMS messages.
In Android 6 and later, apps ask users for approval any time they need one of the dangerous permissions. If you don’t want to grant them, you can always decline the request. Of course, if the app really needs those permissions, it will show error messages and won’t work properly.
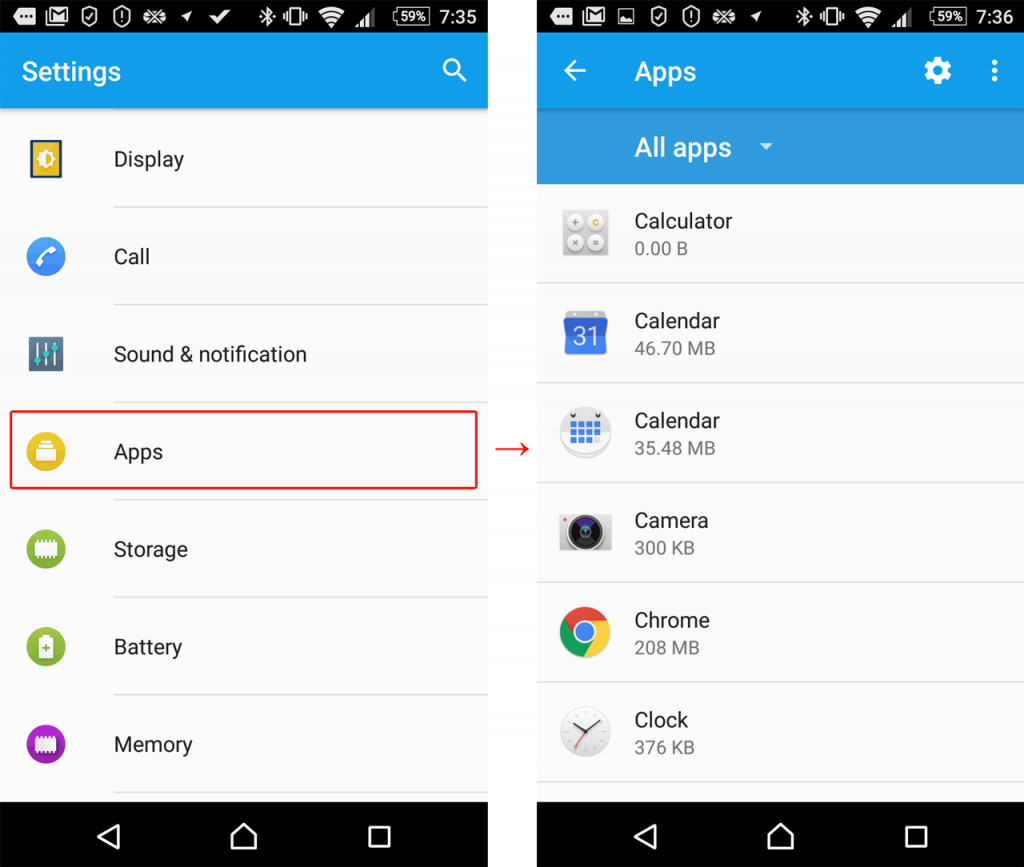
You can also check the permission list and change any app’s permissions. Start by choosing Settings → Apps (these and following menu items may have slightly different names in your version of Android).
Now you can go one of two ways. First, you can check all permissions assigned to a certain app. To do that, click on the app’s name and choose Permissions.
Second, you can look through the full list of apps that have already requested or can request one of the dangerous permissions. For example, it’s a good idea to check which apps want access to your contact list and prohibit suspicious ones from getting it. For this choose Configure Apps (the gear icon in the upper right corner) and then click App Permissions.
Special access rights
Apart from dangerous permissions, an app can also request special access rights. When that happens, you should be wary: Trojans often request such rights.
Accessibility
This permission simplifies work with apps and devices for people with sight or hearing difficulties. Malware can abuse these features.
Having obtained such access rights, Trojans can intercept data from apps (including input text — passwords are the main goal here). In addition, malware gets the ability to purchase apps in the Google Play Store.
Default messaging app
Banking Trojans aim to become the default SMS app; that lets them read SMS messages and hide them — even in later versions of Android. For example, Trojans can use this feature to intercept banking passwords from SMS messages and confirm malicious transactions without a user’s knowledge (remember, they can hide SMS messages).
Don’t trust the reviews and ratings on #GooglePlay https://t.co/3RHVVSkxOj #mobile #apps pic.twitter.com/z2pg7hqg2P
— Kaspersky (@kaspersky) September 1, 2016
Always on top
The permission to overlay windows of other apps lets Trojans show phishing windows on top of legitimate applications (mobile banks or social network apps mostly). Victims think they’re entering their passwords into the forms of real applications, but in fact everything happens in the fake window displayed by the Trojan, and sensitive data goes to criminals.
Device administrator privileges
These rights let the user change the password, lock the camera or wipe all data from the device. Malicious apps often try to get such permissions; apps with administrator privileges are hard to uninstall.

Root privileges
These are the most dangerous permissions. By default, Android never grants these rights to apps, but some Trojans can exploit system vulnerabilities to get them. Once that happens, all other defenses become useless — the malware can use root privileges to do whatever it wants no matter which permissions the victim assigns or denies.
It’s noteworthy that even the new permission system (released in Android 6) does not fully protect from malware. For example, the Gugi Trojan repeatedly bugs victims with window overlay permission requests until the permission is granted. After that, the malware overlays all other apps until it receives other permissions it wants.
Conclusions
Apps should not be allowed to do whatever they want on your phone — especially if they want dangerous permissions for no reason.
Some apps really do need a lot of rights, however. For example, antivirus programs need a lot of permissions to scan a system and proactively protect it from threats.
The conclusion here is simple: Before granting certain rights, think about if the app really needs them. If you’re not sure, do some investigating online.
400 Trojans on #Google #Play https://t.co/cNi1uBuZHo #mobile #malware pic.twitter.com/nDB5sYLCAE
— Kaspersky (@kaspersky) October 11, 2016
Last but not least: Even the most vigilant users are not safe from malware exploiting system vulnerabilities. That’s why it’s important to manage your apps’ permissions properly, which helps you protect your privacy from apps spying on you, and to install a reliable security solution that will defend your device against even more dangerous Trojans and viruses.
Updated October 9, 2018: Google has changed app permission settings in Android Oreo, adding a new group called “Special app access.” More details are available in “App permissions in Android 8: The complete guide.”
 android
android




 Tips
Tips