At the recent I/O 2024 developer conference in California, Google presented the second beta version of its Android 15 operating system — codenamed Vanilla Ice Cream. The company also gave us a closer look at the new security and privacy features coming with the update.
While the final release of Android 15 is still a few months away — slated for the third quarter of 2024 — we can already explore the new security features this operating system has in store for Android users.
AI-powered smartphone theft protection
The most significant security upgrade (but by no means the only one) is a suite of new features designed to protect against theft of the smartphone and the user data contained within. Google plans to make some of these features available not only in Android 15 but also for older versions of the operating system (starting with Android 10) through service updates.
First up is factory reset protection. To prevent thieves from wiping a stolen phone and quickly selling it, Android 15 will let you set up a lock that prevents resetting the device without the owner’s password.
Android 15 will also introduce a so-called “private space” for apps. Some apps like banking ones or instant messengers can be hidden and protected with an additional PIN code — preventing thieves from accessing sensitive data.
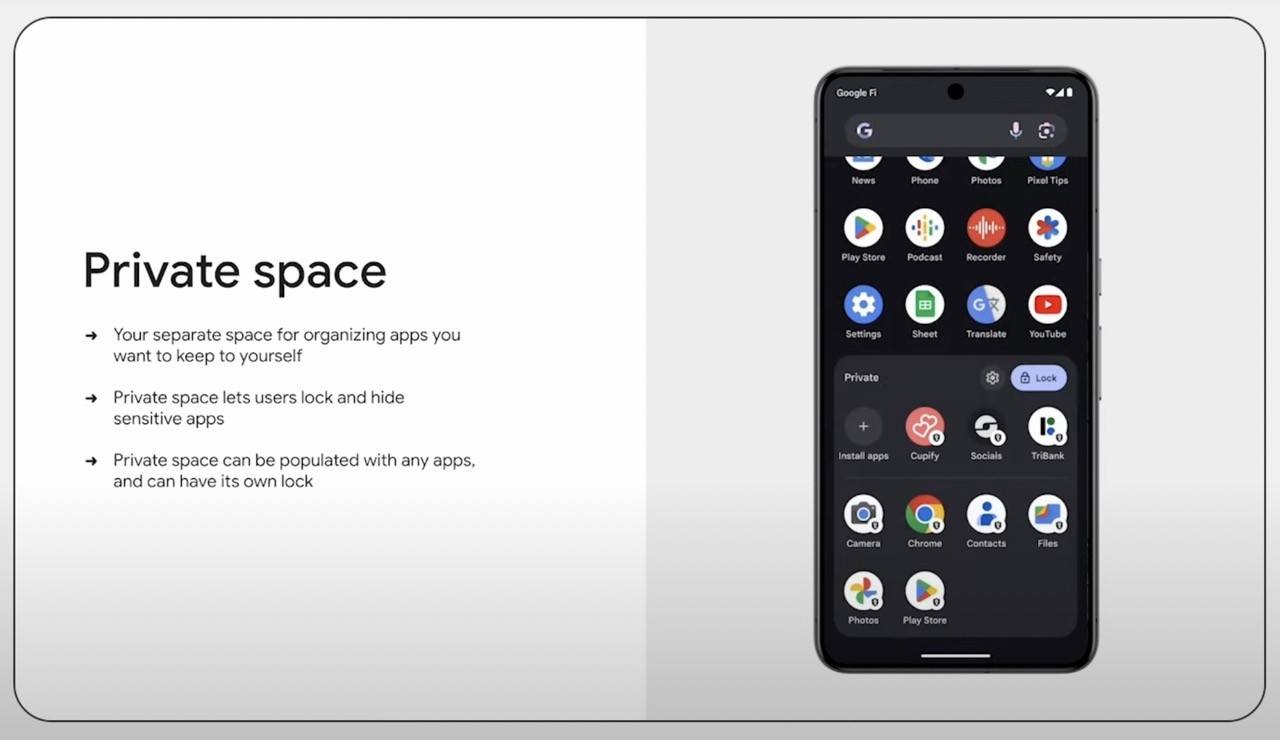
Android 15 will feature a “private space” to hide and protect selected apps with a separate PIN code
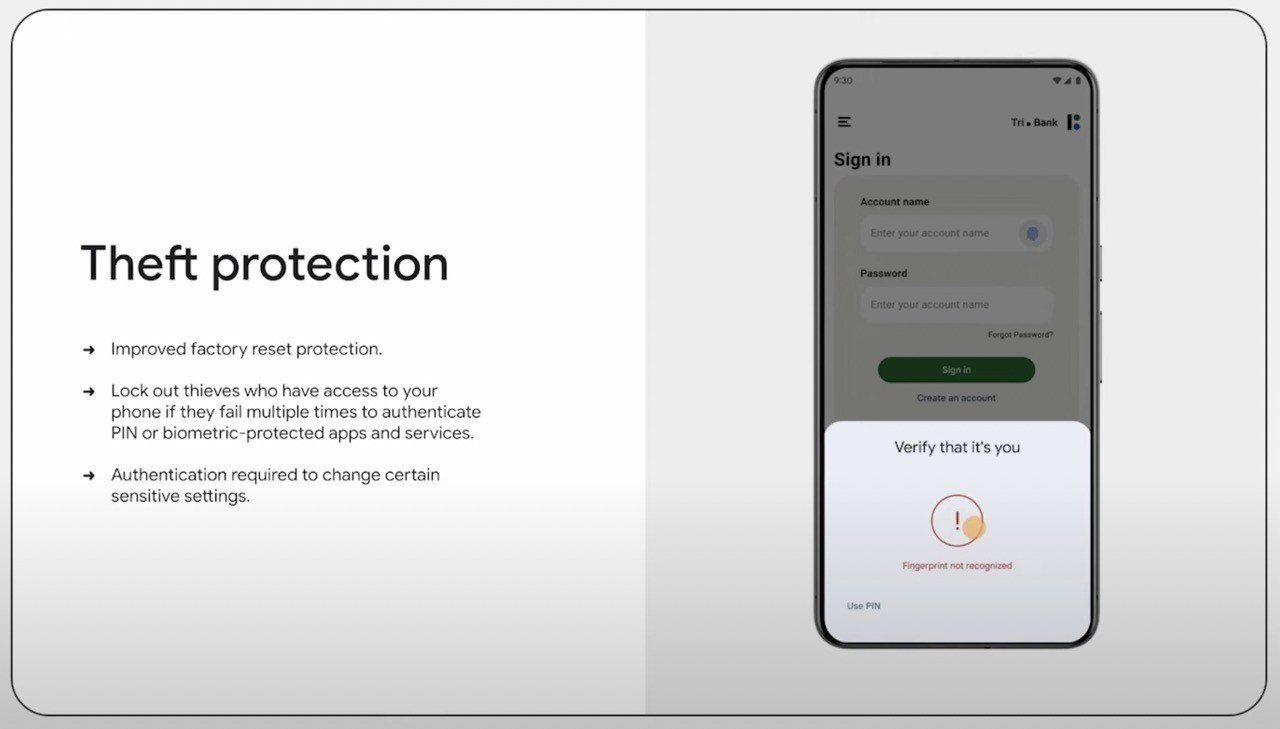
Furthermore, Google plans to add protection for the most critical settings in case a thief manages to get hold of an unlocked smartphone. Disabling Find My Device or changing the screen lock timeout will require authentication using a PIN, password, or biometrics.
But that’s not all: there’ll also be protection against thieves who’ve snooped on or otherwise obtained the PIN code. Accessing critical settings like changing the PIN, disabling anti-theft, or using passkeys will require biometric authentication. According to Google, this settings protection will be available on some devices “later this year”.
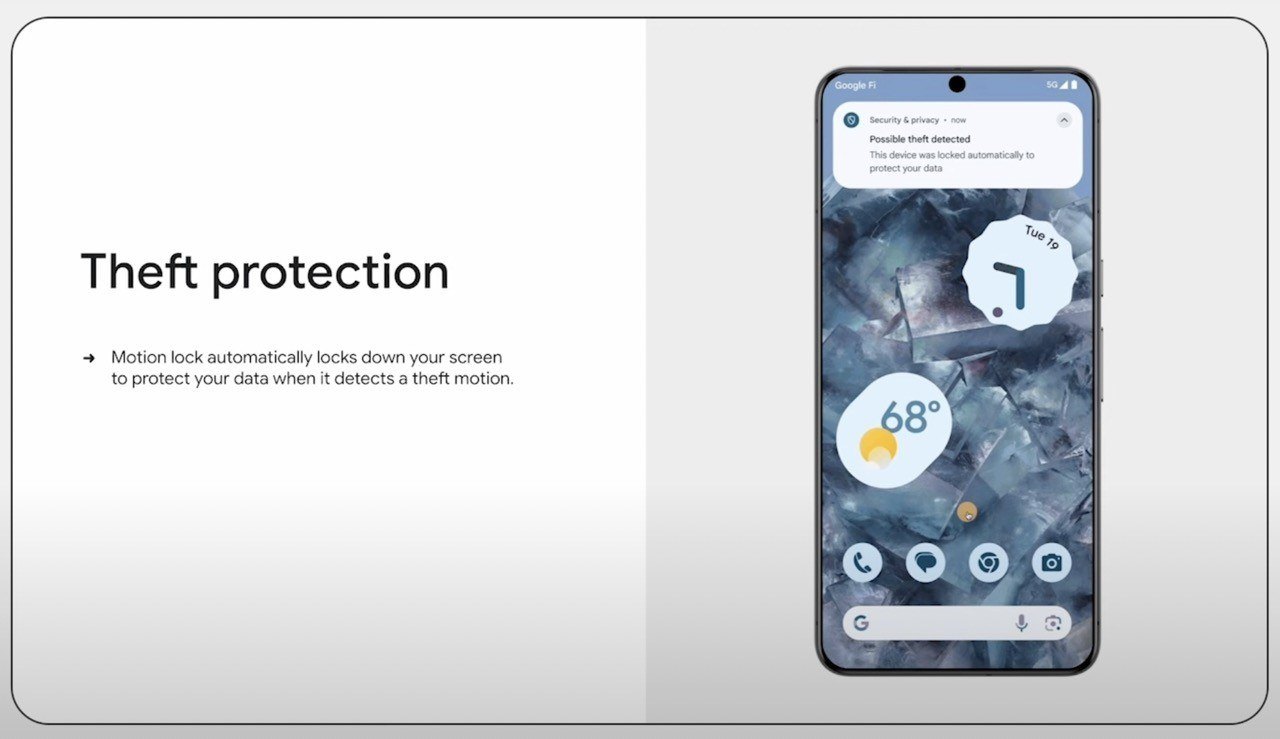
Now let’s talk about the new features that will be available not only in Android 15 but also in versions 10 and above. First, there’s AI-powered, accelerometer-based automatic screen locking. The screen will automatically lock if the system detects movements characteristic of someone snatching the phone and quickly running or driving away.
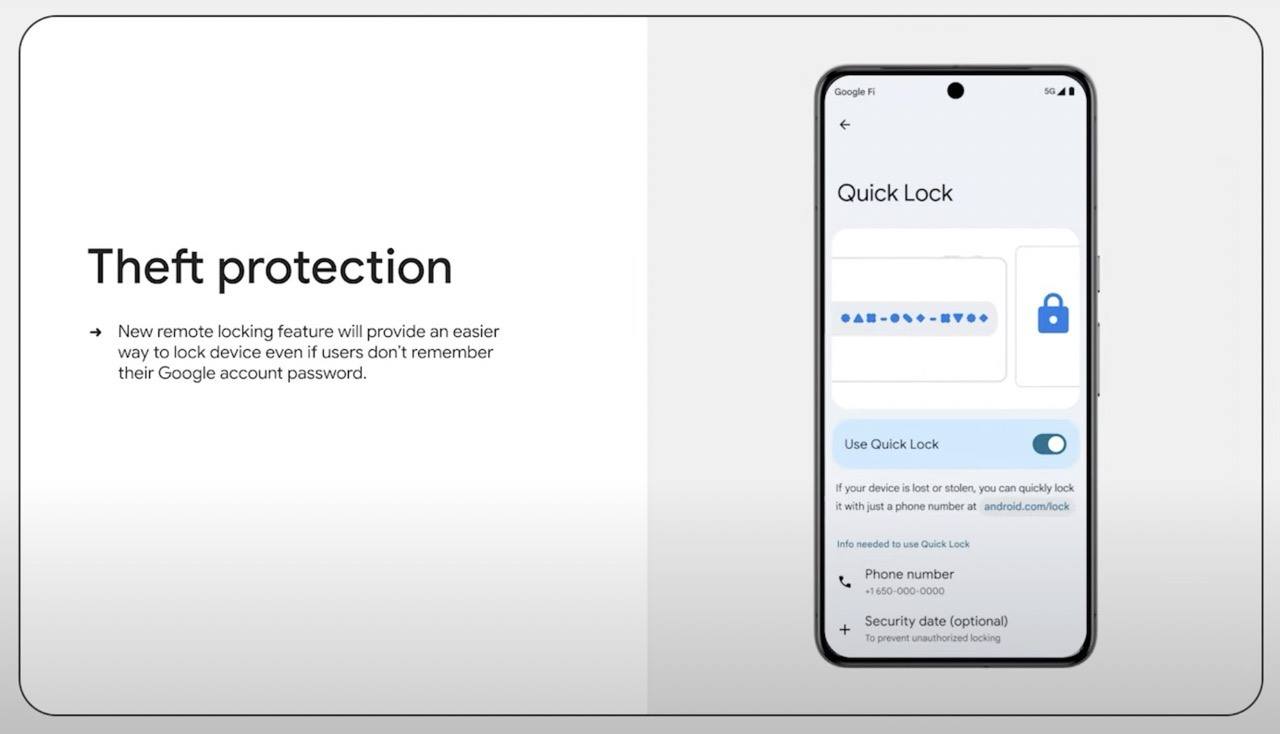
Additionally, the smartphone will automatically lock if a thief tries to keep it disconnected it from the internet for a long time. Automatic locking can also be set for other situations — for example, after a significant number of unsuccessful authentication attempts. Finally, Android will feature remote locking — allowing you to lock the phone’s screen from a different device.
Protection of personal data when screen sharing and recording
Android 15 also focuses on protecting user data from scams such as fake tech-support. Attackers might ask the user to share their screen (or record their actions and send a video) and instruct them to perform dangerous actions (such as logging in to an account). This way, scammers can obtain valuable information like login credentials, financial data, and so on.
First, screen sharing in Android 15 will (by default) only share the specific app the user is interacting with, and not the system interface (such as the status bar and notifications, which might contain personal information). But switching to full-screen sharing will still be possible if needed.
Second, regardless of the screen sharing mode, the system will only display notification content if the app developer has provided a special “public version” for it. Otherwise the content will be hidden.
Third, Android 15 will automatically detect and hide windows that contain one-time passwords. If a user opens an app window with a one-time password (for example, Messages) while sharing or recording their screen, the window contents won’t be displayed. Additionally, Android 15 will automatically hide login, password, and card data entered during screen sharing.
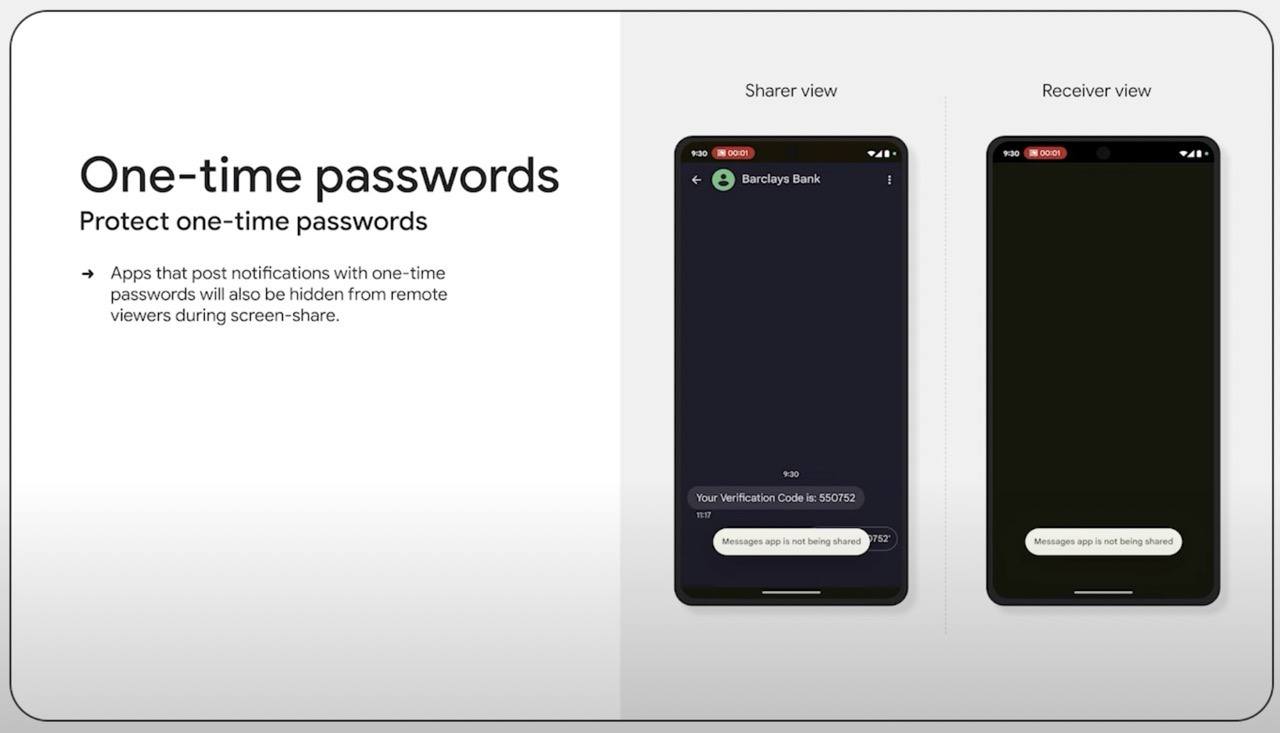
During screen sharing, Android 15 will automatically detect and hide windows containing one-time passwords
These measures protect not only against attackers specifically targeting user data, but also against accidental disclosure of personal information during screen sharing or recording.
Enhanced Restricted Settings
We’ve already discussed the so-called Restricted Settings that Android features from version 13 onward. This is additional protection against the misuse of two potentially dangerous features — access to notifications and Accessibility services.
You can read about the risks associated with these features at the link above. Here, let’s briefly recall the main idea of this protection: Restricted Settings prevent users from granting permission to these features for apps not downloaded from the app store.
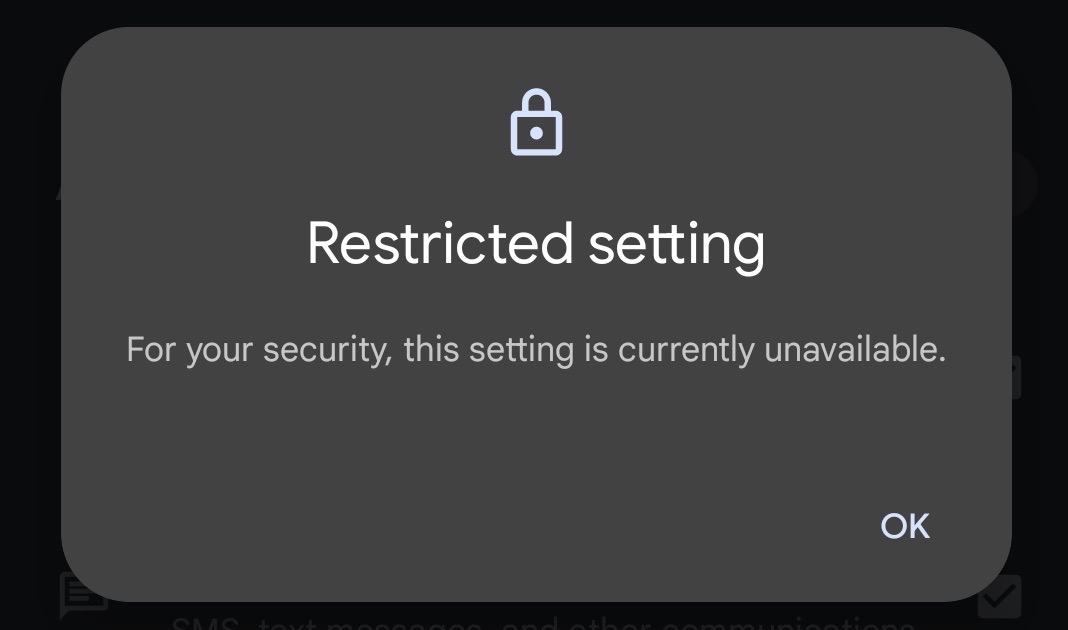
When a user tries to grant dangerous permissions to an app downloaded from outside the store, a window titled “Restricted Settings” appears
Unfortunately, in both Android 13 and 14, this protective mechanism is very easy to bypass. The problem is that the system determines whether an app was downloaded from the store or not by the method used to install it. This allows a malicious app downloaded from any source using an “incorrect” method to subsequently install another malicious app using the “correct” method.
As a result of this two-step process, the second app is no longer considered dangerous, isn’t subject to restrictions, and can both request and gain access to notifications and Accessibility services.
In Android 15, Google plans to use a slightly different mechanism called Enhanced Confirmation Mode. From the user’s perspective, nothing will change — the interface will function as before. However, “under the hood”, instead of checking the app installation method, this mechanism will refer to an XML file built into the operating system containing a list of trusted installers.
Simply put, Google is going to hardcode a list of safe sources for downloading apps. Apps downloaded from elsewhere will be automatically blocked from accessing notifications and Accessibility services. Whether this will close the loophole, we’ll find out after the official release of Android 15.
Protecting one-time codes in notifications
In addition to the improved Restricted Settings, Android 15 will feature additional protection against apps intercepting one-time passwords when accessing notifications from other apps.
Here’s how it works: when an app requests access to a notification, the operating system analyzes the notification and removes the one-time password from its contents before passing it to the app.
However, some app categories — for example, apps of wearables connected through the Companion Device Manager — will still have access to the full content of notifications. Therefore, malware creators may be able to exploit this loophole to continue intercepting one-time passwords.
Warnings about insecure cellular networks
Android 15 will also introduce new features to protect against attackers using malicious cellular base stations to intercept data or spy on smartphone owners.
Firstly, the operating system will warn users if their cellular connection is unencrypted — meaning their calls and text messages could be intercepted in plain text.
Secondly, Android 15 will notify users if a malicious base station or specialized tracking device is recording their location using their device ID (IMSI or IMEI). To do this, the operating system will monitor requests from the cellular network to these identifiers.
It should be noted that both these functions must be supported by the smartphone’s hardware. Therefore, they’re unlikely to appear on older devices upgraded to Android 15. Even among new models initially shipping with Vanilla Ice Cream, probably not all will support these features — it’ll be up to the smartphone manufacturers whether to implement these functions or not.
New app protection features
Next up in the Android 15 security enhancements are improvements to the Play Integrity API. This service allows Android app developers to identify fraudulent activity within their apps, as well as instances where the user is at risk, and use various additional security measures in such cases.
In particular, in Android 15, app developers will be able to check if another app is running simultaneously with their app and recording the screen, displaying its windows on top of their app’s interface, or controlling the device on behalf of the user. If such threats are detected, developers can, for example, hide certain information or warn the user about the threat.
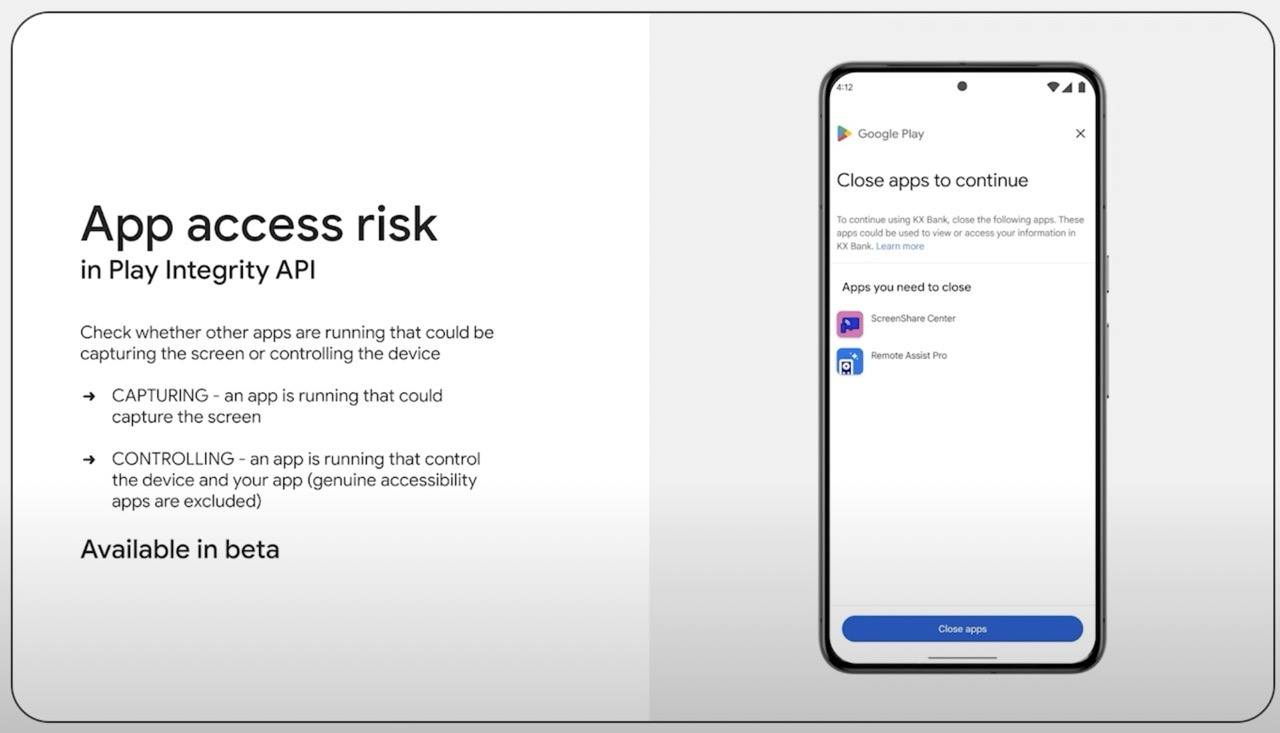
Play Integrity API enables app developers to detect malicious activity and take steps to mitigate threats
Developers will also be able to check if Google Play Protect is running on the device and if any known malware has been detected in the system. Again, if a threat is detected, the app can restrict certain actions, request additional confirmation from the user, and so on.
On-device Google Play Protect
Finally, another security innovation in Android 15 is that Google Play Protect will now operate not only within the official Google Play app store but also directly on user devices. Google calls this “live threat detection”.
The operating system (with the help of AI) will analyze app behavior — in particular, the use of dangerous permissions and interaction with other apps and services. If potentially dangerous behavior is detected, the app will be sent to Google Cloud for review.
Does this mean you can now ditch your third-party antivirus for Android? Not so fast, tiger. Ultimately, the effectiveness of anti-malware protection depends on how thoroughly a vendor can search for and study new threats.
Automation is certainly important here — that’s why we started using machine learning for threat research many years ago, long before it became trendy. But the work of human experts is equally crucial. And on this score, as numerous cases of malware infiltrating Google Play demonstrate, Google is still not doing so well — often lacking the resources to solve this problem.
Therefore, we recommend usinga comprehensive security solution on all your Android devices — including those running Android 15. It’ll complement perfectly the new privacy and security features. Moreover, much of what will only be introduced in the upcoming update — for example the functions for theft protection, finding your device, or protecting individual apps with a PIN — we implemented a long time ago and support even on older versions of Android. Check out this detailed review of the most interesting features in Kaspersky for Android. You can also set up your Android privacy and security settings using the Privacy Checker.
 Android
Android


 Tips
Tips