
Money for Nothing
During the pre-holiday period, attackers are sending invoices to companies for the delivery of non-existent documents.
3313 articles

During the pre-holiday period, attackers are sending invoices to companies for the delivery of non-existent documents.

Methods used by attackers to redirect victims to malicious and phishing sites from seemingly safe URLs.

A researcher has discovered a vulnerability in the Bluetooth protocol implementations for Android, macOS, iOS, and Linux, allowing devices to be hacked remotely.

Are Macs as safe as their owners think they are? A few recent stories about malware targeting macOS users.

Episode 327of the Kaspersky podcast looks at hackers targeting travellers, UK government stiffens adult content laws & an interview with Vidit Gujrathi, chess Grand Master on technology and chess.

Cybercriminals send the Remcos remote-access trojan under the guise of letters from a new client.

Android 13 and 14 have a feature called Restricted Settings. We explain its purpose, and how malicious applications bypass it.

Unused apps not only clutter your phone but also create a risk of personal data leakage, so it’s better to remove them. But what if an app can’t be uninstalled? There’s a workaround.

Typical security issues of WordPress, and how they can be addressed to protect your website or online store from cybercriminals.

Episode 326 of the Kasperksy podcast looks at data breaches, US police return $9M from hackers, homes in limbo after cyber-attack and more!

Bitcoin wallets created on online platforms between 2011 and 2015 may be insecure due to a vulnerability in the library for key generation.

Espionage operations to hack corporate routers are now commonplace — and all organizations need to be aware of this.
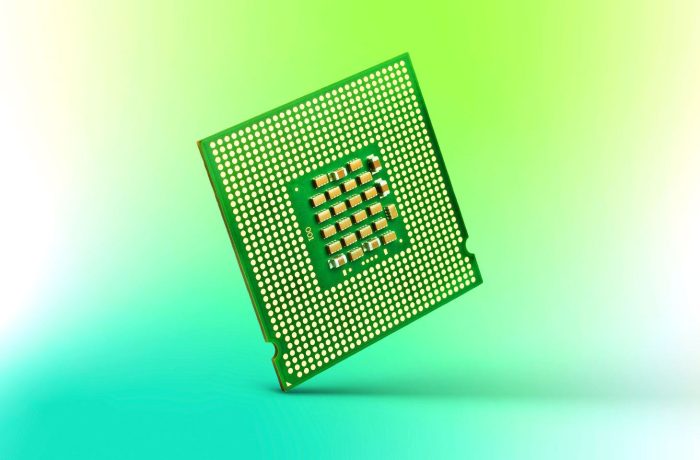
How a recently discovered bug in Intel processors threatens cloud providers.

The Nothing Chats app from Nothing Phone promised to be the iMessage for Android, but in less than 24 hours it was removed from Google Play due to a shocking lack of security.

A look at the pros and cons of updating Android — and ways to do it safely.

Episode 325 of the Kaspersky podcast looks at AI generated music, hacker arrested for helping drug dealers & more.

How attackers use infected archives and malicious browser extensions to steal Facebook Business accounts.

Episode 324 of the Kaspersky podcast looks at Meta and Google in the docks, more on deep-fakes & port operator pulls internet after a cyberattack.

Our researchers discovered spyware-infected WhatsApp modifications distributed through Telegram channels and websites with WhatsApp mods.

We discuss what zero-click attacks are, why they’re dangerous, and how to protect your company from them.

Cyber-hygiene is crucial, but employees at small businesses are having a hard time changing their old habits. Why?